Data Sovereignty Solutions: Multi-Jurisdictional Compliance Guide
Summarize this article with:
✨ AI Generated Summary
Data sovereignty mandates that digital information complies with the laws of the country where it is stored or processed, complicating global compliance due to overlapping regulations like GDPR, HIPAA, and PIPL. Traditional ETL and cloud-only pipelines often fail sovereignty tests because they lack native, region-specific controls, leading to costly violations and operational disruptions.
- Enterprises must map data flows, design sovereignty-first architectures with region-locked processing planes, and enforce strict governance using immutable audit logs and automated monitoring.
- Unified platforms like Airbyte Flex enable multi-jurisdictional compliance by separating orchestration from local execution, reducing latency, egress fees, and compliance risks.
- Choosing the right solution requires ensuring deployment flexibility, encryption key control, comprehensive auditability, and proven regulatory compliance support.
An overnight sync pushes EU customer records to a U.S. analytics cluster, Chinese user logs slip into the same pipeline, and by morning you're juggling simultaneous GDPR, HIPAA, and PIPL violations. Fines can reach €20 million or 4% of global revenue under GDPR and up to 5% of annual turnover in China's PIPL, numbers large enough to threaten entire product lines.
Data sovereignty, the rule that digital information is governed by the laws where it sits or is processed, has become non-negotiable as mandates splinter across regions and sectors. You now face overlapping frameworks that evolve faster than your change-control board.
This guide shows you how to map those regulatory minefields, exposes why traditional ETL and cloud-only pipelines fail sovereignty tests, and walks through sovereignty-first architectures that keep data and your credibility exactly where they belong.
What Does Data Sovereignty Mean Across Different Jurisdictions?
Data sovereignty refers to the principle that digital information is subject to the laws of the country where it is stored or processed. This can be confusingly interchanged with data residency, which specifically dictates the geographic location for storage. Nations impose these requirements to safeguard personal information against misuse and ensure information remains within their control.
These requirements impact each stage of the information lifecycle, from collection and storage to processing and transfer. Enterprises must carefully map these stages to ensure compliance with the diverse regulations prevalent across the world.
This creates a challenging environment for businesses, as overlapping and occasionally contradictory requirements from these frameworks significantly complicate global compliance efforts.
Organizations need to develop robust strategies to align with these diverse regulations and protect their international flows effectively while avoiding severe penalties, disruptions, and reputational harms.
Why Do Current Data Integration Approaches Fail Sovereignty Tests?
The foundation of most integration failures lies in architectural assumptions that predate today's regulatory landscape. Traditional ETL platforms assume a single, centralized deployment where rigid architectures can't pin pipelines to specific regions or automatically block cross-border jobs.
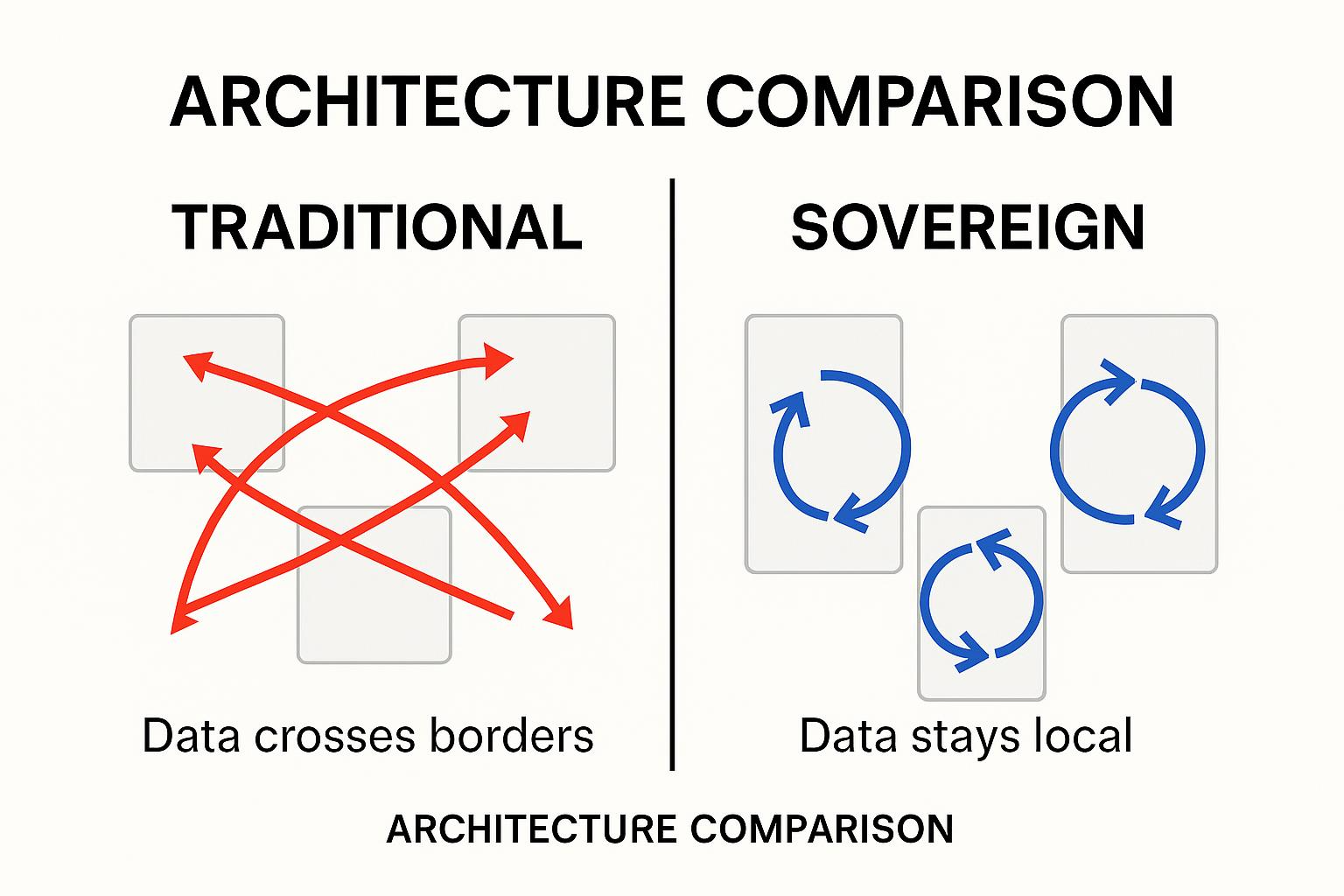
You end up hard-coding location checks and retrofitting encryption, creating brittle workarounds that don't meet encryption-by-default requirements.
Cloud-Only Integration Limitations
Cloud-only integration services create different problems entirely. Providers that promise "hands-off" ELT centralize processing in their multi-tenant centers, giving you limited control over where syncs actually run.
While reviews of platforms like Fivetran, Stitch, and Matillion highlight convenience, sovereignty guarantees depend entirely on whichever regions the vendor supports. If the provider replicates information for resiliency, you may violate GDPR or China's PIPL before seeing an alert.
Industry-Specific Impacts
These gaps hit regulated industries particularly hard:
The result is constant firefighting where compliance officers chase spreadsheet inventories, engineers patch together monitoring scripts, and both groups wait for the next regulator letter. Without native, location-aware controls, you spend more time proving where information isn't than delivering insights where it's needed.
How Can Enterprises Achieve Multi-Jurisdictional Compliance in Practice?
The fastest way to lose market access is to let a single record drift across the wrong border. You avoid that outcome by approaching compliance as an engineering problem: mapping legal constraints, encoding them in architecture, and automating enforcement instead of relying on checklists.
1. Map Your Regulatory Obligations
Start by drawing a line-by-line map of where every dataset is collected, stored, processed, and shared. Break the exercise down by business unit: marketing's click-stream events face different laws than engineering's telemetry.
Tag each class with the governing framework (GDPR, HIPAA, DORA, ITAR, PIPL) and note conflicting rules. For instance, GDPR permits personal information to leave the EU under several mechanisms, including but not limited to Standard Contractual Clauses, while China's PIPL requires 'important information' to stay onshore unless it passes a CAC security review.
Next, capture cross-border flows by drawing arrows showing how a lead captured in Berlin ends up in a US CRM or how APAC payments land in an EU warehouse. Those arrows reveal hidden transfer risks the compliance team may have missed.
Finally, load everything into a living regulatory matrix, with columns for collection, storage, processing, and transfer, and rows for each jurisdiction, and cells that outline the required safeguards. Because rules change, schedule periodic reviews to keep the map up to date.
2. Design a Sovereignty-First Architecture
With the map in hand, you can design topology instead of chaos. A common pattern is a hybrid control plane paired with sovereign processing planes. The control plane orchestrates pipelines from a central location, but every execution engine lives in the jurisdiction where its information originates. That separation means raw records never leave regulated soil unless a policy explicitly allows it.
Implement geo-fencing at the network layer and shard datasets by region so that French customer profiles, for example, physically cannot cross into a US subnet. Layer on federated access: expose secure APIs that let analysts run queries across regions without moving the underlying records, echoing the "bring computation to information, not information to computation" approach.
When teams need aggregated views, push anonymized or pseudonymized aggregates to a global lake instead of syncing the raw tables. The result is a topology that treats borders as hard constraints, not after-the-fact filters.
3. Enforce Governance and Auditability
Architecture alone is not enough. You need guardrails that prove, at any moment, that nothing slipped through. Role-based and attribute-based access control forms your first line of defense. Limit access by job function and geography so an engineer in one region can't peek at restricted records in another.
End-to-end encryption with local key management enhances security and can support compliance, but it does not by itself satisfy the residency requirements of China's PIPL, which requires personal information to be stored and processed within China alongside additional procedural and legal safeguards.
Immutable audit logs store tamper-proof records of every read, write, or transfer, letting auditors trace exactly who touched a record, when, and from where. Full lineage tracking lets you answer a regulator's "how did it get here?" within minutes, not days.
Automated policy monitoring alerts when a pipeline attempts to route information outside its allowed region, reducing the constant crisis management that plagues traditional approaches.
Together, these controls satisfy the "evidence at any time" expectation that modern regulators bring to every audit.
4. Support Cross-Border Use Cases Without Violations
Compliance doesn't mean walling off every dataset forever, but enabling business use cases safely. For EU banks subject to DORA, you can run fraud-detection models by streaming pseudonymized features to a central model, while raw transactions remain within EU processing planes.
Hospitals bound by HIPAA can keep electronic PHI inside a hospital VPC, yet share de-identified cohorts for research analytics. Telecom operators often hold subscriber records on-prem, but answer lawful-intercept queries through federated joins that never expose the underlying identifiers.
These scenarios rely on tactical techniques, including minimization, client-side encryption, and purpose-specific subsets, to satisfy sovereignty rules while still delivering value. By architecting for locality first and layering selective exposure on top, you turn regulatory borders from roadblocks into guardrails that keep your pipelines and your business out of the penalty zone.
What Role Do Unified Platforms Like Airbyte Flex Play in Sovereignty?
You meet sovereignty rules by keeping information in-country while orchestrating global pipelines. Airbyte Flex splits orchestration from execution: a cloud-based hybrid control plane steers multiple region-locked processing planes, so that sensitive records remain within their designated regions, with the exception of certain metadata (e.g., cursors or primary keys) that may be stored in the control plane.
Architecture Overview
The control plane handles scheduling, monitoring, and UI management. Every extract or load job runs inside the processing plane you assign to a jurisdiction. Each plane executes locally, so you can align processing with GDPR in Frankfurt, HIPAA in Virginia, or PIPL in Beijing without rewriting pipelines.
The model follows the control-plane vs. data-plane blueprint and supports true multi-region isolation through workspace-level assignments.
Security and Compliance Benefits
Local execution delivers the technical safeguards auditors expect. Information stays encrypted at rest and in transit, secrets remain in the same region as the records, and every sync produces immutable logs you can hand to regulators. Since only metadata interacts with the control plane, even strict frameworks like ITAR prevent accidental exports.
Flexible Deployment Options
Flex adapts to how you already deploy through three key options:
Performance and Cost Benefits
Running pipelines close to the source cuts latency and cloud egress fees. Each processing plane scales independently, so a bursty EU workload won't idle resources in APAC, and outages stay contained to a single jurisdiction.
By combining sovereign processing planes with a lightweight control layer, Airbyte Flex turns sovereignty from a blocker into a predictable part of your integration workflow.
What Outcomes Can Enterprises Expect From Sovereignty-First Architectures?
Compliance officers see immediate relief when pipelines stay within their designated jurisdictions. Audit prep shrinks from weeks to hours because dashboards auto-collect evidence from immutable logs instead of manual spreadsheet juggling.
Platforms like Airbyte Flex route every sync through region-bound processing planes, supporting clear residency and compliance boundaries, significantly reducing accidental-transfer loopholes flagged in many breach investigations.
Engineering Benefits
Engineers notice the performance gains next. Local execution keeps packets off long-haul networks, cutting replication lag and query latency. The proximity benefits deliver fresher dashboards without over-provisioning compute. Each region scales independently, so on-call alerts drop — traffic spikes in one geography don't ripple across the globe.
Business Advantages
The business gains flexibility over time. A sovereignty-first stack separates orchestration from storage, so you can swap clouds or run on-prem without rewriting connectors. Industry analysts highlight this approach as insurance against vendor lock-in and geopolitical shocks.
Teams focus on building products instead of patching pipelines, while finance sees lower egress fees and predictable regional costs.
How Do You Choose the Right Sovereignty Solution?
Frame every vendor conversation around five non-negotiables: feature parity across deployment modes, comprehensive audit trails with lineage, out-of-the-box support for GDPR/HIPAA/ITAR/DORA, granular residency controls, and open standards to prevent lock-in. These align with sovereignty best practices from regulators and the Cloud Security Alliance.
Press vendors with four critical questions that separate compliant platforms from compliance theater:
- Can I deploy independent processing planes in any region and move them if regulations change?
- Do I keep exclusive control of encryption keys within each jurisdiction?
- Are audit logs immutable, exportable, and stored in the same region as the processed information?
- Which independent attestations prove successful deployments in regulated industries?
The right platform answers each with an unqualified "yes."
Is Your Data Stack Sovereignty-Ready?
Compliance bolted on after launch is a liability. You need sovereignty-first architecture built into every pipeline so new regulations land as configuration tweaks, not crisis rewrites.
Airbyte Flex provides 600+ connectors with unified architecture across cloud, on-prem, and hybrid deployments. Organizations that architect for sovereignty from day one turn regulatory boundaries from roadblocks into competitive advantages—keeping information secure while competitors scramble to retrofit compliance into brittle systems.
Talk to Sales to discuss your regulatory architecture requirements and see how Airbyte Enterprise Flex delivers compliance without capability trade-offs.
Frequently Asked Questions
What is the difference between data sovereignty and data residency?
Data sovereignty means digital information is subject to the laws of the country where it is stored or processed. Data residency, on the other hand, only specifies the physical location of storage. Sovereignty is broader—it includes legal, compliance, and operational requirements, not just geography.
Why do traditional ETL platforms struggle with data sovereignty?
Most legacy ETL platforms assume a single, centralized deployment. They lack native region-based execution, so pipelines often cross borders by default. This creates compliance risks, as sensitive records can drift into regions where storage or processing is not legally allowed.
How can enterprises prove compliance to regulators?
The most effective approach is to use immutable audit logs, lineage tracking, and automated monitoring. These tools provide real-time evidence of where records are stored and processed. Instead of manual spreadsheets, enterprises can hand auditors verifiable logs showing compliance at every stage.
What industries are most affected by data sovereignty rules?
Financial services, healthcare, telecom, and defense face the strictest requirements. Frameworks like DORA, HIPAA, ITAR, and PIPL impose sector-specific controls, making sovereignty-first architectures critical for organizations in these industries.

.webp)
