Data Tokenization Vs. Encryption: Key Differences
Summarize this article with:
✨ AI Generated Summary
Data tokenization replaces sensitive information with irreversible tokens stored in a secure vault, ideal for structured data like credit cards, enhancing compliance and reducing breach risks. Encryption converts data into unreadable ciphertext using cryptographic keys, suitable for both structured and unstructured data, protecting data in transit and at rest but requiring careful key management.
- Tokenization is faster, format-preserving, and reduces data leakage but depends on vault security.
- Encryption secures data with strong algorithms, supports broader data types, but can be slower and vulnerable if keys are compromised.
- A hybrid approach combines tokenization for storage and encryption for transmission, offering layered security.
- Tools like Airbyte facilitate secure data integration using encrypted channels, credential management, and automation features.
Keeping data safe is a crucial task across many businesses. Two common ways to protect sensitive information are tokenization and encryption. Although both are used for data protection, they serve distinct purposes.
This article explores data tokenization vs. encryption in detail, helping you determine which method best meets your needs.
What Is Data Tokenization?
Data tokenization is a process of replacing sensitive data with a unique, non-sensitive token. These tokens are randomly created strings with no real meaning.
Tokenization is widely adopted in financial and payment systems to secure transactions. According to research by Juniper Research, tokenization is becoming highly essential. This projection indicates that by 2026, tokenization systems will protect one trillion transactions worldwide.
The widespread acceptance of tokenization is due to the fact that there is no mathematical connection between the token and the actual data. As a result, unauthorized individuals cannot restore the original value of the token. This makes the tokenized data both undecipherable and irreversible.
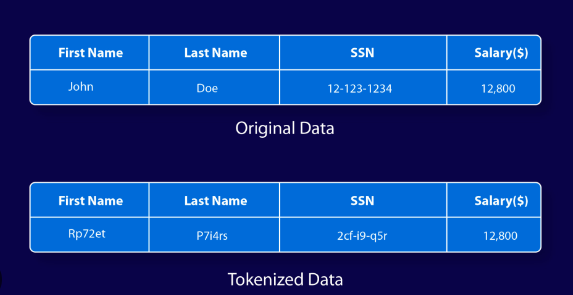
How Does It Work?
When you enter confidential data, such as a credit card number, the tokenization system changes it with a token value.
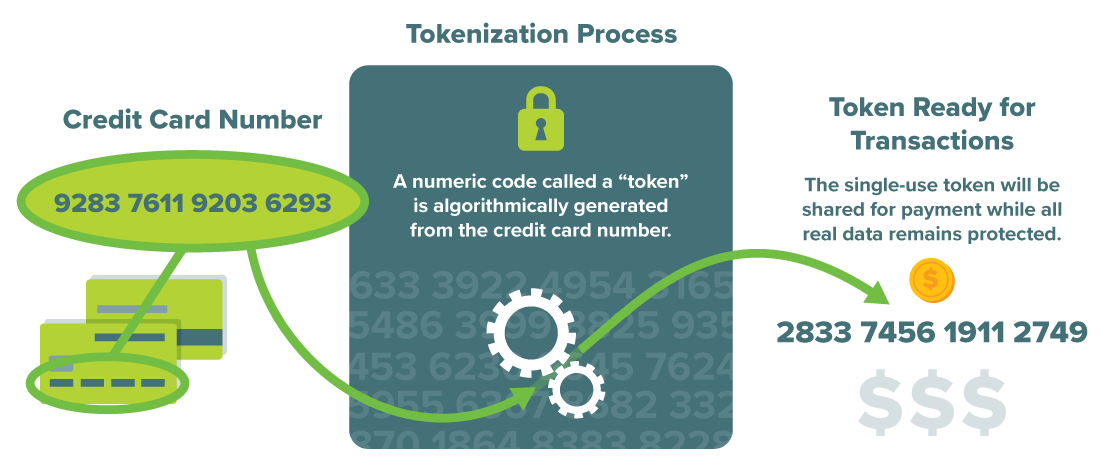
Instead of relying on cryptographic algorithms, the tokenization process uses a secure database known as a token vault. This vault allows you to map each token to its original value while keeping your actual data protected. For additional data privacy, you can encrypt the stored data in the vault.
Pros
- Tokens cannot be reverse-engineered to reveal actual data. If tokens are intercepted, they stay meaningless to attackers. This reduces the risk of data breaches and leakages.
- Use of regulations like PCI, DSS, GDPR, and HIPAA can enforce strict rules on storing and accessing sensitive data. Tokenization helps you meet these standards. As a result, you can minimize large penalties and improve security management.
Cons
- Tokenization has a limited scope. It may not be ideal for multimedia files or unstructured documents. Before implementation, you should assess whether tokenization meets your data protection needs.
- As tokenization depends on the token vault, the whole system is at risk if the vault is harmed. To secure it, you must use strict access controls and encryption.
What Is Data Encryption?
With cyber threats and breaches on the rise, more businesses are adopting encryption to protect sensitive information. In North America, the use of cloud encryption solutions will reach 71.5% by 2033.
Using data encryption, you can convert data into an unreadable format through mathematical algorithms or cryptographic keys. This makes your data useless to anyone without the correct key. In turn, your personal details, financial records, or critical communications stay safe, whether in transit across networks or stored on devices.
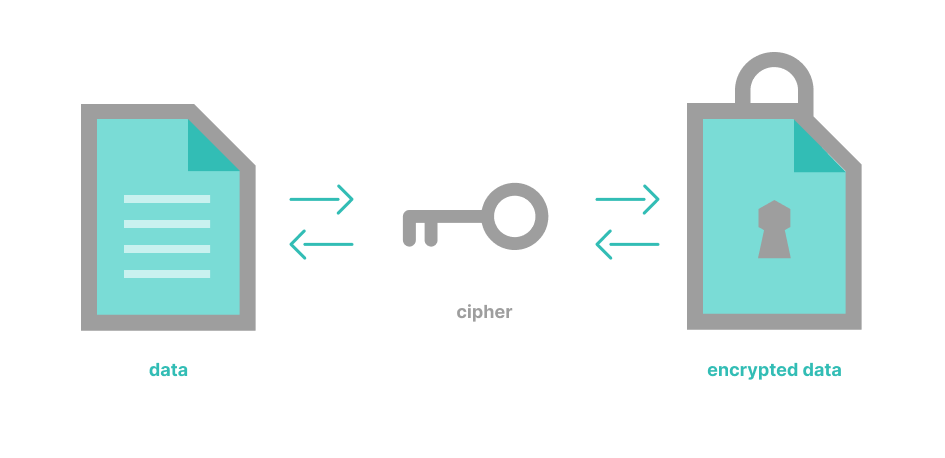
How Does It Work?
The encryption process starts by encrypting required data using an algorithm like AES or RSA.
- AES (Advanced Encryption Standard) is a symmetric approach that uses fixed key sizes (128, 192, or 256 bits) to securely encrypt large data volumes.
- RSA (Rivest-Shamir-Adleman) is an asymmetric algorithm that uses a public-private key pair for encryption and decryption.
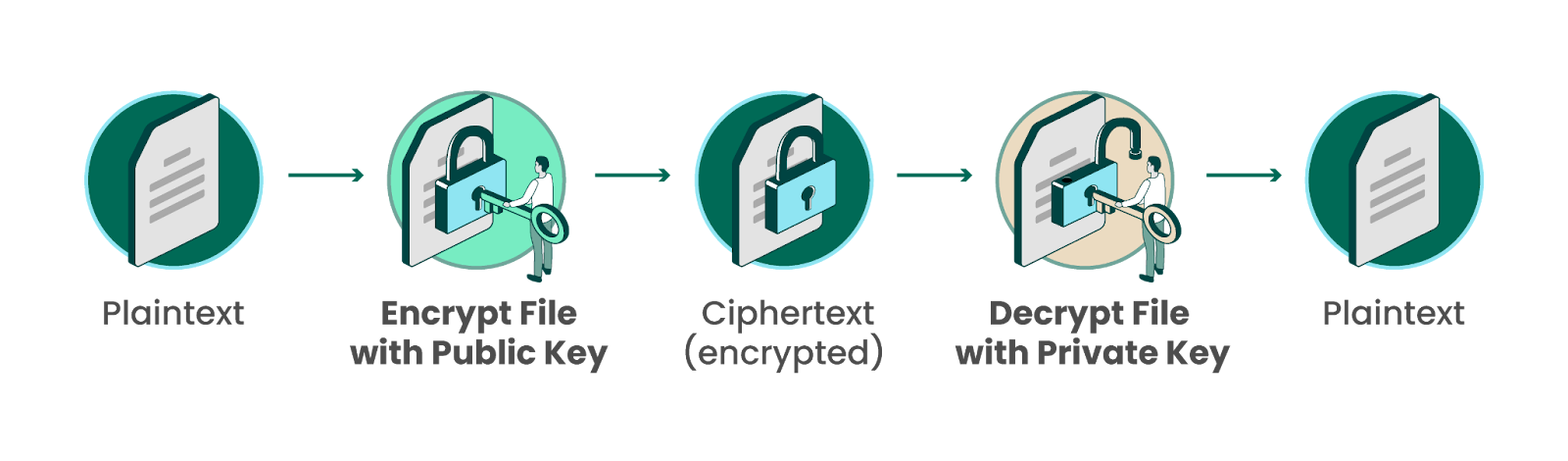
Once the algorithm is applied, the public key enables you to convert the data into ciphertext, making it unreadable. To access the original information, an authorized recipient needs their private key or decryption key to turn the ciphertext back into plaintext.
Pros
- Encryption allows you to keep your data unchanged during transmission by preventing updates from unauthorized individuals. This helps you maintain data accuracy.
- With encryption, you can strengthen multi-factor authentication by protecting stored credentials and authorization tokens. If someone tries to access it, they cannot be read without the right private key.
Cons
- Encryption depends on key storage and management. If encryption keys are lost or stolen, you will not be able to read cipher text. This causes security risks.
- Encryption technique requires a good understanding of mathematical concepts such as modular arithmetic and prime factorization. Without the proper knowledge, weak implementations can make data easy to hack.
Data Tokenization Vs. Encryption
When to Use Data Tokenization?
- For Identity and Access Management (IAM), you can use a tokenization approach. It allows you to authenticate users and control access to protect resources. By creating access tokens, you can grant temporary permissions for your applications or APIs.
- Online retailers can utilize a tokenization process to protect customer payment details. Instead of storing actual credit card numbers, the tokenization technique helps retailers replace them with token values. This minimizes fraud activities and ensures safer transactions.
When to Use Data Encryption?
- You can use encryption to safeguard data stored on devices, cloud storage, and flat files from data breaches. Full-disk and File-level encryption allow you to provide data-at-rest protection. The former enables you to encrypt entire storage devices, such as hard drives and SSDs. In contrast, the latter lets you secure specific files or directories.
- By utilizing encryption, you can secure your intellectual property and trade secrets from unauthorized access. Industries like technology, media, and pharmaceuticals use encryption to secure their proprietary information, research data, and other valuable digital assets.
Data Tokenization Vs Encryption: Would Hybrid Approach Work?
Data tokenization and encryption are two important data obfuscation approaches. Data obfuscation is a way to hide sensitive information so that unauthorized users cannot read or understand it. By combining these obfuscation methods, you will have the flexibility to create a layered security approach. It allows you to improve data security by using the capabilities of both techniques. Let’s see how this hybrid approach works:
- Tokenization for Storage: Initially, you must replace all the sensitive data with tokens using a tokenization system. This must be done before storing it in a database to reduce data exposure.
- Encryption for Transmission: To secure data in transit, you can encrypt its corresponding tokens using cryptography.
- Decryption for Authorized Access: At the receiver end, authorized parties can access original data from the token vault with the help of the recipient's private key.
Here is an example to understand this hybrid approach:
A healthcare provider needs to store and transmit patient data securely. Instead of storing raw medical records and SSNs in their database, they can implement tokenization. This replaces sensitive patient details with unique tokens, which are encrypted during transmission. After implementing the hybrid approach, only authorized individuals like medical administrators can decrypt the tokens using a secure private key. Once decrypted, they can retrieve the required patient details for treatment, billing, or record-keeping.
Secure Data Management with Airbyte
When you transfer sensitive records between internal systems, your data passes through secured channels. While multiple departments receive the file, only authorized persons with the right decryption keys can access its contents. This level of protection is crucial for secure data management. However, manually managing such a complex process can be time-consuming and increase security risks.
A data integration tool like Airbyte enables you to streamline safe data movement across your systems. Its 550+ pre-built connectors let you securely extract data from several sources and transfer it to your preferred storage system.
Most of Airbyte’s native connectors use encrypted channels like SSL, SSH tunnel, and HTTPS to protect your data during transfer. When configuring your connector via Airbyte, you can enable encryption to safeguard your data consolidation workflows.
For extra security, Airbyte supports credential management, role-based access control, compliance certifications, and authentication mechanisms (Bearer Token, OAuth, Session Token).
Here are some of the features of Airbyte:
- Simplify GenAI Workflows: Airbyte supports eight vector databases, such as Pinecone, Weaviate, and Milvus, to streamline GenAI development. These vector stores allow you to store unstructured data in the form of embeddings. To generate these embeddings, Airbyte is compatible with popular LLM providers like OpenAI and Cohere.
- Connector Development with AI Support: Airbyte provides a no-code Connector Builder to build custom connectors for your data integration needs. It comes with an AI assistant feature. This AI support makes connector development simple by automatically filling in the required configuration fields.
- Pipeline Automation Capabilities: With Airbyte, you can reduce the manual effort in data pipeline creation through pre-built connectors and auto-syncs. It also helps you schedule pipelines, replicate incremental changes, and detect schema changes for smooth data integration.
- Developer-Friendly Pipeline: PyAirbyte is an open-source Python library offered by Airbyte. By using Airbyte’s connectors in your Python workflows, PyAirbyte helps you collect data from diverse sources and load it into an internal SQL cache. After processing the gathered data using Pandas libraries or SQL-based tools, you can store it in your destination.
- Data Orchestration: Airbyte lets you integrate with different orchestrator tools, such as Prefect, Kestra, Dagster, and Apache Airflow. Such integration is crucial for automating and managing your data pipelines.
Want to learn more? Connect with Airbyte’s experts to explore how it can support your data management needs.
Conclusion
As data security risks grow, protecting sensitive data is more important than ever. Tokenization keeps financial transactions safe, while encryption protects end-to-end messaging. Each method has its own advantages. By understanding this guide on data tokenization vs. encryption, you can choose the best option based on your organization’s needs.

