European Data Sovereignty Solutions: GDPR-Compliant Architecture
Summarize this article with:
✨ AI Generated Summary
Meta faced a €1.2 billion GDPR fine due to cross-border data violations, highlighting the critical need for true data sovereignty beyond just EU storage locations. GDPR requires that all data processing, access, and auditing occur exclusively under EU law, demanding immutable audit logs, fine-grained access control, sovereign encryption, and verifiable data lineage.
- Traditional multi-region ETL pipelines often violate GDPR by transferring data outside the EU without proper safeguards.
- Hybrid control plane architectures separate orchestration (cloud) from execution (EU data plane), ensuring data never leaves EU jurisdiction while enabling scalability.
- Industry-specific regulations necessitate tailored sovereignty solutions, with enterprises advised to map regulations, secure control/data planes, validate via proof of concept, and document compliance rigorously.
- Sovereignty-first designs prevent compliance gaps, enable audit-ready environments, and future-proof operations against evolving EU regulations like DORA and the AI Act.
Your ETL pipeline just became a €1.2 billion liability. That's what Meta learned when European regulators hit them with GDPR's largest fine for cross-border data violations.
An even bigger problem is that regulators now shut down data flows overnight when they decide your transfer mechanisms don't meet sovereignty requirements, as companies discovered after Schrems II.
GDPR's reach extends to any processing of EU personal data, regardless of where your company is headquartered. This means your multi-region cloud architecture, your SaaS ETL platform, and your "EU-hosted" marketing claims don't automatically protect you.
Every pipeline choice like where storage lives, how data moves between regions, and who can access processing logs, either reduces your compliance risk or amplifies it.
What Does European Data Sovereignty Actually Mean?
Data sovereignty is about control, not geography. You still care where data is stored, but sovereignty goes further, demanding that every byte is processed, accessed, and audited exclusively under European law.
Computing, Storage, and Handling Are Traceable
Hosting customer records in an "EU region" counts for little if a non-EU parent company can legally compel the cloud operator to hand them over. True sovereignty means regulators, customers, and your own security team can trace exactly where compute happened, who touched the data, and under which jurisdiction each action occurred.
GDPR hard-codes this principle. Article 3's territorial scope places any organization handling EU residents' personal data under EU rules, even when the company sits on another continent (a reach clarified in Schrems II and subsequent guidance on cross-border transfers).
Rights and Access Remain With the Data Subject
Sovereignty also lives in day-to-day operations. GDPR grants data subjects powerful rights that your architecture must honor. People can see and correct their data through access and rectification requests. You must delete every copy on request through erasure rights.
Your pipelines therefore, need granular search, deletion, and export functions, all while recording an immutable audit trail to satisfy GDPR's accountability principle.
Why Do Traditional Architectures Fail Sovereignty Tests?
When your data pipelines sprawl across "global" regions, every extract-transform-load job creates a compliance minefield. Multi-region SaaS ETL platforms copy data to whichever data center is cheapest or least loaded (you rarely know where each byte lands, let alone control it).
The moment personal data leaves the EU, GDPR Article 44 demands an adequacy decision or contractual safeguards. Without explicit authorization, those background transfers violate the regulation outright.
Hosting inside an EU-based cloud region doesn't solve the problem. If the infrastructure is owned by a non-EU company, foreign laws like the U.S. CLOUD Act can compel disclosure, undermining true sovereignty despite the European address on the invoice.
Legacy ETL tools make things worse with opacity. Opaque job runners, ad-hoc scripts, and scattered log stores make it nearly impossible to reconstruct a complete audit trail. When a data subject files a request or a breach forces disclosure, you must prove where information flowed and who touched it.
How Can Hybrid Control Plane Architectures Solve the Trade-Off?
You need a way to modernize pipelines without letting personal data drift outside EU jurisdiction. A hybrid control plane does exactly that by separating orchestration from execution.
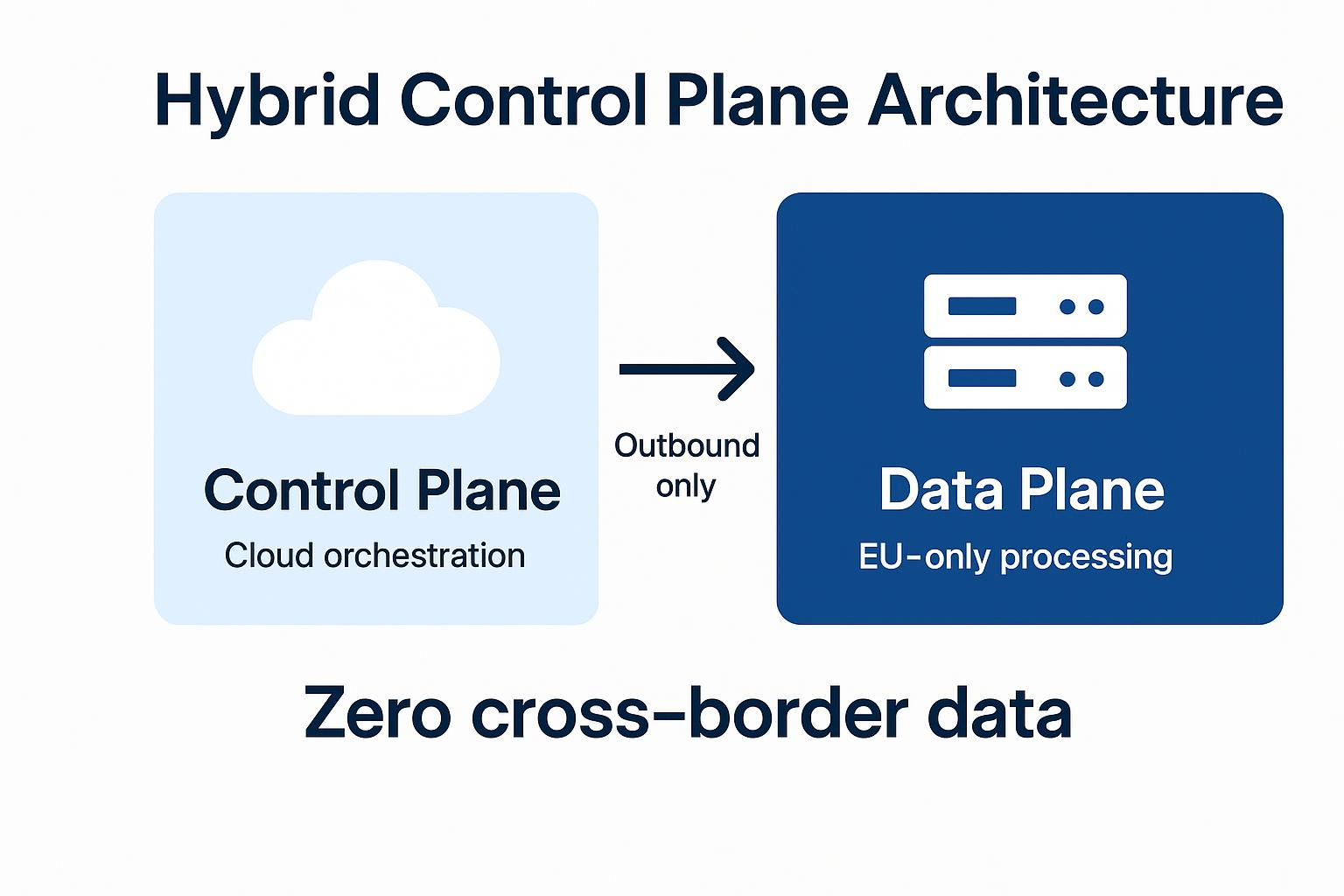
The control plane (the "brain" that schedules and enforces policy) runs in a managed cloud environment, while the data plane (the "muscle" that actually moves and transforms data) stays inside your VPC or on-prem cluster.
Establishing Clear Jurisdictional Boundaries
The managed control plane handles API endpoints, workload scheduling, policy enforcement, and cluster management. When you trigger a sync, the control plane sends instructions outbound-only to your data plane, which executes jobs on EU hardware you control.
Maintaining Data Locality
No inbound ports open and all processing happens locally, so personal data never leaves the region (meeting GDPR's territorial requirements).
Enabling Scalable Operations
The cloud service handles upgrades and node health, delivering hybrid cloud benefits without the complexity. You keep full source and destination coverage instead of the handful typically offered by "split-stack" on-prem options.
This approach delivers several key advantages:
- Data never crosses borders: All reads, writes, and logs stay inside infrastructure governed by EU law
- Scalable without Kubernetes overhead: The cloud service handles upgrades and node health
- Full connector coverage: You keep complete source and destination coverage instead of the handful typically offered by "split-stack" on-prem options
- Consistent UI and API: Manage cloud, hybrid, and on-prem deployments from the same interface
What Technical Capabilities Should a GDPR-Compliant Stack Include?
You need four core capabilities: immutable audit logging, fine-grained access control, sovereign encryption, and verifiable data lineage.
1. Immutable Audit Logging
Start with immutable audit logging stored inside your EU environment. You have 72 hours to report a breach, and tamper-proof logs are a critical part of your evidence trail. Capture every read, write, and transfer event, then checksum each entry so no one can alter it later.
2. Least-Privilege Access
Enforce least-privilege access through fine-grained RBAC tied to your enterprise identity provider. Each role maps to specific datasets and operations (no "all-access" admin accounts that regulators flag as high risk).
3. Sovereign Encryption
Pair this with encryption that never leaves EU jurisdiction. Encrypt data in transit and at rest, but keep the keys inside your customer-controlled store. Cloud-hosted HSMs managed by non-EU providers create sovereignty gaps that sovereign-cloud deployments specifically avoid.
4. Verifiable Data Lineage
Regional isolation and verifiable data lineage complete your compliance foundation. Separate workspaces per EU member state prevent accidental replication to unauthorized regions. Cryptographically signed lineage graphs show auditors every hop your data has taken.
How Do Sovereignty Needs Differ by Industry?
How Can Enterprises Implement Sovereignty-First Architectures?
Sovereignty-first design succeeds only when you tackle governance before writing a single line of Terraform.
Map Regulatory Requirements
Start by mapping every regulation that touches your data. Article 3's extra-territorial reach means even non-EU systems processing EU personal data must comply, so create a living inventory that shows what you collect, where it travels, and which law applies to each element.
Choose Your Deployment Model
With your inventory complete, choose a deployment model. Pure on-premises offers maximal control, but most teams start hybrid: a cloud control plane orchestrates jobs while all personal data stays in EU-hosted or on-premises data planes.
Secure Control and Data Planes
Secure both control and data planes next. Outbound-only networking, region pinning, and customer-managed encryption keys significantly reduce the risk of inadvertent cross-border data flow.
Validate Through Proof of Concept
Run a proof of concept before enterprise rollout. Replicate a high-volume Change Data Capture stream inside an EU region, then validate latency, lineage, and access logs against your Data Protection Impact Assessment checklist.
Document Everything
Document everything, including network diagrams, key management procedures, and SAR response playbooks. When an auditor asks where the computation occurred at 14:07 UTC, you'll answer with screenshots instead of guesswork.
What Outcomes Do Sovereignty-First Enterprises Achieve?
Personal data never leaves EU jurisdiction, so auditors can trace every byte in minutes (satisfying the EU's accountability principle). The same hybrid control plane that enforces locality keeps workloads elastic; when traffic surges, new workers spin up inside your VPC rather than spilling into non-compliant regions.
Teams retire six-figure Informatica licenses and redirect that budget to growth projects. Your stack stays ahead of fast-approaching rules like DORA and the AI Act.
Sovereignty-first architectures create audit-ready environments while delivering the operational reliability and cost efficiency your data teams need.
Build Sovereignty Into Your Architecture From Day One
Bolt sovereignty on later, and every forgotten backup, log, or temp file becomes a compliance landmine. You scramble across regions hoping nothing slipped outside EU protection.
Design it in from day one: keep orchestration in a cloud control plane, run the data plane inside your own EU VPC, and preserve keys and immutable logs. Purpose-built architectures eliminate compliance gaps before they emerge.
Airbyte Flex delivers GDPR-compliant, sovereignty-first architectures with 600+ connectors across on-premises and hybrid deployments.
Try Airbyte Flex to validate CDC performance inside your EU-controlled data planes. Or talk to sales to discuss your compliance requirements.
Frequently Asked Questions
What is the biggest misconception about GDPR data sovereignty?
Many organizations assume that storing data in an EU cloud region automatically ensures compliance. In reality, sovereignty requires that processing, access, and auditability are also fully governed by EU law. If a non-EU parent company controls the infrastructure, regulators may still consider the setup non-compliant.
How does Schrems II affect cross-border data transfers?
The Schrems II ruling invalidated the EU–US Privacy Shield, making it clear that standard contractual clauses alone may not be enough when foreign surveillance laws conflict with EU protections. Enterprises must now evaluate each transfer case by case and adopt sovereignty-first architectures to avoid sudden disruptions.
What technical safeguards do regulators expect?
Regulators expect immutable audit logs, fine-grained access control, encryption with EU-held keys, and verifiable data lineage. These safeguards prove that personal data stayed within EU jurisdiction and that all processing actions were properly authorized and documented.
Can hybrid cloud still be GDPR-compliant?
Yes—if implemented correctly. A hybrid control plane allows orchestration in the cloud while keeping all personal data processing inside EU-controlled data planes. This model enables scalability and operational efficiency without violating data sovereignty requirements.

.webp)
