Is Running ETL Straight from S3 or GCS Safe?
Summarize this article with:
✨ AI Generated Summary
Cloud object storage ETL is secure when implementing three key controls: end-to-end encryption (S3 SSE-KMS, GCS CMEK), least-privilege IAM, and private networking to avoid public internet exposure. Additional best practices include enabling versioning and logging, isolating transformation workloads, continuous monitoring, and automated policy scanning to prevent common breaches caused by weak credentials or misconfigurations. Compliance with GDPR, HIPAA, and SOC 2 is ensured through encryption, immutable audit logs, and data classification, while tools like Airbyte facilitate secure, scalable, and auditable ETL pipelines.
A significant percentage of cloud-related breaches stem from weak or misplaced credentials, often leaving object storage buckets vulnerable to the internet.
Enterprise data teams are pushing ever-larger volumes of customer transactions, sensor logs, and financial records through Amazon S3 or Google Cloud Storage as the first hop in their ETL pipelines. The challenge: move data quickly without becoming a security headline.
Modern ETL tools now default to encrypted transfers and KMS-backed secrets, reducing the amount of custom credential-handling code you have to maintain.
The core question isn't whether cloud object storage is inherently secure but whether your implementation follows the non-negotiable controls that separate bulletproof architectures from breach headlines.
With proven patterns such as server-side encryption (S3 SSE-KMS, GCS CMEK), least-privileged IAM, private networking, and continuous monitoring, you can design pipelines that move at cloud speed without compromising security.
When Is Running ETL Directly from Object Storgage Safe?
Yes, running ELT directly from S3 or GCS is safe, provided you secure storage, network, and identity; otherwise, it's a breach waiting to happen.
Cloud object stores offer very high, scalable throughput and, in Amazon S3's case, '11 nines' of durability, making ETL directly from Amazon S3 or Google Cloud Storage operationally sound.
The real variable is how rigorously you implement three non-negotiable controls:
- First, encryption in transit and at rest with platform-native keys (S3 SSE-KMS, GCS CMEK). Using envelope encryption means a unique data key protects each object, while the master key never touches the data itself, limiting the blast radius if anything leaks. You can also enforce this automatically at the bucket level.
- Second, least-privilege IAM. Grant only the permissions an ETL job truly needs, avoid wildcards like *:*, and rotate keys frequently. IAM policy linting tools on AWS and GCP make it easy to prove nobody can read more than they should.
- Third, private networking. Route traffic through VPC Gateway or Interface Endpoints on AWS or Private Service Connect on GCP, so data never traverses the public internet.
Keeping raw data in object storage also future-proofs you: it remains warehouse-agnostic, allows you to replay failed loads, and serves as a convenient backup layer. Skip any one of these controls, though, and you could run afoul of GDPR Article 32 or HIPAA §164.312 in a single incident.
Why the urgency? More than half of breaches stem from weak credentials—gaps that attackers happily exploit. Tightening encryption and IAM closes both doors, turning your direct-from-storage ETL from a liability into a hardened, auditable workflow.
How Do You Secure Direct-from-Object-Store ETL?
Locking down an S3 or GCS-based pipeline doesn't have to take weeks. Follow these five controls, and you'll cover the highest-impact attack surfaces in a single afternoon.
1. Encrypt End-To-End
Enable server-side encryption with managed keys—S3 SSE-KMS or GCS CMEK—so that every object is wrapped in envelope encryption. The data key encrypts the file, while the master key never touches bulk data, thereby reducing the blast radius if storage is compromised.
Pair this with TLS 1.2 or higher for all transfers to substantially reduce man-in-the-middle exposure. This dual-layer approach keeps your data protected both in motion and at rest.
2. Harden IAM
Grant your ETL job a role that can only GetObject and PutObject on the specific bucket prefix it needs—no wildcards. Rotate credentials with short-lived tokens so leaked keys expire quickly and require MFA for anyone who can edit policies.
Right-sizing permissions is your cheapest risk reduction. Lock down access to only what each process actually needs.
3. Enable Versioning, Logging, and MFA-Delete
Bucket versioning lets you roll back a bad transform in seconds while access logs capture every read and write for forensic replay. Add MFA-Delete so attackers—or careless scripts—can't wipe history without a second factor.
With immutable logs in place, you can answer the audit team's favorite question: "Who touched that record and when?"
4. Isolate Transformation Workloads
Run transformations in their own sandbox—Kubernetes namespaces, Snowflake external stages behind network policies, or a serverless function with VPC-only egress. This keeps raw data in the object store and prevents lateral movement if the compute layer gets breached.
Airbyte adopts this model: each connector operates within an isolated worker, with RBAC governing what it can fetch or write.
5. Monitor Continuously
Feed S3 CloudTrail or GCS Audit Logs into your SIEM and set alerts for anomalies: sudden location changes, bulk downloads, or policy edits outside business hours.
Airbyte exposes job-level audit logs by default, making it easy to plug pipeline events into the same watchlist. Alert fatigue can lead teams to chase spurious correlation instead of real root causes, so tune your anomaly-detection thresholds carefully.
Implement these five controls, and running ETL straight from object storage shifts from "risky shortcut" to "security-forward architecture"—ready for compliance audits and weekend-proof against surprise pager alerts.
What are the Main Security Threats When Running ETL from Cloud Storage?
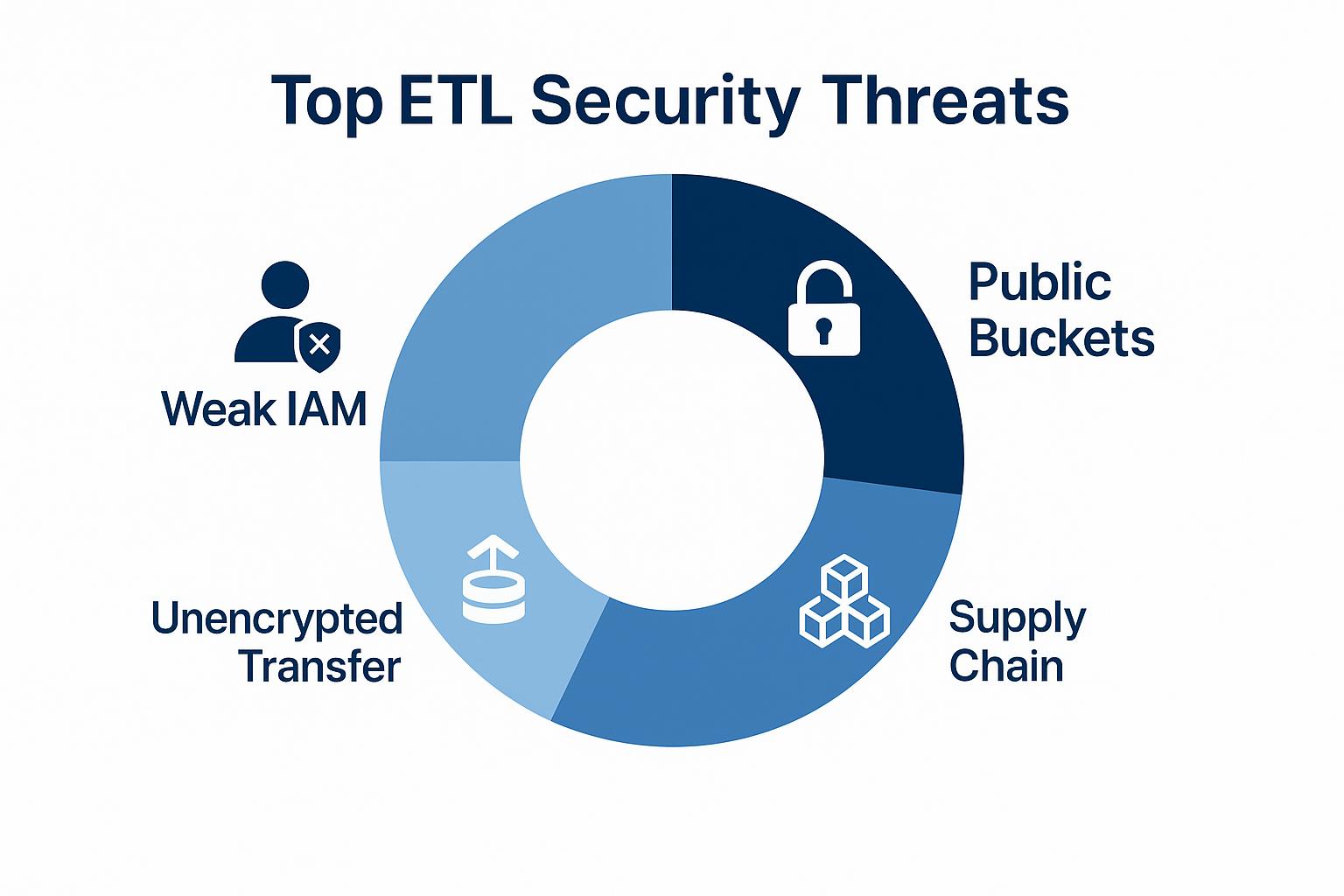
Cloud object stores offer durability and scale, but a single misconfiguration can expose every record you load or transform.
The most common attack paths typically follow predictable patterns, each with concrete fixes that close them off.
Public-Bucket Data Exfiltration
A public S3 or GCS bucket is an open invitation for data theft. Attackers routinely scan the internet for misconfigured buckets and download anything they find.
You eliminate that avenue by turning on S3 "Block Public Access" or GCS "Uniform Bucket-Level Access" and refusing any policy that grants AllUsers read rights.
Versioning and access logs provide a forensic trail if someone slips through, but blocking access at the edge prevents 99% of accidental exposures before they occur.
Misconfigured IAM Roles
Overly broad credentials, such as IAM policies that grant *:* permissions to ETL jobs, can occur but are strongly discouraged and should be avoided in favor of least-privilege access. Follow least privilege: a loader only needs GetObject on a specific prefix, not full bucket admin.
Run AWS IAM Access Analyzer or GCP Policy Intelligence before every deployment and alert on any policy that escalates rights. Rotate keys with STS, use short-lived service accounts, and force MFA for human users.
Man-in-the-Middle During Transfer
Without proper encryption, packet sniffing becomes a real threat. Require TLS 1.2+ on every endpoint, whether you're pulling files with aws s3 cp or a JDBC driver.
Signed URLs add an extra layer by binding each request to a unique token and expiry. For batch jobs, pin your CA bundle so a forged certificate can't sidestep encryption.
Supply-Chain Risk in Transformation Code
Your ETL container might be pulling a base image that was compromised yesterday. Pin exact image digests and scan each build with Trivy or Grype before promotion.
Store images in a private registry and enable Binary Authorization so only signed, vetted artifacts reach production.
That way, even if an upstream library goes rogue, layered controls significantly reduce—but do not entirely eliminate—the risk of a poisoned image running in your cluster.
Object Version Rollback
Versioning is fantastic for recovery, yet it introduces the risk of "time-travel" attacks where an adversary rolls your dataset back to an older, vulnerable state.
Audit every version ID that a job reads, and lock down DeleteMarker and PutObjectVersionAcl permissions so only a controlled CI role can overwrite or purge versions.
Sensitive Data Exposure
Parquet files in a raw zone often contain unhashed emails, salaries, or health records. If you don't label and protect them, insider threats can siphon data undetected.
Tag columns on ingestion, apply IAM condition keys that restrict access to "PII = false," and stream all CloudTrail or Audit Log events into your SIEM for anomaly detection.
Unencrypted Data in Transit
Some legacy ETL scripts still push data over plain HTTP or outdated TLS ciphers. Enforce aws:SecureTransport = true in bucket policies and reject any client that negotiates below TLS 1.2. On Google Cloud, always use HTTPS URLs for storage.googleapis.com in your jobs and avoid HTTP fallbacks in your code, as the platform does not provide a built-in option to enforce HTTPS-only for this endpoint.
API Security Gaps
High-volume ETL jobs can overwhelm storage APIs, so attackers attempt to exploit the same endpoints with credential-stuffing or injection payloads. Throttle requests per principal, validate inputs server-side, and use VPC-scoped endpoints so public internet traffic never touches your buckets.
By addressing each threat with concrete controls—such as policy linting, encryption, and private networking—you turn object-store ETL from a potential breach vector into a hardened, auditable data backbone.
How do Compliance and Governance Requirements Affect ETL Security?
Ensuring regulatory compliance in your ETL process involves more than just securing data. Regulators expect you to prove you’ve followed the necessary steps, and that proof begins by mapping technical controls to the required standards.
Key Technical Controls and Their Compliance Requirements
- Encryption at Rest
- Satisfies GDPR Art 32(1)(a), HIPAA §164.312(a)(2)(iv), and SOC 2 CC6.1.
- Amazon’s SSE-KMS and Google’s CMEK provide nearly turnkey solutions by using envelope encryption and keeping master keys in KMS, ensuring data remains unreadable if exposed.
- Immutable Audit Logs
- Address SOC 2 CC2 and CC7 requirements.
- CloudTrail (AWS) and Google Cloud Audit Logs track key usage and bucket access.
- Enable versioning and MFA-Delete to prevent insider tampering with logs, which are stored in object storage.
- Lifecycle and Erasure Rules
- Helps with GDPR Art 17 "right to be forgotten" compliance.
- Automate expiration or archival of personal data.
- Must be part of a comprehensive process, including legal review and notification.
Data Classification and Visibility for Auditors
- Raw, Unchanged Data
- Allows auditors to replay and verify every transformation.
- Be mindful of scope creep: the more raw data you retain, the larger the environment auditors must examine.
- Data Classification Tags
- Apply tags as soon as files land to track personal or sensitive data (e.g., PII).
- Tools like Airbyte offer manual column selection for protecting PII, while some others automatically tag PII at the column level.
Legal Paperwork and Contracts
- Business Associate Agreements (BAAs)
- Required for healthcare data under HIPAA.
- Data Processing Addendums and Standard Contractual Clauses
- Necessary for handling EU personal data.
- Ensure these are extended to every third-party service in your ETL pipeline.
Data Residency and Cross-Border Transfers
- Data Residency Compliance
- Ensure data remains within its designated geographic area.
- Utilize region-specific buckets and CMEK keys to prevent unauthorized cross-border transfers, particularly when processing EU customer data in a US-only analytics project.
Penalties for Non-Compliance
- Fines for Violations
- GDPR: Fines can reach up to 4% of a company's global annual revenue.
- HIPAA: Civil penalties can be up to $50,000 per violation, with annual caps for repeated violations.
By implementing these controls, you not only stay compliant but also protect your organization from hefty fines.
Which Architecture Pattern Should You Choose for Object Storage ETL?
Choosing how you pipe data from S3 or GCS into analytics systems is largely an architecture question. The pattern you select sets the ceiling for both throughput and risk, so it pays to weigh speed, blast radius, and compliance in the same breath.
Best Practices and Tooling Checklist
Building on architectural patterns, these operational practices turn good designs into bulletproof implementations:
- Infrastructure as Code (IaC): Define buckets, VPC endpoints, and KMS keys in Terraform or CloudFormation. Version-controlled changes and peer reviews prevent manual configuration drift, which can lead to security gaps.
- Automated Policy Scanning: Integrate scanners that flag public buckets, overly permissive IAM policies, and unencrypted objects. Static analysis catches misconfigurations before they reach production.
- Zero-Trust Networking: Route ETL traffic through private links (AWS VPC Endpoints, GCP Private Service Connect). Combine with mutual TLS to eliminate implicit trust and block lateral movement.
- Object Lifecycle Rules: Automate retention by moving non-current versions to Glacier/Coldline after 30 days. This limits the blast radius and manages storage costs without manual intervention.
- Hash-Based Integrity Checks: Generate and verify SHA-256 or MD5 hashes on ingest and before load. Corrupted or tampered objects never reach downstream analytics.
- Blue/Green Buckets for Schema Changes: Route writes to a "green" bucket while validating new schemas in "blue." Flip the pointer when tests pass for instant, version-controlled rollbacks.
- Data Catalog Integration: Push bucket metadata and column-level tags to your catalog. PII becomes discoverable and governed from day one, accelerating GDPR/CCPA audits and right-to-be-forgotten requests.
- Penetration Testing: Schedule red-team exercises focused on bucket ACLs, signed URL misuse, and KMS key reuse. Findings feed directly into IaC fixes for measurable hardening.
- Key Management and Rotation: Use envelope encryption with regular key rotation via SSE-KMS or CMEK. Separate permissions on data and keys enforce a defense-in-depth approach.
- Continuous Monitoring & Anomaly Detection: Stream CloudTrail or Audit Logs to a SIEM. Alert on bulk downloads, cross-region access, or policy changes. Logging gaps cause prolonged breaches.
- Centralized Identity Management: Apply least-privilege roles, MFA, and short-lived service-account tokens through cloud IAM. Consolidation simplifies audits and shrinks the credential attack surface.
- Airbyte-Powered Guardrails: Airbyte's open-standard connectors, declarative YAML configs, and lineage API integrate with these controls. Built-in RBAC and audit logging prove who accessed what data across 600+ connectors.
How Do You Troubleshoot Common ETL Security Issues?
Legacy SSIS packages often assume on-prem file shares and can break when you move staging to cloud storage unless you retrofit them with signed URLs.
Well-designed, encrypted pipelines still fail—or leak data—because of small oversights. Here are the five problems encountered most often when pulling data directly from S3 or GCS, with the fastest fixes:
- "AccessDenied" during COPY or LOAD – The role running your ETL lacks GetObject on the bucket or kms:Decrypt on the key. Double-check the bucket policy and verify the KMS key's resource policy trusts the workload's principal before rerunning the job.
- 429 "SlowDown" or request-rate exceeded – Object stores throttle when a single prefix gets bombarded with requests. Shard large tables across multiple prefixes (for example, s3://bucket/table/date=2024-06-01/part-0001) and enable S3 Transfer Acceleration to spread traffic across AWS edge locations when latency matters.
- Data skew in partitions – If one partition key (like a single customer ID) owns most rows, parallel tasks pile onto the same objects while others sit idle. Understanding the characteristics of partitioning—such as range vs. hash and static vs. dynamic—helps you design balanced shards that avoid hotspots and throttling, allowing compute threads to receive evenly sized chunks and ensuring your transforms finish predictably quickly.
- Stale credentials – Long-lived access keys break after rotation policies kick in unexpectedly and represent a breach waiting to happen. Swap them for short-lived tokens from AWS STS or GCP STS and pin their lifetime to the ETL run window.
- Versioning bloat – Enabling bucket versioning without lifecycle rules can double storage costs within weeks. Add a rule that sends non-current versions to Glacier (AWS) or Coldline (GCP) after 30 days, allowing you to retain rollback capability without incurring the cost of hot storage indefinitely.
When something still slips through, run a lightweight incident-response loop: detect unusual activity (CloudTrail or Audit Logs), isolate the offending key or service account, remediate the policy or code, retest the pipeline, and then document the post-mortem for your compliance team. Early warning beats late-night firefighting every time.
Set up budget alarms on storage growth, enable object-level logging, and stream those logs into your SIEM. Continuous monitoring is non-negotiable—real-time detection gives you precious minutes to respond to threats.
What Should You Consider Before Implementing Object Storage ETL?
The quickest way to gauge your readiness for running ETL straight from S3 or GCS is to work through a four-question rubric:
- Data Sensitivity: Are you moving PII, PHI, or high-value intellectual property?
- Regulatory Scope: Which frameworks apply (GDPR, HIPAA, SOC 2), and what controls do they mandate?
- Team Security Maturity: Do you have SRE coverage, automated policy scanning, and DevSecOps pipelines in place?
- Data Volume and Velocity: Will throughput or real-time requirements force architectural trade-offs?
If any of these answers feel uncertain, start by testing in a non-production environment. You can easily spin up a proof of concept with Airbyte's open-source connectors, which include over 600 options, allowing you to validate permissions, encryption, and throughput in a single day.
Before moving to production, commission a penetration test and integrate key rotation, audit logging, and least-privilege IAM into your Infrastructure as Code (IaC) modules.
Security isn’t a one-time task—it’s a continuous effort. Schedule quarterly control reviews, monitor emerging threats, and reassess vendors for updated compliance certifications.
Running ETL straight from object storage can be bulletproof if you prioritize security from the start. By adopting the right patterns, controls, and monitoring strategies, you transform what could be a risk into a competitive advantage—delivering secure, scalable, and audit-ready data pipelines that support business growth without compromising protection.
If you're ready to streamline your data pipelines with built-in security, try Airbyte.
Our open-source platform provides over 600 connectors and customizable integrations, enabling you to scale securely while maintaining compliance. Get started with Airbyte today and take the first step towards building a secure, efficient, and audit-ready ETL pipeline.

.webp)
