Exit Strategy Requirements: EU DORA Compliance for Data Platforms
Summarize this article with:
✨ AI Generated Summary
DORA mandates that EU financial institutions maintain legally compliant exit strategies for ICT providers, emphasizing documented transition periods, data portability with functional equivalence, and audit-ready evidence. Key requirements include:
- Contracts specifying adequate transition timelines and audit rights
- Regular testing and documentation of data migrations to prove operational resilience
- Open, interoperable data formats and deployment flexibility to avoid vendor lock-in
- Direct regulatory oversight for critical providers with severe penalties for non-compliance
Implementing these exit plans involves overcoming technical and contractual complexities, continuous governance, and proactive testing to ensure seamless provider transitions without data loss or downtime.
Your cloud data platform fails mid-quarter during a regulatory audit. Under the EU's Digital Operational Resilience Act (DORA), now in full force since January 2025, you must prove that you can switch providers or pull workloads in-house without missing a beat.
Article 28 makes exit planning a legal obligation within ICT risk management, generally requiring documented plans and continuity measures, but does not explicitly mandate documented transition periods, data portability, or audit-ready evidence packs as discrete requirements.
Non-compliance carries steep costs. ICT providers face direct European Supervisory Authority oversight and can be barred from serving financial institutions, while firms that rely on them risk fines and regulatory scrutiny linked to global turnover. DORA's compliance framework mirrors GDPR's enforcement approach, with penalties that scale with organizational impact.
Data teams at regulated firms are scrambling to untangle proprietary APIs, scattered pipelines, and hidden SaaS dependencies while building realistic exit roadmaps, making exit strategy readiness the current frontline of operational resilience.
What Does EU DORA Require Around Exit Strategies?
DORA treats an exit plan as a core control. Article 28 emphasizes exit readiness as part of third-party risk management. Before you sign or renew any contract, you should have documented assurances that the provider can export data in a usable format, cooperate during transition, and remain available long enough for migration.
Regulators may request evidence of such assurances, which often includes details on notice procedures, transition timelines, and audit logs, although the regulation does not prescribe specific formats or contents for such documentation.
The stakes are high. Supervisory authorities can bar a non-compliant "critical" provider from serving EU financial institutions, and penalties can be substantial, though they do not strictly mirror GDPR's percentage-of-turnover fines. The EU Data Act, which outlaws exit fees from 2027 and strengthens legal leverage for data portability and open interfaces, makes this even more critical for helping you avoid vendor lock-in.
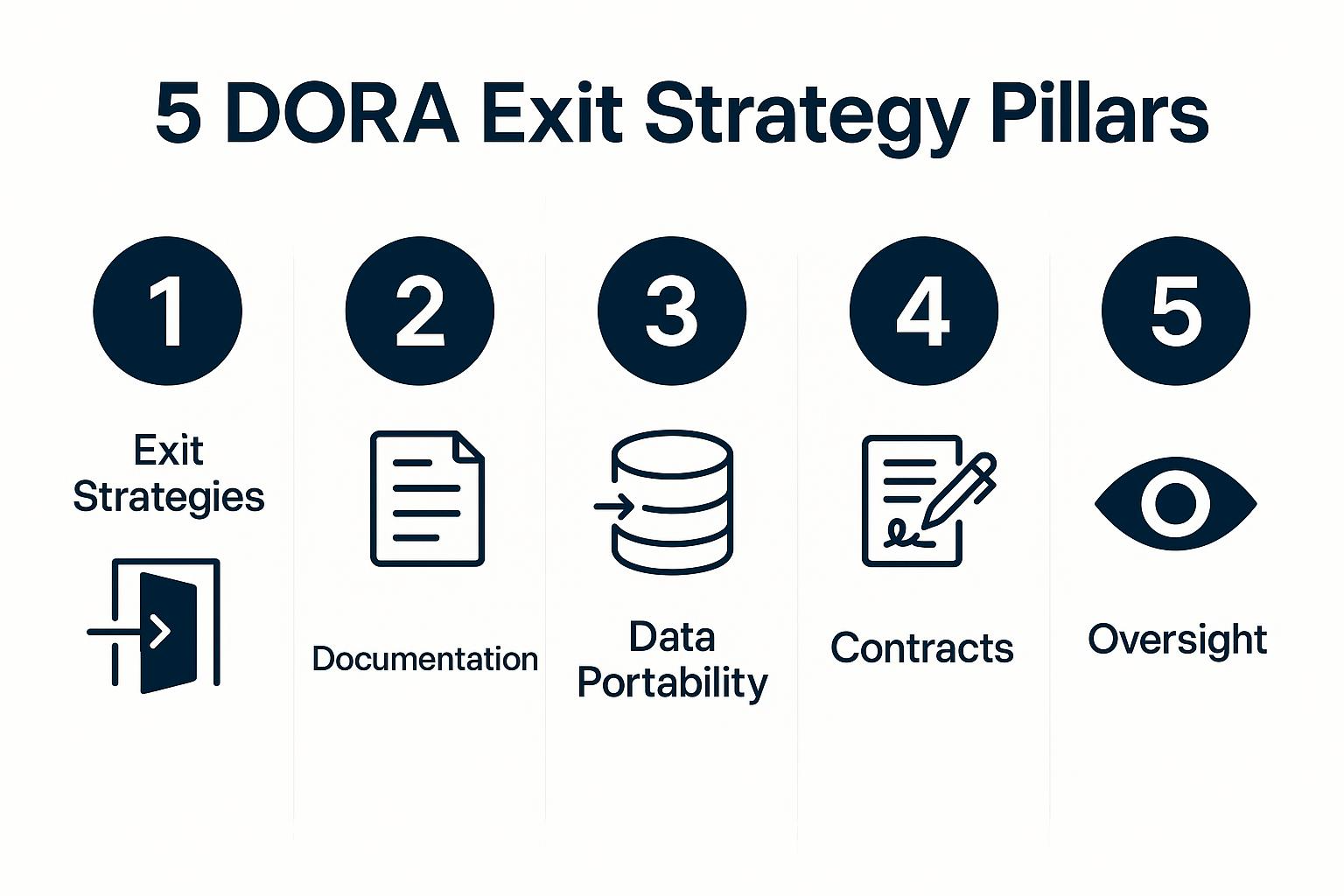
Your exit plan must demonstrate five specific capabilities:
1. Mandatory Exit Strategies with Defined Transition Periods
Contracts must spell out how long the provider will maintain service after notice so you can migrate safely, and the timeline has to be "adequate" for the volume and criticality of data you hold.
2. Evidence Documentation and Testing
A regulator can request your "evidence pack" at any moment. It needs to show notice procedures, retrieval windows, and successful functional-equivalence tests for past migrations.
3. Data Portability and Exportability with Functional Equivalence
You must demonstrate that exported data and applications will work the same way on the new platform. Open interfaces and interoperable schemas are explicitly encouraged.
4. Specific Contractual Provisions
Required clauses include audit and access rights, subcontractor visibility, data-localization assurances, and clear termination notice periods.
5. Regulatory Oversight and Direct Supervision
If a provider is deemed "critical," it falls under direct ESA supervision. Non-compliance can trigger bans on doing business with EU financial firms.
These five pillars turn an exit plan into a living control you must rehearse, audit, and continuously improve, much like incident response or disaster recovery.
What Are DORA's Specific Requirements for Data Platforms?
DORA requirements translate directly into technical obligations for your data integration stack:
Why Are Exit Strategies So Hard to Implement for Data Platforms?
The same cloud services that accelerate delivery also anchor your data in proprietary formats, APIs, and control planes. When regulators ask you to prove you can "walk away at any time," that hidden dependency becomes obvious (and expensive) to unravel.
Technical Complexity Barriers
Most warehouses and SaaS pipelines rely on provider-specific functions and storage layers. Extracting them intact means rebuilding entire data flows, not simply migrating configurations. The EU's portability mandate sounds simple until you start cataloging every schema dependency, encryption setting, and API call.
Petabyte-scale exports overwhelm bandwidth and backup windows, while time-series data and CDC logs must stay consistent during cutover. Each downstream system, such as CRM feeds, BI dashboards, or ML jobs, requires rewiring before regulators consider the migration "functionally equivalent" to your original stack.
Organizational and Contractual Barriers
Legacy contracts cap export speeds, restrict audit access, or impose termination fees that make exits prohibitively expensive. Even when legal clears the path, you need engineers who understand both platforms, which is a rare combination on most teams.
Real-World Implementation Challenges
Consider a mid-tier bank that tried leaving its SaaS ETL vendor during a regulatory audit. Re-platforming 400 pipelines revealed undocumented transformations buried in the provider's UI. A planned two-week sprint became a three-month crisis while examiners escalated operational resilience findings. The lesson: without proactive portability design, exit plans exist only on paper. And DORA judges you on execution, not documentation.
What Does a Compliant Exit Strategy Look Like in Practice?
The regulation shifts exit planning from a theoretical exercise to a verifiable control inside your ICT-risk framework. Your plan needs four technical pillars that let you leave any provider without breaking daily operations or running afoul of regulators.
Data Portability Foundation
You need to export data and its schemas in open, machine-readable formats. DORA expects "functional equivalence" after transfer, meaning the data should run exactly the same with your fallback platform. Building around open APIs and schema-preserving pipelines lets you satisfy the portability mandate while keeping audit evidence close at hand.
Deployment Flexibility Architecture
Regulators care less about where you run than whether you can move quickly. Architect workloads so they run in public cloud, private cloud, or on-premises with minimal rewiring. Containerized services and infrastructure-as-code make it feasible to spin up a parallel environment inside the transition window required by contractual exit clauses.
Audit Trail and Lineage Management
You must still detect incidents and prove chain-of-custody while moving systems. Store cryptographically signed logs in your own environment and keep lineage metadata coupled with each dataset. If supervisors request evidence, you can show exactly who touched what, when, and where those records live.
No Feature Trade-offs During Migration
An exit strategy that downgrades functionality violates the regulation's continuity objective. Your secondary deployment must offer the same connectors, data transformations, and performance SLAs as production. Testing both environments side-by-side demonstrates operational equivalence and gives auditors confidence that a switch-over will be invisible to end users.
Core Components Implementation
Each row connects: open schemas feed lineage, lineage verifies parity, and contractual rights enforce the whole system.
How Can Data Teams Build and Test Their Exit Strategy?
The regulation makes "exit-on-demand" a hard requirement, so you need a repeatable playbook that regulators can inspect. The workflow below turns the law's broad mandates into concrete tasks you can own and iterate.
1. Risk Assessment and Gap Analysis
Start by cataloging every critical ICT dependency, including source systems, orchestration layers, and proprietary APIs. Cross-check each vendor contract for notice periods, audit rights, and data-return clauses. Supplier scorecards and compliance checklists help expose critical gaps early.
2. Develop, Document, and Maintain Exit Plans
For each critical service, write an actionable exit playbook that names fallback providers, migration runbooks, data-format requirements, and verification steps. Store the evidence pack regulators expect, such as transition timelines, retrieval periods, and functional-equivalence test results so that you can surface it on demand. Your compliance documentation needs to prove readiness, not just promise it.
3. Test Operational Resilience
Move beyond tabletop drills. Schedule scenario-based simulations that mimic a sudden provider insolvency or regulator-forced switch. The regulation's "threat-led testing" language means red-team exercises and full data-plane failovers. Log every action and reconcile migrated datasets to prove functional equivalence.
4. Establish Governance Framework
Assign ownership of legal draft clauses, security validates encryption, data engineering runs migrations, and the board reviews residual risk. Clear accountability structures turn a static document into an auditable control.
5. Implement Third-Party and Data Management Controls
Maintain immutable backups outside the provider's environment, enforce continuous monitoring, and demand periodic exit-readiness attestations from suppliers. These monitoring controls reduce incident-to-recovery times and meet the act's continuous oversight expectations.
Regularly revisit each step, as contract renewals, new integrations, and architectural changes can all invalidate yesterday's "green" status. A quarterly dry-run that migrates a non-production workload end-to-end keeps evidence current and teams sharp.
Exit Plan Maturity Model
Even if you start at "Basic," you should target "Developing" within months and have a clear roadmap to "Advanced."
What Outcomes Can Enterprises Expect from a DORA-Compliant Exit Strategy?
A compliant exit strategy transforms regulatory compliance into operational advantage. When you can demonstrate on-demand that critical data and workloads migrate safely, auditors recognize built-in resilience, partners trust your processes, and your team gains freedom to choose optimal technology for each project.
Compliance and Audit Benefits:
- Faster compliance sign-offs as documented exit plans and contract clauses aligned to transition-period rules turn reviews from weeks of remediation into quick evidence checks
- Data portability requirements force providers to support open formats, giving you negotiating power during renewals or replacements
- Clear controls over data residence satisfy both DORA and overlapping jurisdictional rules, enabling cross-border expansion
Operational and Technical Benefits:
- Open interfaces and reusable migration runbooks eliminate hidden engineering hours typically spent untangling proprietary APIs, reducing total cost of ownership
- Tested playbooks shrink switch-over windows from months to days, maintaining project timelines while limiting outage risk
- Teams gain the ability to respond to direct supervisory oversight requirements without disrupting daily operations
Strategic Business Benefits:
- Teams gain agility to launch products faster
- Achieve better cost control through improved contract terms
- Strengthen risk management under the regulation's enforcement regime
- When exit readiness becomes part of daily operations rather than crisis management, you gain strategic flexibility that vendor-locked competitors can't match
How Does Airbyte Flex Support Exit Strategy Compliance?
Airbyte Flex delivers the operational evidence regulators demand without forcing you to surrender control of your data. Its hybrid deployment with a cloud-managed control plane keeps orchestration in Airbyte Cloud while the data plane runs inside your own VPC under your keys, satisfying the act's sovereignty and audit-right clauses. Because pipelines move through infrastructure you own, you can prove at any time that critical data never leaves approved jurisdictions.
Portability is built into the architecture rather than added as an afterthought. Flex ships the full catalog of 600+ connectors and uses open-standard code generation, so the exact same pipeline you run in one cloud region can be redeployed on-prem or with a different provider. There's no feature split to refactor during an exit.
Is Your Exit Plan Audit-Ready?
Regulators are scrutinizing one critical question: can you exit any ICT provider today without data loss or downtime? Your compliance team needs documentation proving you can transition seamlessly.
A compliant exit plan requires three key components: documented transition periods with realistic timelines, exportable and functionally equivalent data in open formats, and contractual audit and oversight rights with verification mechanisms. Failing to meet these expectations may result in contractual or regulatory consequences, including potential fines or service restrictions. Most data teams discover their supposed "exit strategy" is actually months of re-engineering work exactly what the regulation aims to prevent.
Airbyte Flex solves this with hybrid deployment that keeps your data sovereign while delivering 600+ identical connectors across any deployment. Your audit logs stay in your environment, your data never leaves your control, and you maintain the same functionality whether you're on-premises, hybrid, or cloud.
Map your current dependencies, test a migration scenario, and compile your evidence pack before auditors arrive.
Talk to Sales about building a regulator-ready exit strategy with Airbyte Enterprise Flex.
Frequently Asked Questions
What happens if my data integration provider doesn't comply with DORA exit requirements?
If your provider is deemed "critical" by supervisors, they can be banned from serving EU financial institutions entirely. For your organization, this means potential regulatory fines, failed compliance audits, and emergency migration under regulator pressure. You're responsible for ensuring your providers meet DORA standards, so provider non-compliance becomes your compliance risk.
1. How long do I have to exit a data integration platform under DORA?
Article 28 requires "adequate" transition periods based on data volume and criticality, but doesn't specify exact timeframes. However, regulators expect you to negotiate realistic notice periods in contracts before signing. Most financial institutions are building for 90-180 day transition windows for critical data platforms, depending on complexity.
2. Does DORA apply to all data integration tools or just "critical" ones?
DORA applies to all ICT services used by regulated financial institutions, but enforcement intensity varies. "Critical" providers face direct regulatory oversight and potential service bans. Even non-critical providers must support your exit planning obligations, so you need exit strategies for any platform handling operational data.
3. Can I use multi-cloud deployment to satisfy DORA exit requirements?
If a data integration provider fails to meet DORA exit requirements, your organization bears the compliance risk, potentially facing regulatory fines, failed audits, and emergency migration pressures, especially if the provider is classified as critical by EU financial supervisors.
4. What documentation do regulators expect for data platform exit strategies?
Regulators want operational proof: transition timelines, data export procedures, functional testing results, and evidence that secondary platforms work identically to primary ones. Generic disaster recovery documentation isn't enough. You need migration playbooks that prove you can switch providers without business disruption.
5. How does DORA interact with GDPR for cross-border data platforms?
Both regulations reinforce data sovereignty principles. GDPR restricts where personal data can be processed, while DORA requires exit plans that maintain those restrictions during provider transitions. This typically means your exit strategy must keep EU personal data within approved jurisdictions throughout any migration process.

.webp)
