Cross-Border Data Residency: GDPR + US CCAR Architecture Patterns
Summarize this article with:
✨ AI Generated Summary
Global banks must balance GDPR's strict data sovereignty and privacy rules with the US Federal Reserve's CCAR transparency and auditability demands, requiring architectures that ensure both compliance and low-latency performance. Key solutions include:
- Hybrid control planes with local data planes to keep data regional while enabling centralized management.
- Regional data hubs that maintain jurisdiction-specific copies and synchronize sanitized aggregates.
- Pseudonymization gateways that tokenize sensitive data before cross-border transfer, preserving privacy and auditability.
Best practices emphasize data classification at ingestion, encryption or pseudonymization before transfer, immutable audit trails, and careful vendor selection to meet evolving global residency mandates without sacrificing performance.
If you're running a global bank, you live in a tug-of-war. Europe's GDPR demands iron-clad privacy and keeps personal data under EU sovereignty, while the US Federal Reserve's CCAR stress tests require radical transparency into every capital-planning dataset. Failing either side is costly. GDPR violations can trigger penalties of up to 4% of worldwide annual revenue (€20 million minimum), and a CCAR model that lacks auditable data can stall dividend payouts or share buy-backs, draining market confidence overnight.
The engineering dilemma is just as stark. Traders expect millisecond access to positions and risk metrics, yet regulators expect those same records to stay inside their legal fences. You can't simply pick latency or compliance — you need both.
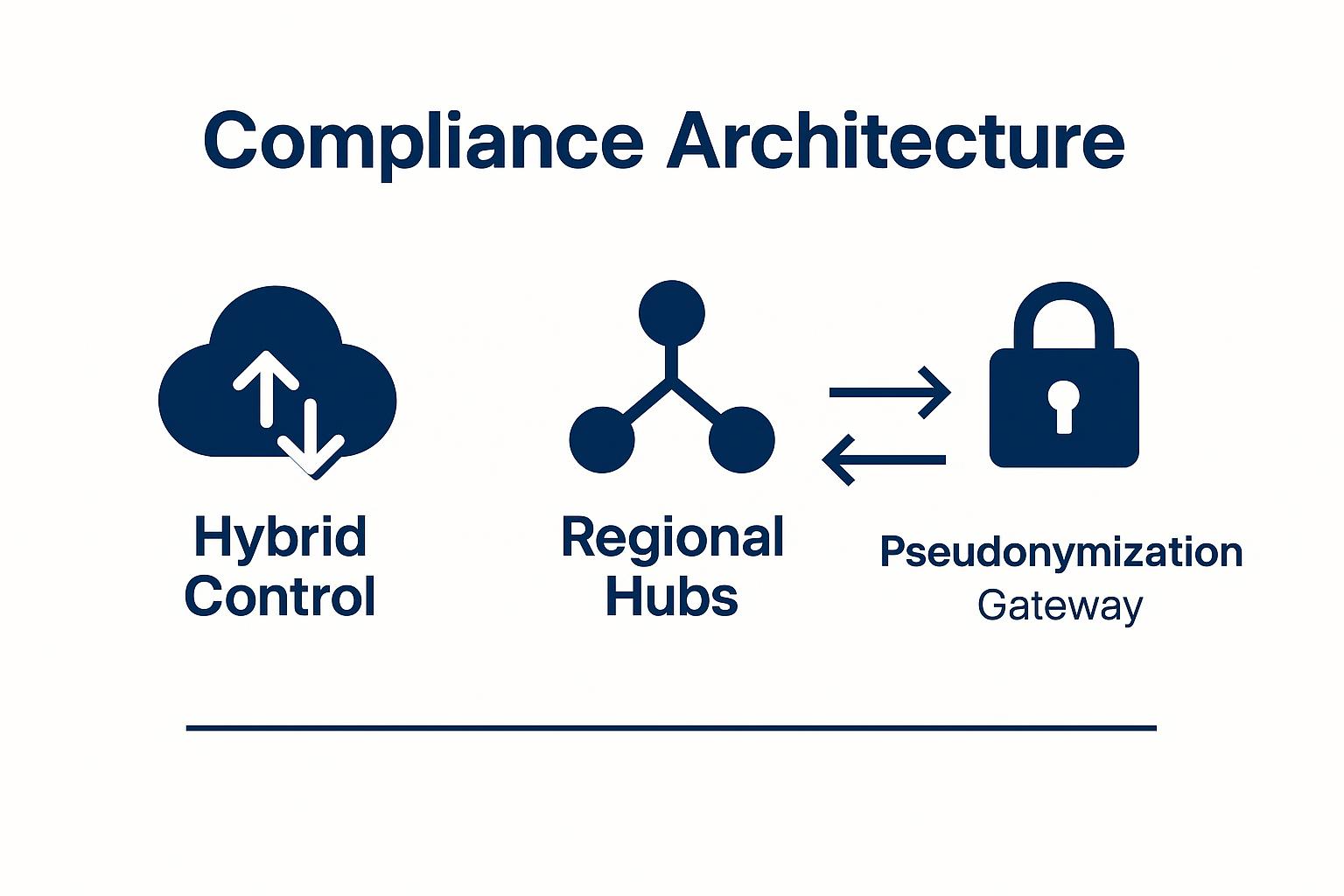
Three architecture patterns square this circle: a hybrid control plane with local data planes, regional data hubs, and a pseudonymization gateway. Together they preserve sovereignty, satisfy audit teams, and keep your pipelines fast.
What Is Cross-Border Data Residency and Why Does It Matter?

When you operate a global banking platform, every customer interaction generates data that must live somewhere. Cross-border data residency describes where that data is physically stored versus where it can be accessed, processed, or analyzed. Under frameworks like the GDPR, storage location alone isn't enough. You also need legal grounds before sending personal data outside the EU, while US rules focus more on security than geography.
It helps to separate three often-confused concepts:
- Data residency is the simple fact of storage in a given jurisdiction.
- Data sovereignty adds another layer: the local laws that continue to apply to the data wherever it travels.
- Data localization is the strictest form, requiring certain records (Russia-based payments or Chinese consumer profiles, for example) to never leave national borders. More than 135 countries now enforce some variety of these rules, and the list grows every year.
For financial institutions, that patchwork collides with daily realities like millisecond trade execution and multi-jurisdiction stress testing. The result is a tightrope walk that exposes you to regulatory, operational, and reputational threats.
Jurisdictional conflicts create immediate architectural challenges. GDPR permits transfers with safeguards, while countries such as Russia or China mandate local storage, forcing you to architect region-specific data planes. Localization mandates compound this complexity by requiring redundant infrastructure in every market, inflating costs while making business continuity fragile. Ignoring local rules can halt operations overnight.
Multi-regulator oversight adds another layer of complexity. You must satisfy EU data-protection authorities and the US Federal Reserve simultaneously, often with contradictory expectations.
Understanding these layers is the first step toward building an architecture that keeps information close to both your users and the law.
How Do GDPR and US CCAR Shape Data Architecture Requirements?
Global financial platforms face two distinct regulatory expectations that fundamentally reshape architectural decisions. GDPR protects personal information of EU residents, while the Federal Reserve's CCAR program demands integrity and auditability for capital-planning datasets. Both regulations change what your infrastructure can and cannot do.
GDPR doesn't require in-country storage, but makes every transfer outside the EEA conditional. You can move personal information only through adequacy decisions, Standard Contractual Clauses, Binding Corporate Rules, or narrow derogations. Each route demands documented Transfer Impact Assessments and Processing Agreements. If local law threatens privacy, you must add supplementary measures like encryption or pseudonymization. Every decision requires documentation for regulatory inspection.
CCAR never dictates where information lives. It requires stress-test inputs, risk models, and reports to be accurate, traceable, and available to supervisors across jurisdictions. Your architecture needs immutable lineage, fine-grained access controls, and fail-safe retrieval. You can satisfy these goals with regional replicas or cloud regions as long as quality remains provable.
GDPR pushes you to keep personal identifiers local or protected. CCAR pressures you to expose the same information's provenance. The forces intersect in specific ways:
What Architecture Patterns Support Compliance With Both Frameworks?
You need infrastructure that keeps GDPR sovereignty intact while delivering the audit trails CCAR examiners demand. Three complementary patterns solve this problem by separating control from storage, creating regional boundaries, and enforcing privacy at transfer points.
Hybrid Control Plane With Local Data Planes
Hybrid deployment through a control plane with local storage planes gives you centralized orchestration without compromising residency. Your control plane sits wherever makes operational sense. It manages connector configs, enforces global policies, and orchestrates jobs. But all actual reads and writes stay inside regional boundaries. EU personal information never crosses the border, yet you still get the unified lineage and reconciliation reports CCAR reviewers expect. Cloud vendors already expose region-pinned services you can wire into this design. The remaining work is building a jurisdiction-aware scheduler and immutable logging, techniques already documented in secure-coding guidance for regulated industries.
Regional Data Hubs
Regional hubs add clarity when multiple jurisdictions matter equally. Create an EU hub and a US hub, each containing its own copy of the same schema. Personal or transaction-level records stay in their local hub. Sanitized aggregates flow through a narrow, logged synchronization channel. The information crossing the Atlantic already meets GDPR export rules through standard contractual clauses and supplementary encryption measures. CCAR transparency works because both hubs can regenerate a unified risk view on demand from identical aggregation logic.
Pseudonymization Gateways
Pseudonymization gateways handle the jurisdictional boundary problem by positioning themselves at every border crossing. Sensitive columns (names, account numbers, IP addresses) get replaced with reversible tokens before any message leaves its origin region. Key material stays in the source jurisdiction, satisfying GDPR's requirement for supplementary measures. CCAR analysts downstream can still correlate records through consistent tokens. Implementation is conceptually clear, but practical deployment can be complex and resource-intensive, requiring careful attention to integration, scalability, and compliance challenges.
These patterns create a clear flow: source systems feed local planes, gateways enforce transformation, audit logs capture every event, and regional hubs expose only the views each regulator can see.
How Can You Balance Performance With Compliance?
You can preserve sub-second performance without stepping outside the rules by combining jurisdiction-aware architecture choices with privacy-enhancing techniques that work together rather than against each other.
Performance Optimization Strategies
Strategic caching with geo-fences keeps frequently accessed reference information in the jurisdiction where it's consumed while preventing write operations that would violate local storage laws. This approach works particularly well for market information that needs to be available instantly but doesn't change frequently.
Read-only replicas combined with pseudonymization let you replicate market or risk information across regions while stripping or tokenizing personal identifiers before the replica leaves its home region. This technique satisfies requirements for supplementary measures while maintaining accessibility for trading systems.
Secure API gateways that enforce transfer contracts validate every cross-border call against the relevant SCC or BCR identifier, logging the legal basis for auditors. These gateways act as compliance checkpoints that don't slow down legitimate flows.
Low-Latency Processing Techniques
Edge or regional processing nodes run latency-sensitive analytics (like pre-trade risk checks) inside the same jurisdiction as the raw information, sending only aggregated results across borders. This keeps your critical path fast while respecting sovereignty boundaries.
Federated queries with on-the-fly redaction execute joins in place and return only the fields permitted by the destination's legal context, minimizing movement of protected information while maintaining query performance.
Implementation Comparison
What Are Best Practices for Cross-Border Implementation?
Building cross-border pipelines that satisfy both regulatory frameworks starts with accepting that every movement will face scrutiny. Compliance needs to be part of your architecture from day one through strategic design choices that anticipate regulatory requirements.
Start with classification at ingestion by tagging every record with jurisdiction, purpose, and retention rules the moment it enters your system. These tags need to flow through every service and transformation. Privacy by Design principles require this upfront work, but it prevents compliance disasters downstream.
Encrypt or pseudonymize sensitive fields before they cross borders to help address GDPR transfer requirements (alongside required legal mechanisms) while keeping CCAR's transparency intact. Geo-fencing at your storage plane edge enforces these rules automatically with no manual intervention needed.
Immutable audit trails provide the highest standard of evidence to meet or exceed regulatory expectations. Every access, transformation, and cross-border movement can be logged with cryptographic seals, capturing detailed telemetry such as who accessed what information, from where, and why. Stream this to real-time monitors so you catch violations before they become reportable incidents.
Third-party risk becomes your risk, making vendor selection critical. Vet cloud providers for regional hosting, encryption standards, and documented incident response procedures. Your contracts need Standard Contractual Clauses or Binding Corporate Rules. Processing agreements must specify which party owns encryption keys, handles key rotation, and manages breach notification.
How Do You Build a Sustainable Cross-Border Architecture?
You don't have to trade performance for compliance. Anchor your design in clear jurisdictional boundaries. Store EU personal information in-region, document every outbound flow, and hard-wire audit trails. This approach supports GDPR compliance best practices and keeps CCAR auditors happy with transparent, immutable lineage.
With expanding residency mandates worldwide, a sovereign-first control plane coupled with local storage planes is one of the most reliable ways to future-proof your stack and avoid reactive fixes.
GDPR and CCAR aren't adversaries. GDPR's insistence on geographic control strengthens the integrity and availability CCAR already demands. You get a single, defensible record of where information lives, how it moves, and who touched it.
Build on that foundation and your architecture evolves with the law instead of against it. Airbyte Flex solves cross-border residency requirements with cryptographically verifiable lineage, meeting GDPR and US CCAR standards without compromising capability.
Talk to Sales about your regulatory architecture.
Frequently Asked Questions
What is the difference between data residency and data sovereignty?
Data residency refers to the physical location where data is stored, while data sovereignty extends this concept to include the legal jurisdiction that governs the data regardless of where it travels. Data localization is the most restrictive form, requiring certain data types to never leave specific national borders.
Can GDPR and CCAR requirements be satisfied simultaneously?
Yes, GDPR and CCAR can be met together with careful architecture. Use regional data planes to keep EU personal data local while maintaining unified audit trails. A hybrid control plane ensures both privacy compliance and data integrity for stress testing.
What are Standard Contractual Clauses (SCCs) and when are they needed?
Standard Contractual Clauses (SCCs) are EU-approved legal tools enabling personal data transfers to countries without adequacy decisions. They're required for moving EU data to such countries and should be paired with technical measures like encryption to maintain privacy protections.
How do pseudonymization gateways work in practice?
Pseudonymization gateways sit at jurisdictional boundaries and replace sensitive data fields (names, account numbers, IP addresses) with reversible tokens before data crosses borders. The tokenization keys remain in the source jurisdiction, satisfying GDPR requirements while allowing downstream analysis through consistent token correlation.
What performance impact should I expect from compliance measures?
Performance impact varies by implementation approach. Strategic caching and edge processing typically add less than 1ms latency, while secure gateways may add 5-20ms. The key is choosing the right combination of techniques based on your specific latency requirements and compliance obligations.
How should I handle vendor selection for cross-border data integration?
Evaluate vendors based on regional hosting capabilities, encryption standards, documented incident response procedures, and compliance certifications. Ensure contracts include appropriate legal mechanisms (SCCs or BCRs) and clearly specify responsibilities for encryption key management, data breach notification, and regulatory reporting.

.webp)
