Azure Hybrid Deployment Options: Best Practices
Summarize this article with:
✨ AI Generated Summary
Azure hybrid deployments address regulatory, latency, and compliance challenges by combining on-premises and cloud resources using secure architectures like hub-and-spoke networks with ExpressRoute and Private Link. Key strategies include:
- Unified identity management with Azure AD Connect and Azure Arc for consistent security and policy enforcement across environments.
- Automated infrastructure deployment using IaC tools (Bicep, Terraform) and Azure Blueprints to prevent configuration drift and ensure compliance.
- Data integration patterns supporting sovereignty, such as Azure Data Factory, Azure Arc-enabled Data Services, and Airbyte Enterprise Flex’s outbound-only architecture for strict data control.
- Comprehensive monitoring with Azure Monitor and Defender for Cloud to unify threat detection and cost management across hybrid estates.
- Avoidance of common pitfalls like over-centralization, inconsistent identity controls, open inbound ports, mixed IaC approaches, and lack of cost monitoring.
Your compliance team approved Azure for analytics, but production databases can't leave the datacenter. GDPR auditors want proof EU customer data stays in Frankfurt. Manufacturing control systems need a sub-10ms response that cloud round-trips can't guarantee.
Almost every enterprise runs hybrid deployments by necessity, not choice. Yet connecting Azure Arc, Stack HCI, Private Link, and ExpressRoute creates real operational complexity. Teams spend weeks debugging network paths, months aligning security policies, and quarters proving compliance to auditors who don't understand hybrid architectures.
This guide covers architecture patterns, governance frameworks, and data movement strategies that work across healthcare startups and global banks.
What Problems Do Azure Hybrid Deployments Solve?
Azure hybrid architecture addresses three observable constraints that force split deployments rather than pure cloud migration.
Regulatory Frameworks Create Hard Boundaries
GDPR doesn't mandate on-premises technically, but requires data handling within legal jurisdictions that cloud-only solutions can't always guarantee. HIPAA creates similar constraints around protected health information. Healthcare organizations face this daily: clinical databases respond in under one second for bedside terminals while audit trails prove records never crossed borders.
Manufacturing Environments Compound the Latency Problem
Factory floor systems controlling robotic arms or chemical processes can't tolerate network delays. ERP databases running SAP or Oracle on specialized hardware aren't moving to the cloud. Those systems generate massive log volumes that choke when replicating over WAN links.
Financial Services Teams Report Observable Failures
Fraud detection models fail when the CDC lag exceeds 30 seconds during trading hours. Cross-border operations need data inside regional datacenters. Internal audit wants cryptographically verifiable lineage that legacy tools can't provide.
These aren't theoretical constraints. They're observable requirements driving hybrid adoption across regulated industries.
How Should You Design Azure Hybrid Network Architecture?
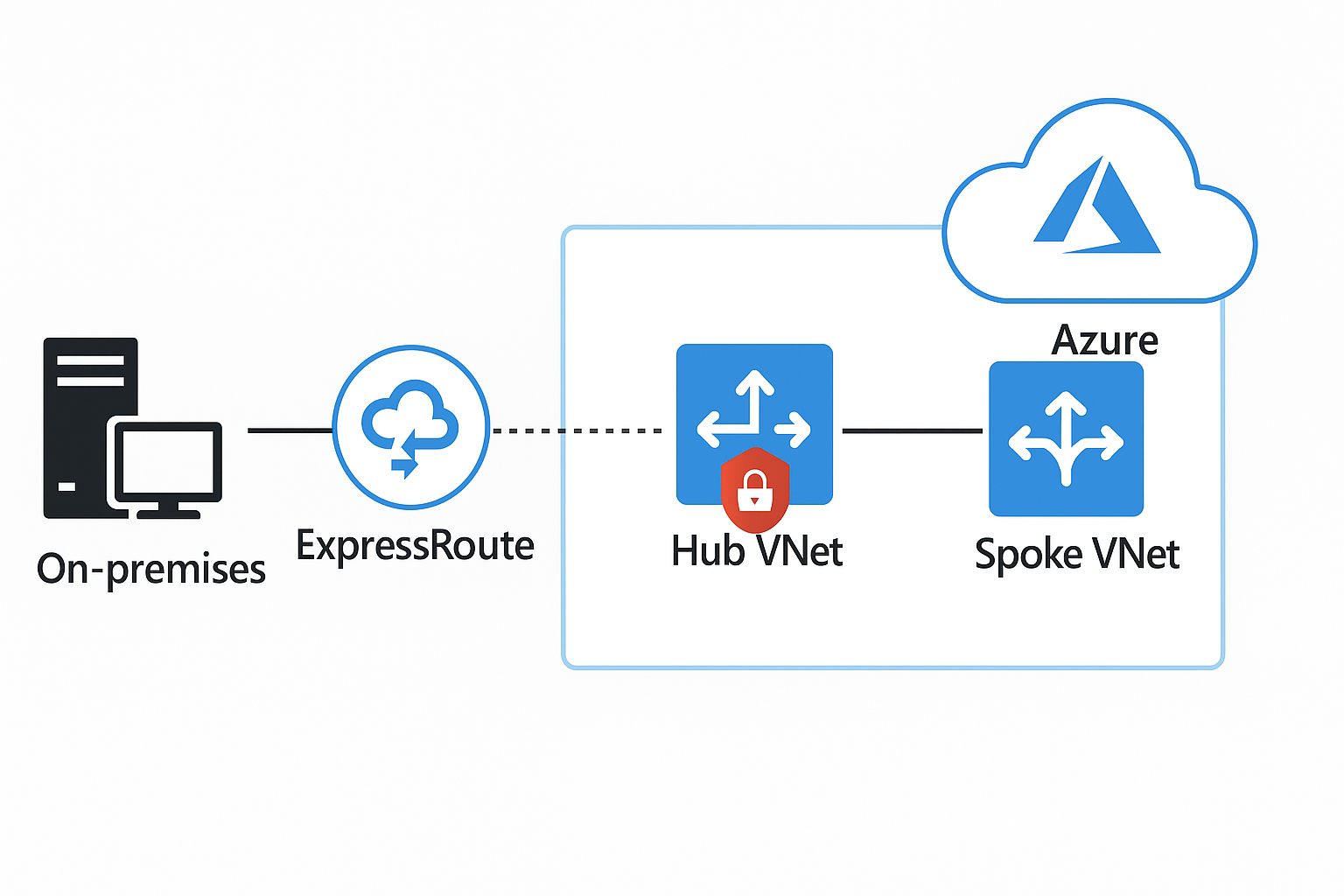
Designing a secure and compliant hybrid network in Azure starts with the right foundation. Your architecture should balance performance, visibility, and data protection, ensuring auditors see clear boundaries and your workloads stay reliable under pressure.
Build a Secure Hub-and-Spoke Foundation
Network topology determines audit approval or compliance flags. Hub-and-spoke design provides the foundation: a central hub VNet in Azure connects to on-premises datacenters through ExpressRoute private circuits.
Use ExpressRoute for Private, Predictable Connectivity
ExpressRoute delivers dedicated network paths bypassing the public internet. Production traffic flows through private circuits with predictable latency and bandwidth. Configure multiple circuits across diverse paths so failures don't take down your hybrid estate.
Layer Security Controls at Every Boundary
Security controls layer at every boundary. Deploy Azure Firewall in the hub VNet as a centralized inspection point. Every spoke VNet routes through this firewall, creating a single enforcement location. Add network security groups on subnets for defense in depth.
Connect Privately with Azure Private Link
Private Link endpoints let Azure services reach on-premises resources without internet exposure. SQL Managed Instance in Azure connects to datacenter databases through private endpoints that auditors verify never touch public networks.
What Identity Controls Work Across Hybrid Environments?
Identity sprawl creates security gaps that attackers exploit daily. The solution starts with unified authentication but maintains separate privilege management across boundaries.
Synchronize on-premises Active Directory with Entra ID using Azure AD Connect. Users authenticate once, but manage role-based privileges separately in each environment to maintain security boundaries.
Conditional Access policies enforce rules consistently:
- Block sign-ins from risky locations
- Require MFA for administrative roles
- Time-box elevated privileges through Privileged Identity Management
Configure sign-in logs flowing to Azure Monitor for audit trails showing who accessed resources and when. Compliance teams need immutability beyond basic logging, so add retention policies and log forwarding for specific regulatory requirements.
Azure Arc extends identity controls to on-premises servers. Registered machines appear in the Azure control plane. Apply the same RBAC policies, Conditional Access rules, and security monitoring to datacenter servers as Azure VMs.
Manufacturing companies manage edge locations this way. Factory floor systems register with Arc, inherit centralized policies, and keep operational data local for latency.
How Do You Maintain Compliance Across Environments?
Azure Policy declares rules for auditing cloud resources and Arc-registered servers. The policies "All storage must use encryption" and "only EU regions allowed" trigger alerts or automatic remediation when drift occurs.
Bundle policies with RBAC assignments and ARM templates inside Blueprints. Every subscription inherits the same baseline. The security team defines standards once, and enforcement happens automatically.
Tag every resource with owner, cost center, and compliance scope. Tags prove to auditors which systems handle regulated data. Generate cost reports per regulatory boundary, and track which teams own specific workloads.
Network segmentation reinforces compliance boundaries:
- HIPAA workloads terminate inside healthcare VNets with their own NSGs and firewall rules
- GDPR data stays in EU regions with policies preventing cross-region replication
- Map every data flow to regulatory requirements before deployment
Defender for Cloud provides unified threat detection and monitoring of Azure resources, Arc-registered servers, and hybrid network traffic. When compliance forbids raw log export from on-premises, forward only security events to SIEM while retaining full logs locally for forensics.
What Data Integration Patterns Support Hybrid Compliance?
Most hybrid deployments fail at the data layer. Databases stay on-premises for sovereignty, but analytics need cloud compute. Batch windows that worked five years ago no longer meet real-time insight requirements.
Three architectural approaches place control and data planes differently, with direct compliance implications.
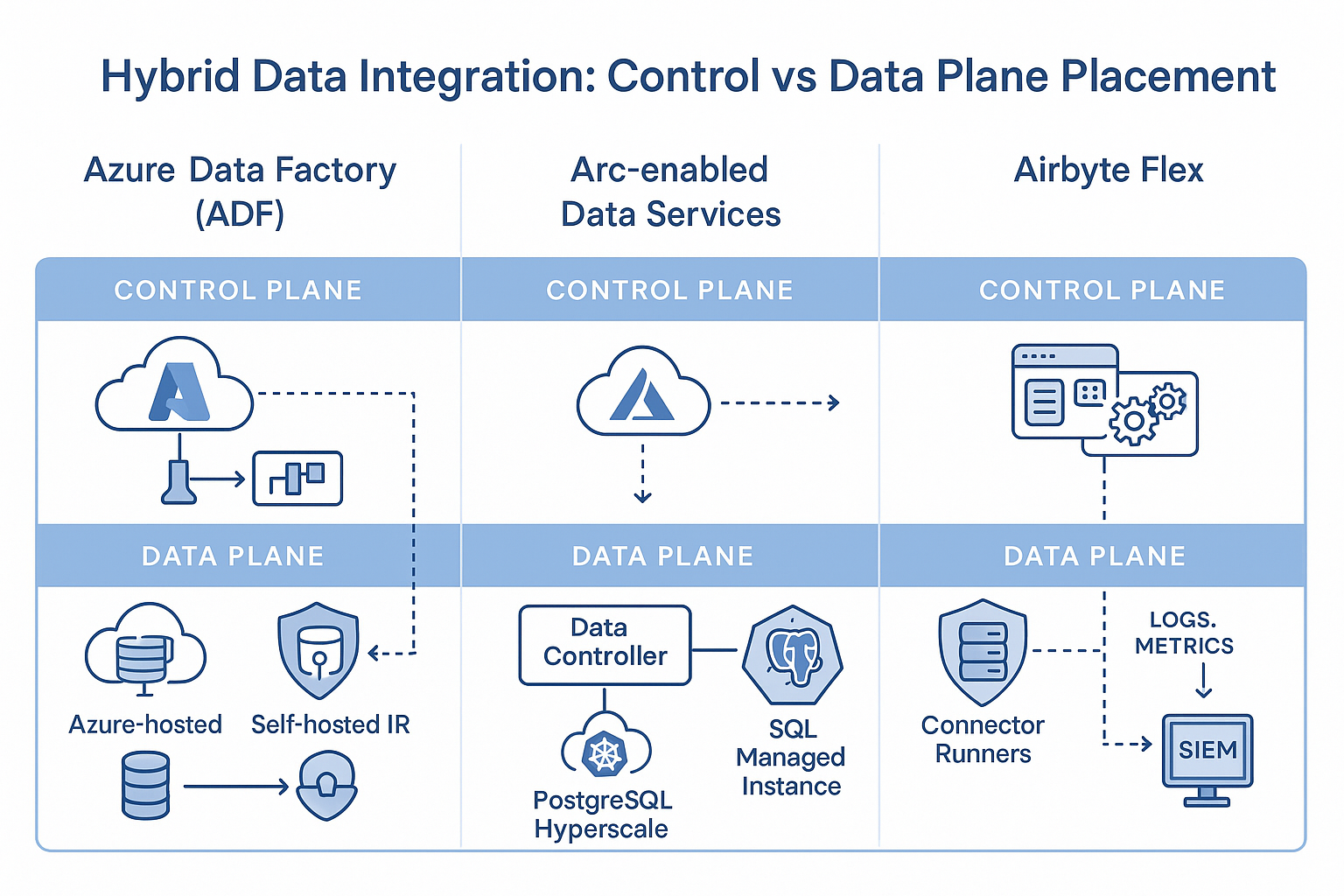
1. Azure Data Factory with Self-Hosted Integration Runtime
ADF pushes orchestration into the cloud while agents inside the datacenter handle movement. Works for scheduled batch pipelines but routes metadata through Microsoft regions. Add Private Link to keep transfers off the public internet.
Best for: Teams comfortable with batch workloads and metadata in Azure regions.
2. Azure Arc-Enabled Data Services
Arc treats on-premises databases as Azure resources. Register SQL Managed Instance or PostgreSQL under Arc control. Data processing stays in the facility with cloud management tools.
Best for: Latency-sensitive workloads where millisecond response matters and data must stay local.
3. Outbound-Only Architecture (Airbyte Enterprise Flex)
In Airbyte Cloud, the hybrid control plane allows data pipelines to execute inside your VNet or datacenter. Traffic flows in one direction out. Auditors see no open ports. You maintain full custody of regulated datasets.
Best for: Strict sovereignty requirements with 600+ connector needs and zero inbound traffic rules.
Healthcare organizations deploy outbound-only for PHI requirements. Clinical data never leaves hospital networks, yet teams build AI-ready pipelines feeding Snowflake for research.
Financial services use this for real-time fraud detection. Transaction databases stay in regional datacenters meeting GDPR. Models in Azure process streaming data through private circuits with verifiable audit trails.
How Do You Automate Infrastructure Deployment?
Manual configuration creates drift compliance audits that catch immediately. Azure environment has one set of rules, on-premises different configurations, and no one explains discrepancies.
Codify infrastructure in Bicep or Terraform. Store templates in Git. Deploy through CI/CD pipelines to both Azure and on-premises. Every change goes through the same review with automated validation.
ARM and Bicep work for native Azure resources. Terraform excels in provisioning VMware VMs, network devices, and Azure services from same codebase. Gate every pull request with validation catching policy violations before production.
Azure Blueprints package policies, RBAC, and templates together. New subscriptions inherit the baseline automatically. Security defines standards once, and enforcement scales across the organization.
This prevents infrastructure snowflakes from plaguing hybrid estates. Every environment starts from the same template. Drift shows in automated scans. Compliance verifies controls through code review rather than manual inspection.
What Monitoring Controls Work Across Hybrid Estates?
Fragmented monitoring creates blind spots attackers exploit. The solution requires unified observability, treating all resources equally regardless of location.
Enroll all resources in Azure Monitor and Log Analytics, including Arc-registered machines in the datacenter. Metrics and logs flow to a centralized workspace, correlating events across environments.
Defender for Cloud applies threat detection uniformly:
- Scans Azure VMs, Arc servers, network traffic, and container workloads
- Same security rules and alerts everywhere
- No separate tools for cloud versus on-premises
Alert rules catch security events and operational issues before business impact:
- When CDC lag exceeds thresholds, alerts fire before dashboard delays
- When privileged access attempts from an unusual location, security gets notified immediately
- When network egress spikes, teams see cost problems early
Cost telemetry matters as much as security. Tag resources with the environment and the owner. Export cost data to Log Analytics. Set alerts when egress or compute exceeds budget. Hybrid deployments hide costs in ExpressRoute utilization and cross-region transfers.
Telecom companies processing billions of CDRs daily configure alerts when volume spikes risk capacity. Network operations see the same dashboards whether systems run in Azure or on-premises.
What Mistakes Derail Azure Hybrid Deployments?
Same errors appear across failed projects regardless of industry or size. Avoid these five patterns derailing hybrid success.
1. Over-Centralizing Orchestration
Forcing every API call through a single region drives up latency and bandwidth while creating a single failure point. Register servers with Arc instead for local management with global policy enforcement.
2. Ignoring Identity Parity
Leaving gaps where legacy apps bypass MFA or RBAC lets users authenticate differently across environments. Attackers exploit inconsistencies. Sync on-premises directories with Entra ID, extend Conditional Access everywhere.
3. Opening Inbound Firewall Rules
Exposing ports for data movement creates audit problems. Compliance flags exposed ports immediately. Use outbound-only patterns where the data plane initiates connections, eliminating the attack surface while maintaining functionality.
4. Mixing Infrastructure-as-Code Approaches
ARM templates here, manual scripts there, guarantees configuration drift. Pick Terraform or Bicep, standardize across environments, and run everything through CI/CD for consistency.
5. Neglecting Cost Monitoring
Discovering egress charges months later, when bills arrive, blinds you to spending. Tag resources from day one, configure cost alerts, and export usage to Log Analytics for analysis.
These mistakes appear consistently across customer deployments. Teams
avoiding them early prevent technical debt from compounding over time.
How Does Airbyte Enterprise Flex Support Azure Hybrid Data Integration?

Data sovereignty requirements don't disappear when you need modern analytics. You need to move data from on-premises to cloud warehouses while proving to auditors that sensitive information never crossed boundaries.
Airbyte Enterprise Flex provides a hybrid control plane architecture designed for compliance-heavy environments. Control plane runs in Airbyte Cloud, handling orchestration and monitoring. Data plane executes inside your VNet or datacenter using outbound-only connections.
This separation means production data never touches external infrastructure. You get 600+ connectors with the same quality across all deployment models. Healthcare teams replicate EHR systems to Snowflake while keeping PHI inside hospital networks. Financial services process transactions meeting GDPR without compromising regional sovereignty.
The platform handles CDC replication without locking production tables. Manufacturing companies extract from SAP and Oracle during 24/7 operations. Parallel processing moves terabyte-scale datasets over private circuits with automatic retry and error handling.
Talk to our sales team to see how Airbyte Enterprise Flex handles data sovereignty in hybrid Azure deployments without compromising connector capabilities or deployment flexibility.
Frequently Asked Questions
What is the difference between Azure Arc and Azure Stack?
Azure Arc extends the Azure control plane to on-premises and multi-cloud resources. You register existing servers, Kubernetes clusters, or data services with Arc, managing them through the Azure portal. Azure Stack provides Azure services running entirely in a datacenter as integrated hardware and software. Arc manages what you already own, Stack deploys Azure infrastructure on-premises.
How does ExpressRoute improve hybrid deployment security?
ExpressRoute creates private network circuits between the datacenter and Azure, bypassing the public internet. Traffic flows through dedicated connections with predictable bandwidth and latency. This satisfies compliance requirements for data-in-transit protection and reduces attack surface, eliminating exposure to internet-based threats. Combine ExpressRoute with Private Link for end-to-end private connectivity.
Can you use Azure Policy to enforce compliance on-premises?
Yes, through Azure Arc. Register on-premises servers or Kubernetes clusters with Arc, then Azure Policy evaluates them using the same rules as cloud resources. Declare requirements like "all servers must have security agents" or "only approved extensions allowed," and Arc applies policies to registered machines. Policy compliance reports show drift across the hybrid environment.
What data integration tools work with strict sovereignty requirements?
Tools using an outbound-only architecture where the data plane initiates all connections from inside your network. Azure Data Factory with self-hosted integration runtime supports this pattern. Airbyte Enterprise Flex provides a hybrid control plane with data movement happening entirely within your VNet or datacenter. The key requirement is eliminating inbound firewall rules while maintaining full connector functionality across deployment models.

.webp)
