Guide to Hybrid Cloud Deployment Security
Summarize this article with:
✨ AI Generated Summary
Hybrid cloud security dissolves traditional perimeters, expanding attack surfaces due to fragmented IAM, inconsistent encryption, and limited visibility across on-premises and cloud environments. Effective security relies on architectural principles including:
- Separate control and data planes with outbound-only networking to limit lateral movement
- Federated identity management and runtime secret fetching from external vaults
- Immutable centralized logging and security policies defined as code for continuous compliance
Airbyte Enterprise Flex exemplifies this approach by separating orchestration from data processing, enforcing outbound-only connectivity, and enabling customer-controlled credentials and centralized monitoring, ensuring scalable, compliant hybrid cloud deployments.
As you mix public-cloud agility with on-premises resilience, your security perimeter disappears. Each workload now spans different trust domains, vendors, and regulatory zones. The shared-responsibility boundaries you once relied on no longer apply.
This complexity creates an expanded attack surface. Fragmented IAM, inconsistent encryption, and limited observability expose gaps that traditional perimeter defenses can't address. Hybrid environments merge on-premises and public services, so a misconfiguration in one environment can compromise your entire stack.
Effective hybrid security means protecting every workload, credential, and dataset across these interconnected yet separately governed domains. The foundation is architectural: unified control planes, regional data execution, and outbound-only networking. This approach keeps orchestration centralized while maintaining data sovereignty.
What Are the Main Security Risks in Hybrid Cloud Deployments?
Multi-environment deployments string together on-premises systems and multiple clouds, so you inherit every hazard of each environment plus new gaps created at the seams. Fragmented identity stacks leave roles defined in Active Directory, AWS IAM, and SaaS platforms out of sync, making privilege creep and orphaned accounts routine. Open network bridges and VPN tunnels required for cross-environment traffic can expose management interfaces that attackers probe for lateral movement.
Credential reuse compounds the problem. Static tokens or hard-coded service accounts often flow between systems, so a single leak grants broad access. Each region may handle data under different rules, causing compliance drift that auditors flag as soon as records leave an approved jurisdiction. Visibility is just as uneven. Logs live in multiple silos, delaying incident response and masking indicators of compromise. Rapid CI/CD pipelines often outpace change control, so misconfigurations like public buckets and permissive security groups slip into production before anyone notices.
These vulnerabilities create a clear pattern of risk areas across hybrid environments:
These weaknesses multiply the attack surface. Traditional single-domain security built around a clear perimeter and one IAM store can't keep pace with the fluid boundaries, overlapping trust zones, and constant change that define multi-environment operations.
How Can Architecture Strengthen Hybrid Cloud Deployment Security?
Security in a multi-cloud environment succeeds or fails at the architectural layer. You can't bolt it on later and hope for the best. By designing each layer to assume breach and minimize trust, you dramatically cut the pathways attackers can exploit while keeping operations predictable for your team.
Five architectural pillars work together to create consistent protection:
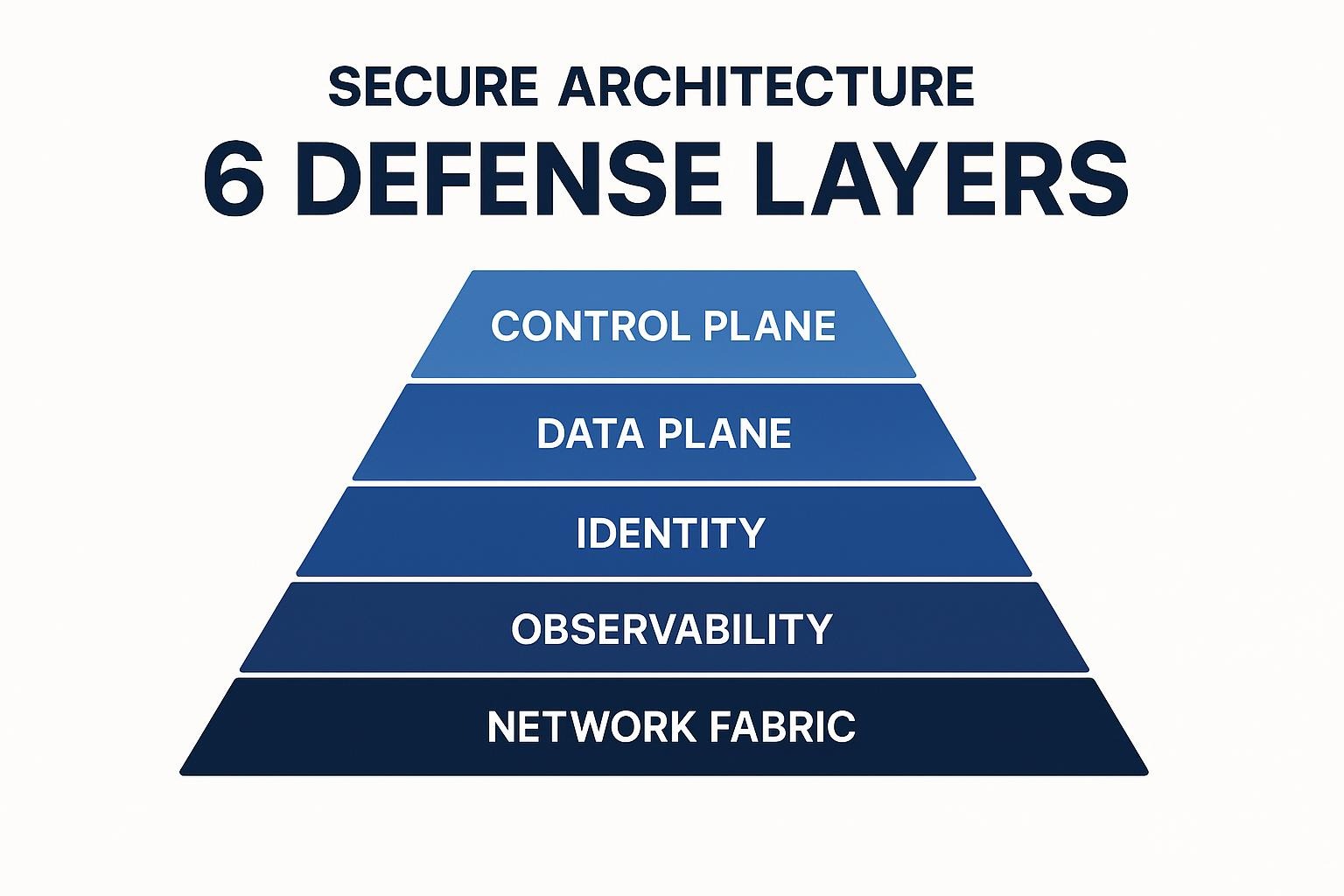
- Separate control plane and data plane: When orchestration lives in a dedicated management tier and data stays local to each region, a compromise of one plane can't automatically pivot into the other. This gives you two distinct blast radii.
- Adopt outbound-only networking: Every data-plane component dials out to fetch jobs or push metrics instead of opening inbound ports. Firewalls become simpler, lateral movement gets limited, and security reviews focus on a single egress path rather than sprawling ACL matrices.
- Unify access with federated identity: A single authentication backbone maps roles consistently across on-premises, AWS, Azure, and SaaS. You deprovision once, enforce MFA everywhere, and eliminate the "shadow admin" accounts that thrive in fragmented IAM stores.
- Fetch credentials from external secrets managers: Storing secrets alongside code or images invites leakage. Fetching them just-in-time from HashiCorp Vault or AWS Secrets Manager keeps rotation painless and audit trails complete.
- Capture everything through tamper-evident logging: Immutable logs (ideally hashed and shipped to a write-once store) let you reconstruct incidents without worrying that an attacker wiped their footprints.
These pillars deliver reduced attack surface, least-privilege enforcement, verifiable evidence, and architectures ready for zero-trust expansion rather than expensive retrofits.
What Are the Best Practices for Securing Hybrid Cloud Deployments?
Multi-environment deployments reward clear, repeatable processes. The fastest way to shrink your attack surface is to standardize security controls everywhere workloads run, then let automation keep them in sync as the stack evolves.
1. Federate Identity Under One Source of Truth
The foundation starts with federating identity under one source of truth. A single directory backed by SAML, OIDC, or OAuth lets you map roles once and have them honored across data centers and clouds. This eliminates orphaned accounts and privilege drift that identity sprawl creates. When your authentication flows through a central hub, you can track access patterns and spot anomalies that would otherwise hide in fragmented systems.
2. Prioritize Outbound-Only Network Architecture
Network architecture should prioritize keeping traffic outbound-only wherever possible. Architect sync jobs, management APIs, and monitoring agents to dial out instead of accepting inbound calls. Firewalls can then default-deny unsolicited traffic, cutting lateral movement opportunities in half. This approach transforms your perimeter from a collection of exposed entry points into a series of controlled outbound connections that you fully own.
3. Pull Secrets at Runtime from External Vaults
Credential management demands pulling secrets at runtime from an external vault rather than embedding them in configurations. HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault stores credentials centrally, rotates them automatically, and supplies short-lived tokens only when workloads request them. This removes static keys from repos and ticket systems, where they tend to accumulate and become forgotten attack vectors.
4. Define Security Policy as Code
Security policy works best when defined as code rather than manual procedures. Express network rules, IAM bindings, and compliance controls in Git-tracked files. Continuous-integration hooks can block non-compliant changes before they reach production and auto-remediate drift in live systems. This approach means your security posture stays consistent even as teams deploy new services and modify existing ones.
5. Stream All Logs to One Analytics Pipeline
Visibility requires streaming every log to one analytics pipeline. Central aggregation (whether a SIEM or a data lake) lets you correlate events across clouds and on-premises servers, spot anomalies quickly, and hand auditors provable evidence on demand. Without unified logging, distributed environments become forensic nightmares where critical evidence gets scattered across incompatible systems.
Secure operations depend less on a bigger tool catalog than on architectural discipline. When you codify roles, routes, secrets, and policies once and let machines enforce them, you trade heroic out-of-band fixes for predictable, audit-ready pipelines that scale with every new region you deploy.
How Does Secure Architecture Look in Practice?
Resilient multi-cloud stacks layer security in deliberate tiers, each one insulating the next. The control plane (your orchestration APIs and schedulers) lives apart from the data plane where records are processed and stored. By isolating management traffic, a breach in workload code never grants an attacker administrative reach.
This layered approach creates distinct security boundaries that work together:
These layers cooperate to enforce zero-trust fundamentals. Never trust a request merely because it originates "inside," always authenticate and authorize it first. When a retail dataset syncs from an on-premises warehouse to a cloud analytics cluster, the data plane initiates an encrypted, outbound channel. The control plane only schedules the job, and credentials are fetched moment-to-moment from your vault. Even if an attacker compromises the sync container, they meet segmented networks, expiring tokens, and a control plane that's walled off behind MFA. Defense in depth by design, not afterthought.
How Does Airbyte Enterprise Flex Deliver Secure Hybrid Architecture?

Airbyte Enterprise Flex separates orchestration from data processing, implementing the secure architectural patterns discussed above. The cloud-managed control plane handles scheduling and pipeline state, while patient, payment, and product data remains in your customer-run data plane, whether deployed in on-premises Kubernetes clusters or locked-down VPCs.
Key security features include:
- Outbound-only connectivity: The data plane initiates all traffic outbound, so firewalls only require outbound rules, eliminating inbound attack vectors
- Customer-controlled credentials: Flex pulls secrets just-in-time from HashiCorp Vault or AWS Secrets Manager, ensuring keys never leave your infrastructure
- Centralized visibility with data sovereignty: Job metadata, metrics, and logs stream to the control plane for unified monitoring without exposing underlying records
- Consistent connector quality: The architecture scales horizontally across regions while maintaining the same 600+ connectors in every deployment
A U.S. healthcare network demonstrates this approach in practice. They needed to join on-premises EHR data with cloud-based analytics while maintaining HIPAA compliance. By deploying a Flex data plane inside their data center, they sync tables outbound to a HIPAA-eligible warehouse, generate immutable local audit logs for compliance verification, and achieve sub-minute SLA requirements. No VPN backhauls, no custom agents, and no protected health information leaves their controlled environment.
Why Is Continuous Compliance Essential for Hybrid Security?
Multi-environment infrastructure never sits still. You add connectors, shift workloads, and spin up short-lived resources every day. If you wait for an annual audit, gaps appear the moment a new microservice lands in production. By weaving compliance controls into daily operations, you keep pace with that change and avoid the "surprise" findings that derail releases. The goal is true continuous compliance: policies that evaluate themselves automatically whenever the environment evolves.
You achieve that by treating compliance as code, not paperwork. Tools track every asset, compare its state to rule baselines, and trigger fixes the instant drift occurs. Central dashboards pull data from on-premises and cloud so you can prove posture at any moment (no frantic screenshot hunt required).
Effective continuous compliance requires several key practices:
- Automate drift detection and remediation so misconfigurations are corrected before attackers notice
- Set up regular credential rotation to shorten the window for stolen secrets
- Review immutable audit logs monthly to catch subtle privilege misuse
- Standardize monitoring dashboards across all regions for a consistent view of risk
Continuous compliance isn't a phase. It's a feedback loop that strengthens security every time your distributed stack changes. Evidence collection and policy-as-code turn audits into standard checkpoints rather than fire drills.
How Do You Build Hybrid Cloud Security That Scales?
Architecture, not tools, determines whether your multi-environment deployment stays secure as it grows. Separate orchestration from the data plane, keep credentials in external vaults, and use outbound-only connectivity. Talk to sales to see how Airbyte Enterprise Flex delivers cloud control with customer-controlled data planes across 600+ connectors.
Frequently Asked Questions
How does hybrid cloud security differ from traditional on-premises security?
Hybrid cloud security requires protecting workloads across multiple trust domains instead of a single perimeter. You need unified identity management across different platforms, consistent encryption standards, and centralized logging that spans on-premises and cloud environments. Traditional perimeter defenses fail because there's no longer a clear boundary to defend.
What's the most common security mistake in hybrid cloud deployments?
Opening inbound network paths between environments creates the largest attack surface. Teams often add VPN tunnels or expose management APIs to enable cross-environment traffic, giving attackers lateral movement opportunities. Outbound-only connectivity where data planes dial out to fetch jobs eliminates most of this risk.
How do you maintain compliance across multiple cloud regions?
Compliance requires keeping data local to approved jurisdictions while maintaining centralized visibility. Deploy regional data planes that process records within their geographic boundaries, stream only metadata and logs to central monitoring, and use policy-as-code to enforce consistent controls across all regions automatically.
Can you use the same security tools for hybrid and cloud-only deployments?
Yes, if you architect properly. Use federated identity management that works across all environments, secrets managers that integrate with both on-premises and cloud infrastructure, and logging pipelines that aggregate from any source. The key is choosing tools that don't assume a single deployment model.

.webp)
