How to Sync Two MySQL Databases Using Airbyte?
Summarize this article with:
✨ AI Generated Summary
MySQL synchronization is crucial for ensuring data availability, performance, and security in distributed environments, with methods ranging from one-time sync for migrations to continuous sync for real-time replication. Airbyte offers a no-code, scalable platform with 600+ connectors that simplifies synchronization across cloud, hybrid, and on-premises setups, while manual methods provide granular control for complex or compliance-driven needs. Advanced techniques like Change Data Capture (CDC) and GTID replication enhance real-time processing and multi-master configurations, supported by robust security practices including encryption, access control, and compliance frameworks.
- One-time sync suits migrations and periodic backups; continuous sync supports real-time data replication using MySQL binary logs.
- Airbyte enables easy setup, granular data selection, and secure synchronization with enterprise-grade monitoring and governance.
- Manual sync offers deep customization via master-slave replication but requires expert knowledge and careful configuration.
- Advanced methods like CDC and GTID improve scalability, failover, and consistency in complex architectures.
- Security involves encryption (TDE, SSL/TLS), role-based access, and compliance with GDPR, HIPAA, PCI-DSS.
- Use cases include disaster recovery, development/testing environments, and analytics workloads with optimized performance.
MySQL synchronization has become essential for modern organizations managing distributed database environments. Despite MySQL's widespread adoption as one of the leading relational database management systems, enterprises face critical challenges ensuring continuous data availability while maintaining performance and security across complex infrastructures.
A single hour of database downtime can result in significant financial losses, damaged customer relationships, and regulatory compliance failures. This reality has driven widespread adoption of MySQL synchronization strategies that extend far beyond simple backup solutions.
This comprehensive guide explores how to implement effective MySQL synchronization using Airbyte's modern [data integration](https://airbyte.com/blog/data-integration) platform, alongside traditional manual methods and advanced techniques that address today's complex infrastructure requirements.
What Are the Different Types of MySQL Synchronization Available?
MySQL synchronization strategies have evolved to address diverse organizational needs, from simple data backup scenarios to complex real-time analytics architectures. Understanding these approaches enables you to select the optimal synchronization method based on your specific requirements for data consistency, performance, and operational complexity.
One-Time Synchronization
One-time sync involves replicating data between MySQL databases in a single operation without maintaining ongoing connections for future updates. This approach proves particularly valuable for data migration projects, initial system setups, or applications that require periodic bulk data transfers rather than continuous updates.
Organizations commonly implement one-time synchronization for development environment refreshes, where production data snapshots provide realistic testing scenarios without requiring real-time updates. This method also supports compliance requirements where historical data must be transferred to archival systems at specific intervals while maintaining data integrity and audit trails.
The implementation of one-time synchronization requires careful planning around data consistency points, ensuring that snapshot captures represent coherent system states. Modern tools like Airbyte optimize this process through intelligent batching mechanisms that minimize resource consumption while maintaining data integrity throughout the transfer process.
Continuous Synchronization
Continuous sync maintains persistent connections between source and target MySQL databases, enabling real-time or near-real-time data propagation as changes occur in the source system. This approach forms the backbone of high-availability architectures, real-time analytics platforms, and disaster recovery implementations that cannot tolerate significant data lag.
The technical implementation of continuous synchronization leverages MySQL's binary logging capabilities to capture all data modification operations as they occur. This enables precise replication of INSERT, UPDATE, and DELETE operations across multiple target systems. Advanced continuous synchronization platforms utilize Change Data Capture technologies that monitor binary logs without impacting source database performance.
Modern continuous synchronization implementations support sophisticated routing and transformation capabilities. This enables organizations to maintain multiple synchronized copies with different schema structures or data subsets. This flexibility proves essential in complex architectures where different downstream systems require customized views of the same source data while maintaining consistency guarantees.
How Can You Sync MySQL Databases Using Airbyte?
Airbyte has emerged as a leading data integration platform with strong no-code capabilities, offering 600+ pre-built connectors that enable seamless data movement between various sources and destinations. This includes comprehensive support for SQL-based databases. When specific connectors are unavailable, Airbyte provides a Connector Builder and Connector Development Kits for rapid custom connector development.
The platform's architecture addresses fundamental challenges in database synchronization by combining enterprise-grade security features with deployment flexibility across cloud, hybrid, and on-premises environments. This approach eliminates the traditional trade-offs between ease of use and technical control that have historically limited synchronization platform adoption.
Step 1: Connect Your MySQL Database as Source
Begin by accessing Airbyte Cloud through the login portal or creating a new account if you're a first-time user. Navigate to the Sources section and use the search functionality to locate the MySQL connector from Airbyte's extensive connector library.

The source configuration process requires comprehensive database connection details including the Host address, Port number (typically 3306 for MySQL), authenticated User credentials, Password, and specific Database name for synchronization. Additionally, configure the Encryption method to ensure secure data transmission and select the appropriate replication method (such as Standard or Change Data Capture) based on your synchronization requirements.
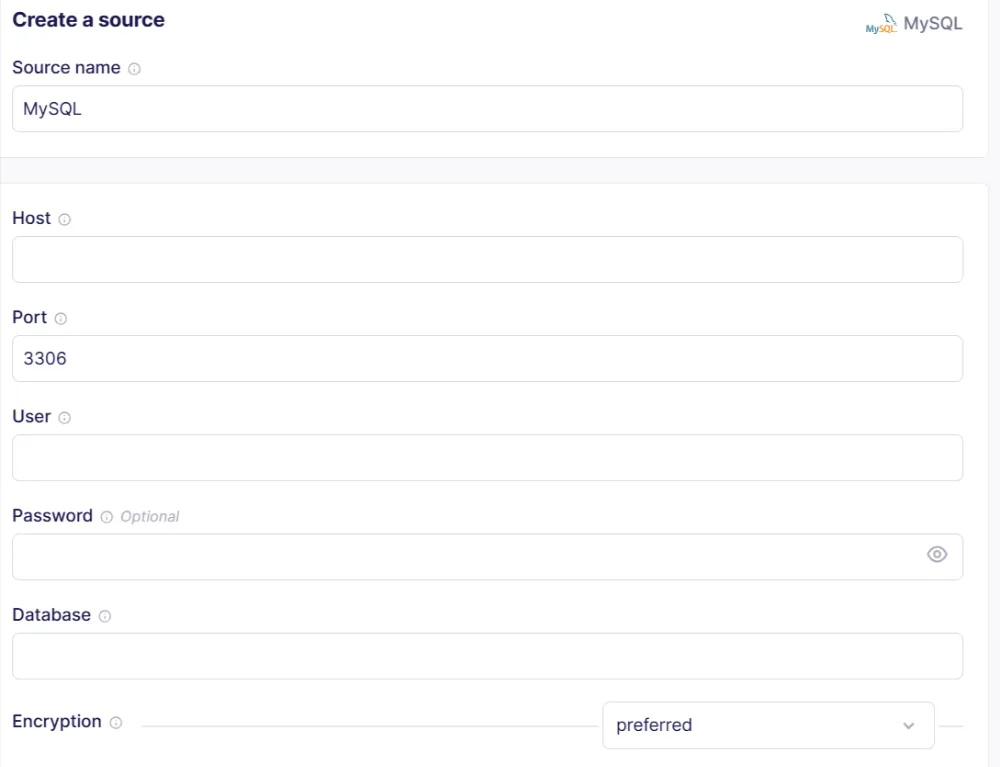
For detailed configuration guidance and advanced options, consult the Airbyte MySQL source connector documentation. Complete the source setup by clicking Set up source.
Step 2: Connect Your MySQL Database as Destination
Navigate to the Destinations section and search for the MySQL connector to establish your target database connection. The destination configuration mirrors the source setup process but focuses on the target environment where synchronized data will be stored.
Enter the destination Host address, Port configuration, target Database name, and authenticated User credentials with appropriate permissions for data writing operations. Configure SSH Tunnel Method settings if your network architecture requires secure tunneling for database connections, ensuring compliance with organizational security policies.
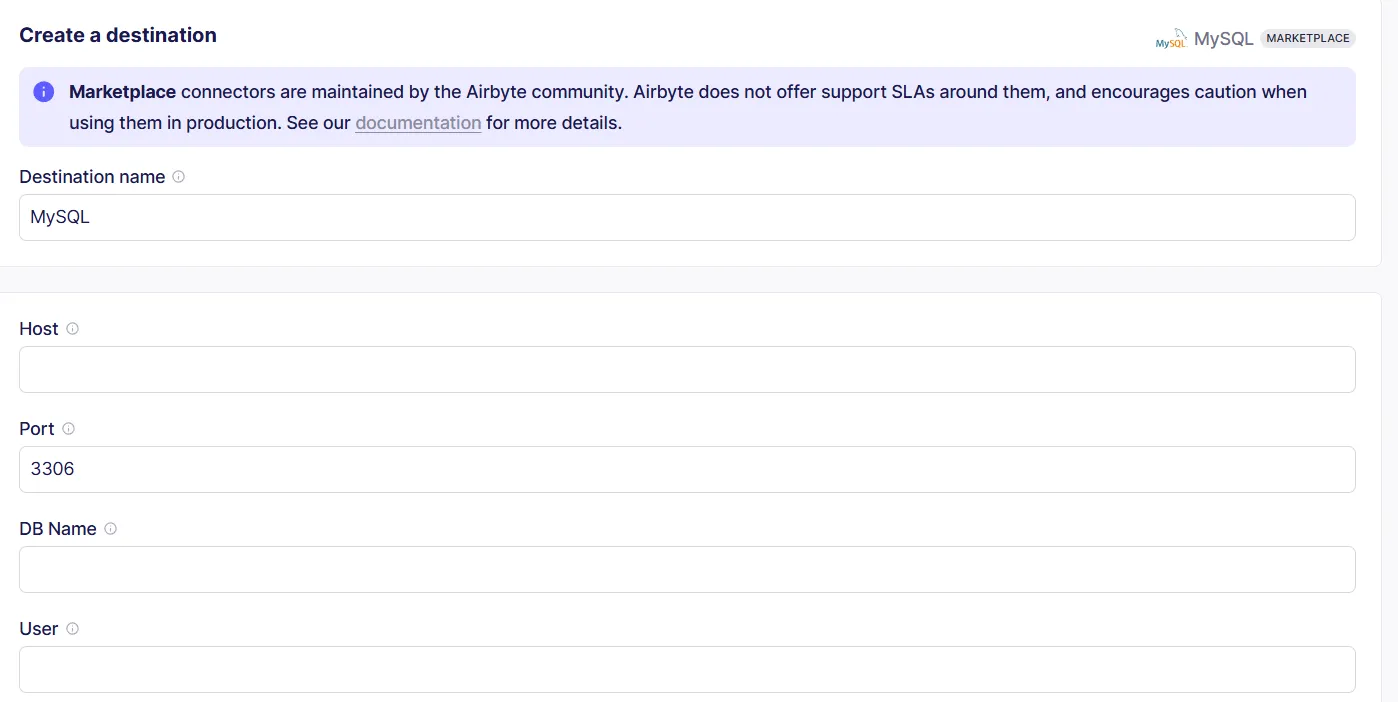
Complete the destination configuration by clicking Set up destination, which validates your connection parameters and prepares the target environment for data synchronization operations.
Step 3: Sync MySQL Databases
Access the Connections section to establish the synchronization relationship between your configured MySQL source and destination. Select your previously configured MySQL source and destination to create a new connection that defines the data flow parameters and synchronization behavior.
The Select stream interface enables granular control over data synchronization scope. This allows you to specify which tables, views, or data subsets participate in the synchronization process. This capability proves essential for optimizing performance and managing data volumes by synchronizing only the data elements required for your specific use case.
Configure connection parameters including Connection name for easy identification, Schedule Type to determine synchronization timing, Replication Frequency based on your data freshness requirements, and Destination Namespace to organize synchronized data within the target database structure.

Complete the setup by clicking Finish & Sync to initiate the synchronization process. This will begin transferring data according to your configured parameters while providing real-time monitoring capabilities through Airbyte's dashboard interface.
How Do You Sync MySQL Databases Manually?
Manual MySQL synchronization provides granular control over replication architecture through traditional master-slave configurations where a primary server maintains authoritative data while one or more secondary servers replicate changes through binary log processing. This approach enables deep customization of replication behavior while providing complete visibility into synchronization operations.
The manual approach requires comprehensive understanding of MySQL's internal replication mechanisms, network configuration requirements, and security considerations. While more complex than automated solutions, manual synchronization offers maximum flexibility for organizations with specific performance requirements or complex security constraints.
Step 1: Configure Network Access
Establish secure network connectivity between all participating servers by opening port 3306 on the Master server to enable Slave connections. Configure firewall rules to permit MySQL traffic while restricting access to authorized servers only, maintaining security boundaries throughout the replication topology.
Step 2: Create a Replication User Account
Step 3: Define MySQL Configuration Properties
Master my.cnf:
Slave my.cnf:
Restart MySQL services on all servers and verify binary logging via:
Step 4: Take a Snapshot of the Master Database
Record File and Position, copy the data directory, then:
Step 5: Prepare the Data for the Slave Server
While tar and scp can copy the MySQL data directory, these commands alone are not sufficient to safely initialize a replication slave; proper MySQL tools and procedures are needed for consistency and correct setup.
Step 6: Import Data to the Slave Server
Restart MySQL on the slave.
Step 7: Initiate the Data Replication Process
Verify with:
What Are the Advanced MySQL Synchronization Techniques Available Today?
Change Data Capture and Real-Time Processing
Change Data Capture tools such as Debezium stream INSERT, UPDATE, and DELETE events from MySQL's binary log. These tools often pipe data into platforms like Apache Kafka for scalable distribution across multiple downstream systems.
This approach enables real-time analytics and event-driven architectures that respond immediately to database changes. Modern CDC implementations provide exactly-once delivery guarantees and support complex transformation logic during the streaming process.
Global Transaction Identifiers and Enhanced Replication
GTID-based replication removes file/position management complexity, simplifies failover procedures, and enhances operational reliability. Combined with MySQL Group Replication, this approach supports multi-master, virtually synchronous clusters that provide automatic failover and conflict resolution.
These advanced replication topologies enable active-active configurations where multiple nodes accept write operations. The system automatically manages consistency and conflict resolution across the cluster.
Modern Integration Architectures
Container orchestration platforms like Kubernetes enable MySQL data to flow through transformation, validation, and analytics layers with automatic scaling and fault tolerance. Microservices architectures and event-driven patterns provide sophisticated data processing pipelines.
These modern approaches integrate MySQL synchronization with broader data platform architectures. They support complex workflows that combine batch processing, stream processing, and real-time analytics capabilities.
How Do You Ensure Security and Compliance in MySQL Synchronization?
Encryption and Data Protection Frameworks
Implement comprehensive encryption strategies that protect data throughout the synchronization lifecycle. Modern MySQL synchronization platforms provide built-in encryption capabilities that integrate seamlessly with existing security frameworks.
Access Control and Authentication Mechanisms
Role-based access control provides granular permissions management for synchronization operations. Multi-factor authentication adds additional security layers for administrative access. Strict service-account governance ensures that automated processes operate with minimal required privileges.
These security measures prevent unauthorized access while maintaining operational efficiency. Regular security audits and access reviews ensure that permissions remain appropriate as organizational needs evolve.
Compliance and Audit Frameworks
Detailed audit logs support compliance requirements across multiple regulatory frameworks. Data minimization policies ensure that only necessary data participates in synchronization processes. Incident response procedures provide structured approaches to security events and compliance violations.
When Should You Use Each Synchronization Method?
Airbyte Platform Advantages
Airbyte provides rapid setup capabilities with 600+ pre-built connectors that eliminate custom development overhead. The platform supports cloud, hybrid, and on-premises deployment options that align with diverse infrastructure requirements. Incremental and full-refresh synchronization modes optimize performance, while scalable deployment options allow Airbyte to handle varying workload demands when configured with external tools like Kubernetes autoscaling.
Organizations benefit from enterprise-grade governance features, comprehensive monitoring capabilities, and professional support options. The platform's no-code approach enables business users to configure synchronization workflows without extensive technical expertise.
Manual Implementation Scenarios
Manual implementation provides maximum control over performance optimization and security configurations. Organizations with complex multi-master topologies or specific compliance requirements often require custom synchronization logic that automated platforms cannot provide.
Teams with deep MySQL expertise can implement sophisticated replication strategies that optimize for specific performance characteristics. Manual approaches also provide complete visibility into synchronization operations and enable fine-tuned troubleshooting capabilities.
Hybrid Approaches
Combine Airbyte for routine synchronization tasks with manual optimization for critical performance paths. This approach leverages the efficiency of automated platforms while maintaining control over business-critical operations.
Use Airbyte Enterprise for advanced governance and professional support while implementing custom solutions for specialized requirements. This strategy provides the best balance between operational efficiency and technical control.
What Are the Primary Use Cases for MySQL Sync?
Data Protection and Business Continuity
Hot standbys and geo-replicated disaster recovery sites ensure rapid failover capabilities during system failures. These architectures minimize downtime and data loss while providing transparent recovery for end users.
Modern disaster recovery implementations support automated failover with minimal manual intervention. Geographic distribution protects against regional disasters while maintaining performance for global user bases.
Development and Testing Optimization
Production-like replicas provide realistic testing environments without impacting live traffic. Development teams can experiment with complex queries and data transformations using current production data while maintaining complete isolation from operational systems.
Automated synchronization ensures that development environments remain current with production changes. This approach improves testing accuracy while reducing the risk of environment-specific issues in production deployments.
Analytics and Reporting Workloads
Read replicas and CDC pipelines feed data warehouses and real-time dashboards, significantly reducing the impact on transactional system performance. This separation enables complex analytical queries while maintaining optimal performance for operational workloads.
Modern analytics architectures leverage MySQL synchronization to support both historical reporting and real-time analytics capabilities. Stream processing enables immediate insights while batch processing provides comprehensive historical analysis.
Conclusion
MySQL synchronization has evolved from basic backup procedures to sophisticated, highly available, real-time data architectures that support modern enterprise requirements. Automated tools like Airbyte democratize these capabilities by providing enterprise-grade synchronization without operational complexity.
Advanced techniques such as CDC and GTID replication address stringent performance and consistency demands for mission-critical applications. Organizations should evaluate their specific consistency, performance, security, and operational requirements to select the optimal synchronization strategy that balances technical capabilities with resource constraints.
Frequently Asked Questions
1. What is the difference between MySQL replication and synchronization?
MySQL replication automatically copies data changes between servers (master-slave or master-master), while synchronization is a broader concept, including replication and other methods to keep databases consistent, such as batch jobs, third-party tools, or real-time integration.
2. How often should I synchronize my MySQL databases?
Synchronization frequency depends on your needs: real-time apps need continuous sync or change data capture (CDC), while analytics may only need hourly or daily updates. Consider data volume, network bandwidth, system load, and business-criticality when deciding.
3. Can I synchronize MySQL databases across different cloud providers?
Yes, MySQL synchronization works across different cloud providers and hybrid environments. Tools like Airbyte support cross-cloud synchronization by establishing secure connections between different cloud environments. You'll need to configure proper network connectivity, security policies, and consider data transfer costs when synchronizing across cloud providers.
4. What happens if my MySQL synchronization fails?
If MySQL synchronization fails, databases can become out of sync, risking data inconsistencies or service disruption. Recovery requires identifying the failure, fixing the issue, and resuming replication from the last successful checkpoint or log position.
5. How do I handle schema changes during MySQL synchronization?
To handle schema changes during MySQL synchronization, plan carefully to maintain consistency. Use tools like Airbyte that auto-adapt to schema changes, or coordinate updates manually with versioning and backward compatibility, restarting replication if necessary.

.webp)
