Cross-Border Data Transfer Compliance: Global Enterprise Guide
Summarize this article with:
✨ AI Generated Summary
Cross-border data transfers must comply with diverse regulations like GDPR, US sectoral laws, Brazil's LGPD, and the Global CBPR, each imposing unique legal and technical requirements. A unified control plane with region-specific data planes enables centralized governance while keeping data local, simplifying compliance by enforcing policies, maintaining audit logs, and preventing unauthorized transfers.
- Key challenges include conflicting laws, cloud replication complexity, vendor risks, and administrative burdens.
- Elastic regional scaling supports compliance by adjusting compute capacity without moving data across borders.
- Effective governance requires centralized data inventories, lineage tracking, immutable audit logs, and policy-as-code enforcement.
- Airbyte’s hybrid architecture separates orchestration from data processing, ensuring data residency, outbound-only communication, and flexible deployment for global compliance.
Every overnight analytics sync, customer support lookup, or AI model upload moves personal data through multiple jurisdictions, each triggering different legal requirements: GDPR in the EU, sectoral rules in the US, Brazil's LGPD, or the emerging Global CBPR framework.
Compliance means proving, at any moment, that data left one country only under a recognized legal mechanism, remained encrypted in transit, and landed in infrastructure with auditable safeguards. Your architecture, not policy binders, determines whether you can meet that standard.
A unified control plane with region-specific data planes centralizes governance while keeping raw data local. This turns today's fragmented regulatory landscape into a solvable design problem rather than an operational fire drill.
What Global Frameworks Govern Cross-Border Data Transfers?
Every international data transfer triggers multiple privacy regimes with conflicting requirements. The EU's GDPR, U.S. sectoral statutes, Brazil's LGPD, and the newly globalized CBPR system each impose distinct prerequisites, and they rarely align.
GDPR and European Economic Area Requirements
GDPR requires that personal data maintain its protections wherever it travels. Adequacy decisions, Standard Contractual Clauses (SCCs), Binding Corporate Rules, and documented Transfer Impact Assessments provide the legal framework for data movement, but only if you can prove "essentially equivalent" safeguards. AI model training also falls under these rules, forcing companies to revisit transfer assessments.
United States Sectoral and National Security Rules
The United States offers no single federal law. Instead, HIPAA, GLBA, and state-level statutes like CPRA govern specific data types. Forthcoming U.S. regulations, proposed in 2024, may restrict some outbound transfers of sensitive personal data to countries of concern, with requirements like encryption, risk reviews, and record-keeping, but these rules have not yet taken effect.
Brazil's LGPD and Regional Variations
Brazil's LGPD mirrors GDPR but adds its own requirements. While ANPD-approved SCCs may become an option for international transfers in the future, as of now there is no mandate requiring their use. Companies operating in Brazil must monitor regulatory updates, review contracts as needed, and appoint DPOs where required to stay compliant.
Asia-Pacific and Global CBPR Systems
Asia-Pacific economies traditionally relied on the voluntary APEC Cross-Border Privacy Rules. In June 2025, those principles scaled worldwide with the Global CBPR and Processor Recognition systems, creating an accreditation route for any country. While certification remains optional, it provides an interoperable baseline amid rising sovereignty-first laws in China and beyond. China PIPL compliance requires region-specific data planes to meet strict localization mandates.
Successful compliance depends on matching your legal mechanism to each jurisdiction's expectations, whether that's binding clauses, regulator-approved certifications, or full in-country processing.
What Are the Biggest Compliance Challenges in Global Data Transfers?
Moving data across borders means navigating conflicting legal requirements, cloud architecture complexity, vendor risks, performance trade-offs, and administrative burdens that can overwhelm even experienced teams.
- Conflicting Legal Requirements Across Jurisdictions: GDPR, Brazil's LGPD, and emerging U.S. national-security rules each impose different legal bases, assessments, and contractual terms. A pipeline that looks lawful in one region can violate another overnight.
- Cloud Architecture and Data Replication Complexity: Multi-cloud providers replicate data for resilience, yet rarely tell you exactly where each copy lands. Shadow copies can quickly undermine compliance efforts when regulations demand that personal data stay inside specific jurisdictions.
- Third-Party Vendor Risk and Limited Visibility: Third-party APIs create blind spots as downstream processors spawn their own transfers. Once data leaves your environment, you rely on contractual guarantees and limited audit rights.
- Performance vs. Compliance Trade-Offs: Keeping data in the right place adds latency that frustrates users and slows analytics. Data localization mandates can force you to duplicate pipelines, inflating infrastructure costs.
- Administrative Burden of Compliance Documentation: Many jurisdictions require paperwork like updated SCCs, DPO appointments, or Transfer Impact Assessments, but these requirements vary widely by region and legal framework.
These pressures demonstrate that manual policy checks won't scale. You need architecture-level controls with centralized orchestration and region-bound data planes to turn compliance from reactive firefighting into proactive design.
How Can Unified Architectures Simplify Cross-Border Compliance?
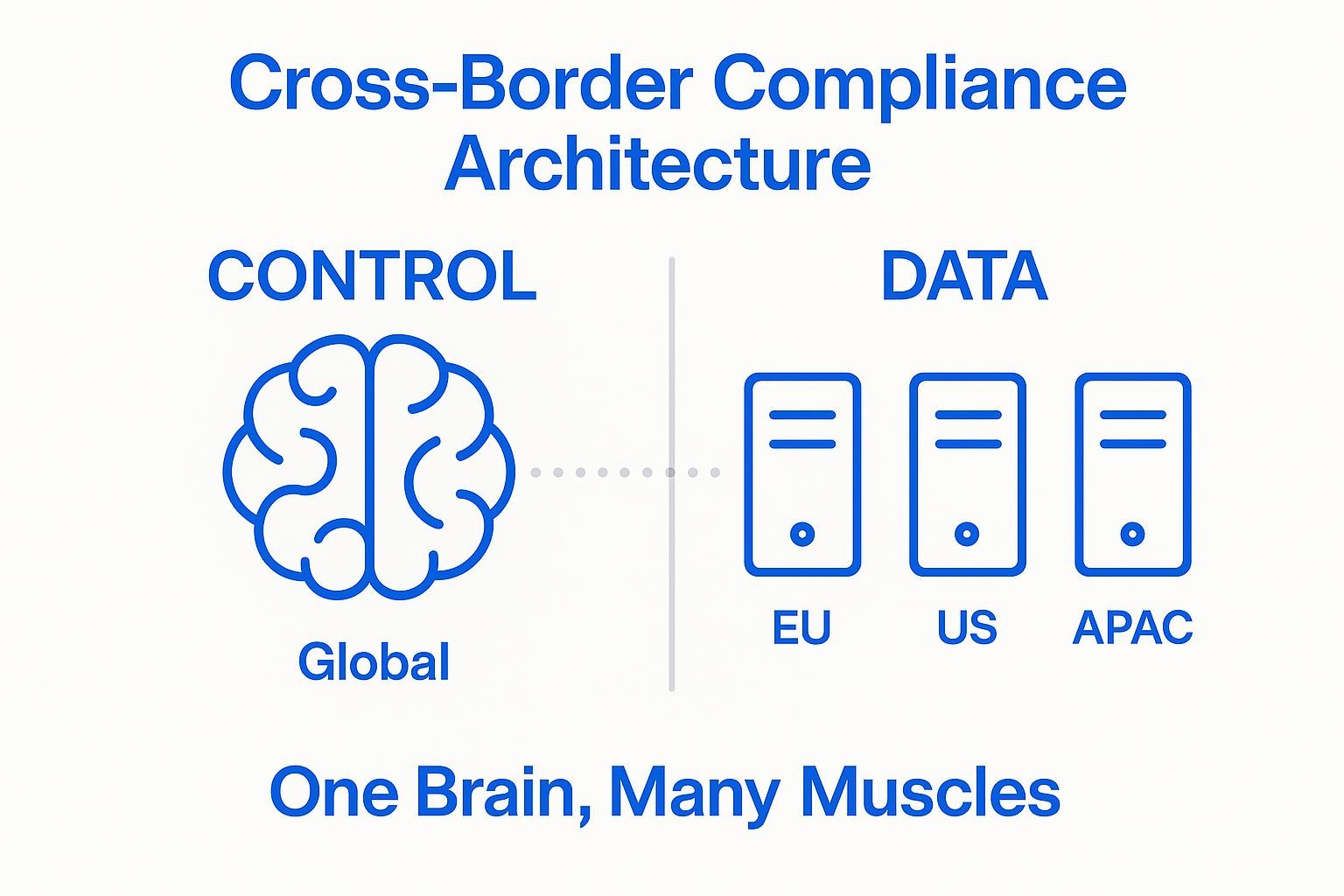
The solution starts with separating the "brain" from the "muscle." A unified control plane manages configuration, authentication, and policy globally, while regional data planes handle the actual data processing inside the jurisdictions that require them. Because the control layer never touches raw records, you get a smaller attack surface and a clean audit story without losing central visibility.
With this split, you define governance rules once and let each data plane enforce them locally. A GDPR data set stays inside EU availability zones, Brazilian customer data remains under LGPD jurisdiction, and U.S. workloads run under national-security limits, all from the same console. No traffic crosses a border unless policy allows it, and every decision gets logged for regulators.
Different deployment models let you choose the risk posture that fits each workload. Some teams run a public control plane with cloud-hosted data planes in specific regions. Highly regulated industries keep the data plane inside a private VPC, while sovereignty-first organizations go further with a full bring-your-own-cloud setup.
How Can Elastic Resource Management Support Compliance and Scalability?
Elastic resource management adds or removes compute capacity within each regional data plane on demand, meeting residency requirements while responding instantly to traffic spikes without moving data across borders.
- Regional Scaling Without Cross-Border Data Movement - Scaling logic stays in the global control plane while execution remains in the local data plane. You never move data just to gain processing power, ensuring policy stays centralized while data never leaves the approved zone.
- Automated Capacity Management Within Jurisdictions - Kubernetes horizontal pod autoscalers or cloud auto-scaling groups spin up extra nodes within the same configured region, then tear them down once demand subsides. Because only compute capacity changes within the same region, you generally avoid renegotiating SCCs or rerunning Transfer Impact Assessments every time you scale.
- Operational Benefits of Region-Aware Autoscaling - Local scaling keeps latency low while respecting sovereignty mandates. Cost efficiency comes from paying for burst capacity only when needed. Autoscaling and smart workload routing remove the human error that often causes accidental transfers, and fault isolation means a capacity issue in one region never affects another.
Airbyte Enterprise Flex applies these mechanics directly. You manage 600+ connectors from a hybrid control plane while regional data planes expand elastically (EU-only today, APAC tomorrow) without opening inbound ports or exposing raw records.
How Should Enterprises Govern and Audit Cross-Border Data Transfers?
You can't prove compliance if you can't trace every byte that crosses a border. Effective governance requires centralized visibility, complete lineage tracking, immutable evidence, and automated policy enforcement.
Build a Centralized Data Inventory and Classification System
Effective governance starts with a single source of truth about where sensitive records live, how they move, and who can touch them. The most mature teams anchor that visibility in the control plane while keeping data pinned to regional data planes for sovereignty.
Maintain a data catalog that tags each dataset with sensitivity and jurisdiction. Continuous discovery tools can help surface new tables automatically, supporting the goal of maintaining up-to-date records for GDPR record-of-processing obligations.
Capture Complete Lineage and Flow Mapping
Capture hop-by-hop lineage so you can answer "where did this field originate and where did it land?" without digging through code. When regulators ask questions, you'll have answers, not excuses.
Implement Immutable Audit Logs for Regulatory Evidence
Hash-chained logs stored in write-once buckets create tamper-evident records. These logs become your proof that transfers happened exactly as documented.
Enforce Policy as Code with Real-Time Monitoring
Declarative rules in the control plane block transfers that violate regional rules before they execute. Because policies live in code, you can unit-test them and roll out changes globally in minutes. Event-level monitoring exposes anomalies (say, a spike in exports to a non-adequate country) triggering real-time alerts instead of quarterly surprises.
Consider a multinational bank that processes card transactions in Frankfurt, Tokyo, and São Paulo. Region-aware data planes keep raw PCI data local; redacted aggregates flow to a U.S. analytics lake only after automated lineage checks pass and logs are sealed. During its last audit, the bank produced five years of transfer records in under an hour.
How Does Airbyte Enable Cross-Border Data Transfer Compliance?

You keep control of your data because Airbyte's hybrid architecture follows the control-plane vs. data-plane model. Orchestration lives in Airbyte Cloud's control plane, which stores only configuration and metadata (except for cursor/primary key values and, during development with Connector Builder, some data). Every other record stays inside regional data planes that you deploy in your own VPCs or on-premises servers.
Communication flows outbound-only: each data plane initiates an encrypted session to the control plane, so there's no inbound path for attackers or regulators to flag as a vulnerability. The control layer manages authentication, policy, and scheduling centrally, so you define a rule once and see it enforced in EU, APAC, or the US without moving data across borders. Airbyte’s hybrid control plane acts as regulatory compliance software, enforcing transfer policies across multiple jurisdictions.
Deployment stays flexible. You can run public cloud data planes for standard workloads, spin up private clusters for HIPAA or LGPD datasets, or mix both as demand changes. Key capabilities include:
- Hybrid control plane architecture that separates orchestration from data processing
- Outbound-only communication model eliminating inbound network exposure
- Region-locked data planes ensuring data never crosses jurisdictional boundaries
- Unified management interface for 600+ connectors across all deployment models
- Flexible deployment options supporting public cloud, private VPC, or full on-premises
Airbyte enables global retailers to sync EU sales data to analytics warehouses through an EU-only plane, Japanese inventory streams through a Tokyo plane, and US marketing events flow stateside, all managed from one UI.
Where Should Enterprises Start Their Compliance Modernization Journey?
You'll move faster once you frame compliance as an engineering problem, not a policy checklist. Start by narrowing the blast radius of every transfer, then automate the safeguards that keep you audit-ready.
The following roadmap provides a structured approach to compliance modernization:
- Map Cross-Border Data Flows - Chart every dataset, system, and vendor hop. A clear data flow map exposes hidden transfers that regulators will ask about first.
- Classify Regulated Data - Tag personal, health, payment, and other sensitive records so you always know which laws apply before data leaves a region.
- Deploy Regional Data Planes - Keep processing close to the source. Isolated, in-region data planes let you honor residency rules without fragmenting orchestration.
- Automate Policy Enforcement - Use metadata-driven rules to block non-compliant routes, trigger encryption, or require Transfer Impact Assessments. Automation catches edge cases manual reviews miss.
- Establish Immutable Audit Logs - Centralized, tamper-proof logs prove exactly who accessed what, when, and why. Core evidence for audits and breach investigations.
Compliance doesn't have to slow modernization when architecture is your foundation. Airbyte Flex delivers HIPAA-compliant hybrid architecture, keeping ePHI in your VPC while enabling AI-ready clinical data pipelines across multiple jurisdictions. Talk to Sales to discuss your cross-border compliance requirements and see how hybrid data planes can meet GDPR, LGPD, and emerging regulations without compromising on capability.
Frequently Asked Questions
What is the difference between GDPR adequacy decisions and Standard Contractual Clauses?
Adequacy decisions are formal EU determinations that a third country provides equivalent data protection, allowing transfers without additional safeguards. SCCs are contractual commitments between exporters and importers that provide appropriate safeguards when no adequacy decision exists, requiring Transfer Impact Assessments and supplementary measures if needed.
How do regional data planes help with data localization requirements?
Regional data planes process data within specific geographic boundaries while the control plane orchestrates operations globally. This lets you meet strict localization mandates in countries like China, Russia, or Brazil while maintaining centralized governance and visibility without rebuilding integration logic for each geography.
What types of data transfers require Transfer Impact Assessments under GDPR?
TIAs are required for transfers relying on SCCs or Binding Corporate Rules to countries without adequacy decisions. You must assess whether the destination country's laws might impinge on your safeguards, particularly for countries with broad government surveillance powers or inadequate legal protections.
Can elastic scaling within regional data planes trigger compliance violations?
Properly configured regional data planes scale compute resources within the same approved jurisdiction without moving data. However, you must ensure your cloud provider's auto-scaling configuration is region-locked and cannot failover to other geographies. Misconfigured multi-region replication or backup policies cause most accidental cross-border transfers during scaling events.

.webp)
.png)