7 Essential Use Cases for Hybrid Deployment Models
Summarize this article with:
✨ AI Generated Summary
Hybrid deployment models separate cloud-based control planes from customer-controlled data planes, enabling cloud elasticity while keeping sensitive data on-premises to meet strict compliance requirements like HIPAA and GDPR. Key benefits include:
- Regulatory compliance with local data residency and sovereignty mandates
- Low-latency, real-time processing by colocating data planes near data sources
- Unified orchestration with outbound-only connectivity and external secrets management for enhanced security
- Use cases span healthcare, finance, manufacturing, telecom, government, retail, and SaaS, addressing challenges like data residency, latency, and vendor lock-in
- Hybrid models reduce operational overhead and costs compared to pure cloud or on-premises setups while supporting AI and advanced analytics securely
Your data team deploys to the cloud for speed and scale, but regulatory requirements force everything back on-premises. Or you build on-premises for compliance, then struggle with the operational overhead of maintaining infrastructure.
Hybrid deployment solves this daily contradiction. You get cloud orchestration paired with customer-controlled data planes without compromising on compliance.
The real test isn't theoretical. Healthcare systems need HIPAA-safe analytics without losing elasticity. Banks require cross-border data residency while maintaining millisecond fraud detection. Telecom networks process petabyte-scale CDRs that can't leave the premises.
The seven use cases ahead show exactly how hybrid deployments handle these constraints, with technical patterns you can implement immediately.
What Are Hybrid Deployment Models?
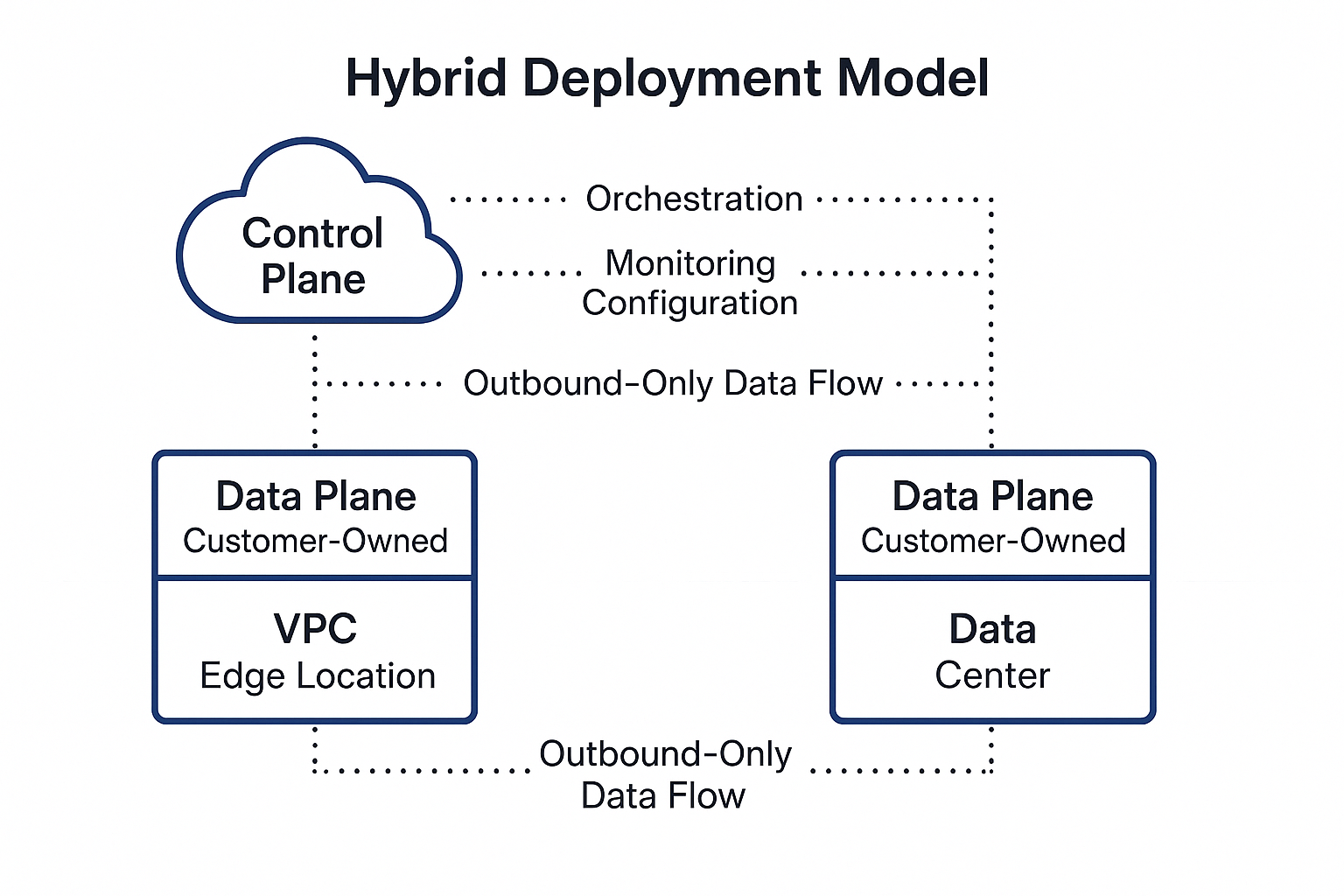
A hybrid deployment (the foundation of hybrid cloud computing) separates your control plane from your data planes. The control plane runs in the cloud and handles orchestration, monitoring, and configuration. Your data planes run inside your VPC, data center, or edge location wherever your data needs to stay. This means you get cloud elasticity without your sensitive data ever leaving environments you control.
Airbyte Enterprise Flex works exactly this way. Same 600+ connectors, same performance, but your data never leaves your environment.
This comparison highlights why hybrid cloud computing architectures are now the default choice for regulated data workflows:
This architecture uses existing cloud services while avoiding the "all or nothing" choice between public cloud and on-premises infrastructure. Hybrid deployments let you keep regulated datasets local without losing managed tooling.
Making this work requires three technical components:
- Outbound-only connectivity so firewalls never accept unsolicited ingress
- External secrets management that stores credentials outside both planes
- Unified orchestration that applies a single configuration across every region and environment
With these pieces in place, you orchestrate pipelines from the cloud while your data stays exactly where compliance teams need it under your direct control.
Why Are Hybrid Deployment Models Gaining Momentum?
The shift from pure cloud or on-premises strategies is accelerating because hybrid cloud tech solves a fundamental tension: keeping sensitive data where regulations demand while still scaling like the cloud. Instead of choosing between control and agility, you get both.
Four forces are driving this transformation:
- Data sovereignty mandates like HIPAA in the U.S., GDPR across Europe, and the emerging EU DORA framework require you to ensure that regulated data is protected and compliant with local regulations, especially when transferred across borders.
- Analytics and AI workloads span regions, making it essential to colocate data planes near each dataset while avoiding risky exports.
- Low-latency expectations in healthcare dashboards, trading systems, and factory floors punish any architecture that waits on long round-trips to a single cloud region.
- Vendor lock-in avoidance drives teams to mix on-premises, private, and multiple public clouds to keep options open when prices rise or features lag.
Pure deployment strategies no longer match where your data actually lives. The hybrid approach meets infrastructure where it is and provides elasticity where you need it most.
What Are 7 Essential Use Cases for Hybrid Deployment Models?
Hybrid deployment is the practical answer to strict regulations, unpredictable workloads, and the reality that sensitive data still lives on-premises. The seven scenarios below come straight from teams wrestling with compliance and latency every day. Each shows how a cloud-hosted control plane paired with customer-owned data planes solves a different, high-stakes problem.
1. Healthcare: HIPAA-Compliant Data Integration
Protected Health Information can't float through public regions without proper safeguards. Hospitals keep PHI inside HITRUST-certified networks while a cloud control plane schedules syncs over outbound-only connections.
Business Associate Agreements are standard requirements. The harder part is unified audit logging that tracks every read or write across both environments, a gap that hybrid architectures close by default. With data remaining local, encryption keys stay on-premises, satisfying HIPAA's security rule.
The result is immediate: EHR dashboards refresh in under a minute instead of the two-hour delay common with legacy ETL tools, and security teams complete audits efficiently because PHI never left their firewall.
2. Financial Services: Cross-Border Data Residency
A European bank cannot ship transaction records to a U.S. region without violating GDPR, yet its fraud models demand sub-30-second change data capture lag.
By deploying regional data planes inside each jurisdiction and directing orchestration from a single cloud control plane, the bank proves that customer data never traverses borders while still sharing anonymized features globally. Column-level lineage, signed and time-stamped, gives auditors the evidence they need for EU DORA reviews.
This approach also clarifies the shared responsibility boundaries: the provider secures the control plane, but encryption keys and network policies remain in the customer's hands.
3. Manufacturing & ERP: Real-Time SAP Replication
Plant floors run 24x7. Locking an SAP table for export can halt production. Manufacturers avoid that risk by running CDC agents next to their ERP databases, pushing only the deltas through secure outbound tunnels.
The cloud control plane handles scheduling and retries, but it never touches raw operational data. Because compute bursts happen off-site, the local cluster focuses on millisecond-level shop-floor queries while terabyte-scale logs flow to a lake for global analytics.
This pattern of local capture with remote orchestration originated when teams realized legacy ETL couldn't keep pace with IoT telemetry.
4. Telecom: Sovereign Edge Data Processing
Telecom operators generate billions of call detail records that national regulators can subpoena at any moment. The hybrid approach lets them run data planes at the network edge, sometimes inside regional switching facilities, while the control plane lives in a neutral cloud region.
Because CDRs never leave sovereign soil, lawful intercept rules stay intact. Edge clusters pre-aggregate traffic so only metadata, not personal identifiers, flows upward for capacity planning. Low latency is non-negotiable, and keeping compute close removes the round-trip delay.
5. Government & Defense: Air-Gapped or ITAR-Controlled Data
Defense contractors can't expose munitions data to public infrastructure. Their answer is a private control plane running inside a classified enclave with no inbound traffic allowed.
Data planes mirror across multiple secret networks, each logging every packet for continuous FISMA monitoring. FedRAMP-authorized components plug into the same orchestration APIs, so workflows look identical whether the engineer is in a secure room or at an unclassified site.
This approach aligns with zero-trust guidance while meeting ITAR requirements and maintaining automated CI/CD pipelines.
6. Retail & Logistics: Regional Data Synchronization
Payment information collected at point-of-sale terminals in Berlin must stay in the EU, while the same retailer's inventory system needs a unified global view.
The hybrid model separates those concerns: EU-based data planes keep cardholder data local to satisfy PCI and GDPR, while product and supply chain tables replicate to a cloud warehouse every few minutes for worldwide replenishment forecasting.
Because the control plane coordinates all jobs, dev teams write one pipeline definition that adapts to each region's sovereignty rules. The result is near real-time stock accuracy without the legal risk of exporting PII.
7. Technology & SaaS: Multi-Cloud Integration
A SaaS provider selling to both U.S. healthcare firms and Swiss banks can't force everyone into the same region or even the same cloud.
Instead, it spins up customer-specific data planes, AWS in Ohio for HIPAA clients and Azure in Zürich for FINMA users, while a single control plane delivers upgrades and monitors health. Because all deployments run identical codebase, feature rollout happens once, not per region.
This neutralizes vendor lock-in and gives sales teams a direct answer to "Where will my data live?" without sacrificing operational consistency.

How Do Hybrid Deployment Models Enable AI and Advanced Analytics?
These architectures keep sensitive data inside your firewall while accessing cloud compute resources for model training and inference. By running the control plane in the cloud and the data plane on-premises, you orchestrate pipelines centrally while ensuring raw data never crosses compliance boundaries.
A common implementation pattern involves pre-processing and anonymizing PHI or payment events locally, then sending only feature vectors or aggregated results to the cloud for large-scale training. When inference completes, predictions stream back through the same outbound-only channel, so no inbound holes are opened.
Real-world AI implementations show the practical impact:
- Healthcare teams report sub-minute imaging classification while maintaining HIPAA compliance.
- Financial services generate fraud scores within regional banking clusters without cross-border data transfer.
- Manufacturing companies run predictive maintenance models at factory edge locations that learn from global fleet data.
Airbyte Flex supports these AI workflows by moving both structured and unstructured data across deployment boundaries with 600+ connectors and consistent performance across all environments.
What Common Patterns Do These Use Cases Share?
Every successful deployment, whether in healthcare or telecom, follows the same architectural playbook. The goal is simple: keep sensitive data under your control while still enjoying cloud elasticity and speed.
Outbound-Only Data Plane Traffic
This keeps your firewalls closed to inbound calls, reducing attack surface while still letting the cloud control plane issue jobs. You get cloud orchestration without exposing internal systems.
Regional Data Planes
Match jurisdiction boundaries, satisfying data residency and sovereignty requirements under GDPR and HIPAA. Each region processes its own sensitive data locally while contributing to global insights through the control plane.
External Secrets Management
Pervasive encryption protects credentials and payloads end-to-end. Store secrets outside both planes to maintain separation of concerns and satisfy audit requirements.
Unified Orchestration
Provides one dashboard for pipelines across clusters, minimizing configuration drift and manual maintenance. Teams manage everything from a single interface regardless of where data actually lives.
Compliance-First Design
Treats audits as a design input, not an afterthought. When you combine these patterns, you balance control, security, and scalability without trading off speed of innovation.
Together, these shared patterns form the foundation of modern hybrid architectures, creating systems that adapt to any compliance boundary without slowing down data-driven innovation.
How Can You Choose the Right Hybrid Deployment Model?
Regulated data, latency targets, and cost controls rarely align neatly, so you need a framework that balances them without guesswork.
Start by documenting every mandate first. Map HIPAA, GDPR, or PCI obligations to specific datasets to avoid retroactive fixes. Classify data by risk, separating PHI, PII, and operational telemetry so encryption scope becomes obvious once you label sensitivity. Chart data flows across borders by visualizing which tables, streams, or files cross regions so residency gaps surface early.
Choose your control plane location carefully. Keep orchestration in the cloud unless sovereignty rules demand on-premises deployment. Validate vendor primitives by requiring outbound-only networking, external secrets, and audit logging before signing contracts.
Finally, start small and propagate. Pilot a low-risk pipeline first. With Airbyte Enterprise Flex, the same 600+ connectors follow you from lab to production with no rewrites, just redeployment.

How Do You Get Started with Hybrid Deployment?
Enterprise data teams face conflicting demands that pure cloud or on-premises deployments can't resolve. Hybrid architectures provide cloud orchestration with data sovereignty, elastic scale without compromising governance. Airbyte Enterprise Flex delivers HIPAA-compliant hybrid architecture, keeping ePHI in your VPC while enabling AI-ready clinical data pipelines. Talk to Sales to discuss your hybrid deployment requirements.
Frequently Asked Questions
What is the difference between hybrid and multi-cloud deployments?
Hybrid deployment connects your on-premises infrastructure with cloud resources through a unified control plane. Multi-cloud uses multiple public cloud providers without necessarily connecting to private infrastructure. You can combine both approaches where data planes span AWS, Azure, and your data center while a single control plane orchestrates everything. Airbyte Flex supports this unified architecture across all environments.
How do hybrid deployments handle disaster recovery?
Hybrid architectures enable flexible disaster recovery strategies because you control where backup data planes run. You can replicate from on-premises to cloud for off-site protection, mirror across multiple regions for geographic redundancy, or maintain hot standby clusters that activate when primary sites fail. The cloud control plane continues orchestrating regardless of which data plane serves requests, so recovery automation doesn't depend on manual failover.
Can hybrid deployments reduce costs compared to full cloud?
Cost depends on your specific workload patterns. Hybrid deployments reduce cloud egress fees by processing data where it originates rather than moving everything to remote regions. You also avoid overprovisioning on-premises hardware because cloud data planes handle burst capacity. However, you maintain some infrastructure overhead. Organizations typically see 60-80% infrastructure cost reduction when moving from legacy ETL platforms to hybrid architectures because unified orchestration eliminates duplicate tooling.
What security considerations are unique to hybrid deployments?
Hybrid architectures require careful network segmentation because you're connecting environments with different security controls. Use outbound-only connections from data planes to control plane so you never open inbound firewall rules. Store credentials in external secrets managers rather than embedding them in either plane. Implement column-level encryption for data moving between environments, and maintain separate audit logs in each jurisdiction to satisfy local compliance requirements. The split architecture actually improves security posture by limiting where sensitive data can travel.

.webp)
