GDPR Data Sovereignty: European Enterprise Compliance Guide
Summarize this article with:
✨ AI Generated Summary
GDPR data sovereignty requires that EU personal data remains under EU legal jurisdiction throughout its lifecycle, not just physically stored in the EU, to avoid hefty fines and compliance risks. Traditional data stacks and cloud SaaS tools often fail this by allowing unauthorized cross-border transfers and lacking auditability, while sovereignty-first architectures enforce geo-fenced storage, immutable audit logs, and customer-controlled encryption keys.
Key compliance essentials include:
- Mapping data flows and processors with immutable lineage
- Implementing hybrid control and customer-controlled data planes to keep data inside EU VPCs
- Enforcing strict governance with role-based access, masking, and external secrets management
- Continuous monitoring, real-time alerts, and automated breach response
Solutions like Airbyte Flex enable GDPR-compliant pipelines by separating control from data planes, preventing data from leaving EU jurisdiction while supporting scalable, auditable, and vendor-lock-in-free data integration. Embedding sovereignty as a design principle accelerates innovation and reduces regulatory risk.
You've probably seen the headlines: regulators have already levied hundreds of millions of penalty against Amazon, and organizations risk fines of up to €20 million or 4% of global turnover (whichever is higher) for serious violations of data protection regulations, including improper cross-border data transfers. Those numbers translate into board-level panic, sudden processing bans, and stalled product launches the moment an audit exposes a sovereignty gap.
Data sovereignty became the foundation that keeps your analytics stack running when every table, log, and microservice touches EU personal data. Without it, you risk overnight downtime while engineers scramble to reroute pipelines, executives field reputational fallout, and legal teams negotiate with supervisory authorities demanding immediate remediation.
What Does GDPR Data Sovereignty Really Mean for Enterprises?
GDPR data sovereignty means EU citizen data stays under EU legal protection regardless of where you, your processors, or cloud infrastructure operate. The regulation's extraterritorial reach covers any organization worldwide handling EU data, so you can't escape compliance by incorporating elsewhere or moving storage offshore.
Data residency gets confused with sovereignty constantly. Residency is about physical location; sovereignty is about jurisdiction. Park your data in a European availability zone all you want, but if the provider answers to non-EU governments, that data can still face foreign legal demands, breaking the EU protections you promised customers.
This trips up teams regularly. A workload in an EU cloud region owned by a U.S. company can be compelled to disclose data under the CLOUD Act, creating unauthorized cross-border transfers. Every transfer leaving EU legal protection needs lawful mechanisms: adequacy decisions, Standard Contractual Clauses, or explicit consent.
Why Current Enterprise Approaches Break Under GDPR Pressure
Most enterprise data stacks were designed for speed, not jurisdictional control. As a result, they silently move personal data across regions, leaving you with blind spots the moment an auditor asks, "Where exactly did this record travel?"
Legacy ETL platforms were built around centralized clusters that replicate data to boost performance. Those clusters rarely respect geographic fences, so an innocuous transformation job can route EU citizen data through a U.S. staging server and trigger Article 44 violations. Cloud-only SaaS tools make this worse, as their multitenant fabrics mingle your PII with other customers' workloads on infrastructure that the provider (and often the U.S. CLOUD Act) can access.
Vendor lock-in creates another critical gap. When regulators demand end-to-end lineage, proprietary pipelines make it impossible to export immutable logs or reconstruct historical data flows. This gap gets flagged repeatedly in enterprise architecture compliance reviews.
The impact is tangible. Meta's €1.2 billion penalty for unlawful U.S. transfers shows how quickly fines eclipse technology budgets. Until pipelines are rebuilt around explicit EU control planes and customer-owned data planes, enterprises will keep absorbing compliance shocks instead of shipping features.
What Are the Core GDPR Compliance Requirements Around Data Sovereignty?

You need to demonstrate not just that personal data lives inside the EU, but that every byte remains under EU legal control throughout its lifecycle. The GDPR spells this out across several articles that auditors reach for first when they sit down with your architecture diagrams.
Data Protection Principles (Article 5)
- Data minimization: Collect only what you truly need for the specified purpose
- Storage limitation: Delete data when the processing purpose is fulfilled
- Purpose limitation: Use data only for the original stated purpose
- Accuracy: Keep personal data accurate and up-to-date
Processor Accountability (Article 28)
- Written contracts: Ensure data protection obligations for all processors and sub-processors
- Processing instructions: Processors must act only on your documented instructions
- Security measures: Implement appropriate technical and organizational safeguards
- Sub-processor management: Maintain oversight of all downstream data handlers
Records of Processing (Article 30)
- Processing activities: Document purposes, data categories, recipients, and retention periods
- Data flows: Map how personal data moves through your systems
- Legal basis: Record the lawful basis for each processing activity
- International transfers: Document any cross-border data movements and their legal mechanisms
Security Requirements (Article 32)
- Risk-based approach: Implement security measures appropriate to the risk level
- Encryption: Use encryption for data at rest and in transit where appropriate
- Access controls: Implement role-based access to personal data
- Regular testing: Test, assess, and evaluate security measures regularly
Cross-Border Transfer Rules (Articles 44-50)
- Adequacy decisions: Transfers to countries with EU adequacy decisions are permitted
- Standard Contractual Clauses (SCCs): Use approved contractual safeguards for other transfers
- Binding Corporate Rules: Implement approved internal data transfer mechanisms
- Essential guarantees: Ensure foreign surveillance laws don't undermine data protection
Regulators increasingly focus on your ability to prove these safeguards. They want immutable audit trails that show when a dataset moved, who accessed it, and which legal basis justified the action. During recent EU investigations, maintaining detailed and rapidly accessible audit logs is increasingly recognized as a best practice for meeting evolving regulatory expectations.
Equally important is processor accountability. Even if you choose an EU data center, a U.S.-headquartered vendor may still be subject to foreign disclosure laws. Under Article 28, you must ensure contracts require the vendor to act on your instructions and implement appropriate safeguards.
How Can Enterprises Architect GDPR-Compliant, Sovereignty-First Data Pipelines?
You can't add sovereignty to an existing stack. To keep EU personal data permanently under EU jurisdiction while still delivering near-real-time analytics, you need an architecture that treats location and control as first-class design parameters.
Map Data Flows and Risks
Building compliant pipelines begins with drawing a complete map of every place personal data appears. Fragmented pipelines and undocumented hops are the main reason auditors uncover violations.
Discover and classify datasets containing PII, health, or financial records. Tools that automate classification reduce manual blind spots created by siloed systems. Document each processor, sub-processor, and geographic region the data touches. Missing links here derail later Data Protection Impact Assessments.
Record transformation logic and retention schedules to build an immutable lineage. Without this, proving compliance during a breach investigation becomes extremely difficult.
Adopt Hybrid Control + Customer-Controlled Data Planes
A sovereignty-first pipeline splits orchestration from storage and compute. The control plane runs in a managed cloud, but every byte of personal data stays inside your VPC or on-prem cluster that you alone administer. This design substantially mitigates foreign-jurisdiction access risks.
Technical considerations include using private endpoints and outbound-only agents so the control plane never initiates inbound connections. Pin storage tiers to EU availability zones and disable automatic cross-region replication. Keep encryption keys in an EU-based HSM you control; the vendor should only see wrapped keys.
Enforce Enterprise-Grade Governance
Once data is fenced in, you need granular controls to prevent internal misuse. Role-based access control should tie permissions to business purpose, not job title. External secrets managers ensure plaintext credentials never enter pipeline configs.
Field-level masking and tokenization protect sensitive columns, guarding against accidental exposure when schemas change. Immutable audit logs appended to every sync should be stored in a write-once object store inside the same EU region.
Isolated workspaces per business unit or region ensure data from German subsidiaries never mingles with French HR records. This separation becomes critical during audits when regulators need to verify data boundaries.
Verify and Demonstrate Compliance Continuously
Regulatory enforcement doesn't wait for quarterly reviews; you need live assurance. Stream logs to a SIEM that raises alerts on anomalous transfers or permission changes. Build dashboards that show data residency, processor list, and last-verified DPIA status at a glance.
Test failover paths regularly. Backup clusters must also be EU-pinned, or a disaster recovery drill could trigger an illegal transfer. Automate breach-response playbooks so you can meet the regulation's 72-hour notification window without scrambling for proof.
Which Enterprise Teams Are Most Impacted by GDPR Data Sovereignty?
Security teams face the highest stakes. As a CISO or IT security director, any slip in jurisdictional control can trigger fines of up to €20 million or 4% of global turnover, and those penalties apply even to non-EU companies thanks to the regulation's extraterritorial scope. That risk makes immutable, queryable audit logs non-negotiable. Without them you can't prove where every record lives or who accessed it.
Infrastructure modernization leaders face a different challenge. You want to retire expensive legacy ETL but worry new SaaS services will spray PII across regions you can't map. In practice, cloud adoption often scatters data across jurisdictions, so your team blocks migrations until you can guarantee EU-only processing or verified legal transfer mechanisms.
Data engineers handle the operational fallout. Long nights debugging webhook failures, schema drift, and patchwork scripts work that does nothing to advance analytics but keeps pipelines compliant. Maintaining brittle pipelines consumes the bulk of engineering time. You'd rather ship features than replay failed syncs, so a consistent SDK and hybrid control plane that keeps data in your VPC become essential tools, not nice-to-haves.
What Are the Benefits of Sovereignty-First Data Architectures?
How Does Airbyte Flex Support GDPR Data Sovereignty?
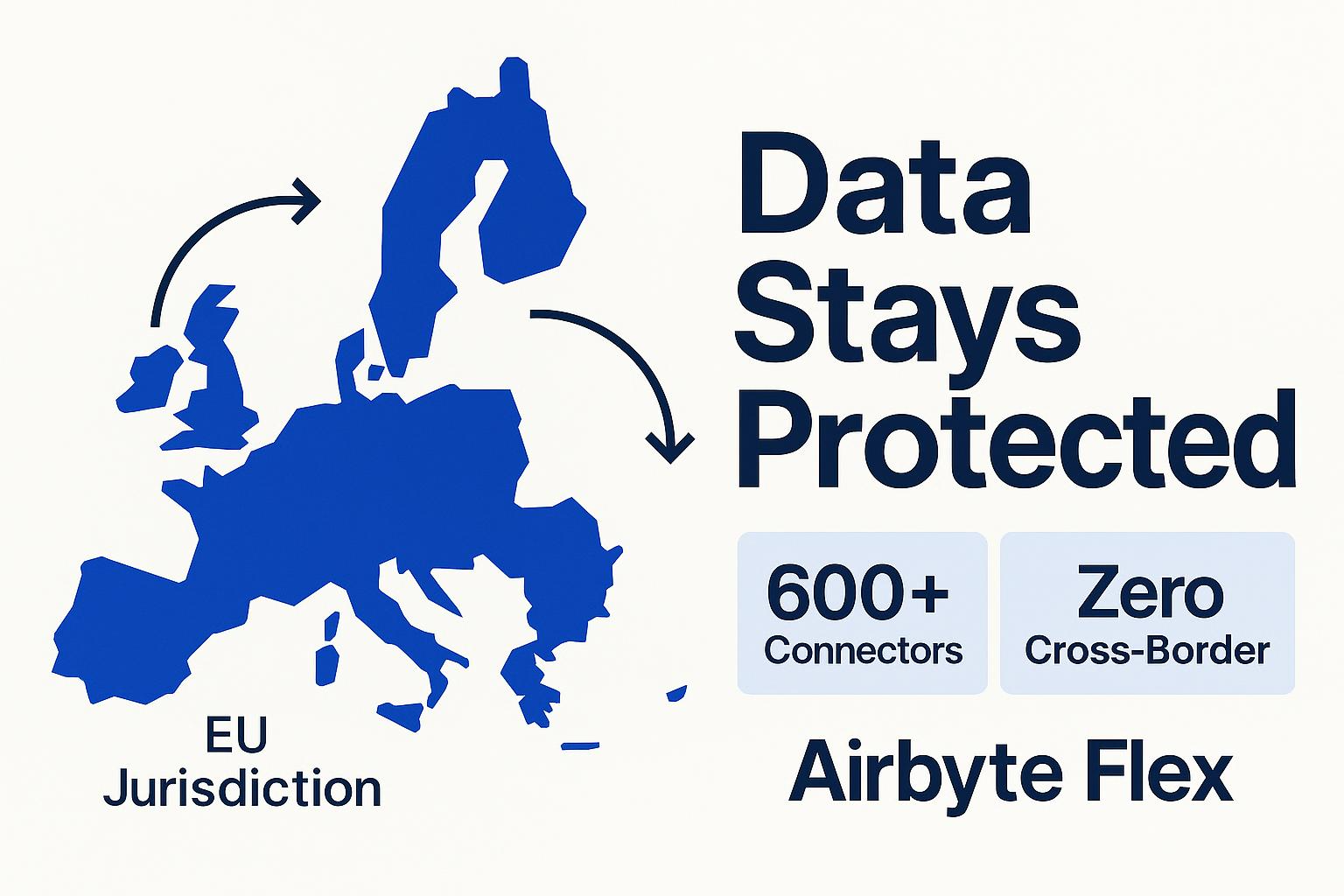
Keeping EU personal data under EU jurisdiction is non-negotiable. The moment a record crosses borders, you inherit the legal headaches described in regulatory guidance. Airbyte Flex eliminates this risk by splitting control from processing: a lightweight cloud control plane orchestrates jobs while every byte of customer data moves inside a data plane you host in your own VPC or on-premises environment. No inbound connections, no hidden copies, no surprise sub-processors.
The same 600+ connectors run identically across cloud, hybrid, or fully air-gapped deployments, preventing the vendor lock-in many compliance teams fear. Enterprise governance features,, such as fine-grained RBAC, field-level PII masking, external secrets management, and immutable audit logs, map directly to regulatory accountability and security expectations.
Because Flex relies on open-standard code generation, you can port pipelines across regions or clouds without rewriting ETL logic when regulations evolve.
Can GDPR Data Sovereignty Drive Enterprise Innovation?
Treating data sovereignty as a design principle, not an afterthought, lets enterprises build compliance and performance advantages simultaneously. When EU citizen data stays under proper jurisdiction, your teams can run analytics without transfer-impact reviews and deploy region-specific AI models with confidence.
This creates a competitive advantage: faster delivery cycles with lower regulatory risk. Companies that embed sovereignty into their architecture from day one avoid the compliance tax that slows their competitors.
Explore how Airbyte Flex builds sovereignty-first pipelines that scale with your compliance requirements.
Frequently Asked Questions
1. What's the difference between data residency and data sovereignty?
Data residency defines where data is physically stored, while data sovereignty ensures that the data remains under the legal jurisdiction and control of a specific country or region, regardless of where the storage infrastructure is located.
2. Do I need Standard Contractual Clauses if my data never leaves the EU?
If your data truly never leaves EU jurisdiction and you only work with processors subject to GDPR, you may not need SCCs. However, most organizations use hybrid architectures or work with global vendors, making SCCs essential as a legal safeguard for any potential cross-border scenarios.
3. How can I prove data sovereignty during a GDPR audit?
Auditors will want immutable logs showing exactly where data traveled, who accessed it, and under what legal basis. You need comprehensive audit trails that track every data movement, transformation, and access event with timestamps and geographic locations.
4. Can I use U.S. cloud providers and still maintain GDPR compliance?
Yes, but only with proper safeguards. You can use U.S. providers if you implement Standard Contractual Clauses, ensure data stays in EU regions, and have contractual guarantees about government access. However, this creates more legal complexity than using EU-based providers.
5. What happens if my backup or disaster recovery system accidentally moves EU data outside the region?
This would likely constitute a GDPR violation and must be reported to supervisory authorities within 72 hours. It's why disaster recovery testing must include jurisdiction verification. Design your backup systems to respect the same geographic constraints as your primary systems.
6. How does Airbyte Flex help with GDPR data sovereignty?
Airbyte Flex separates the control plane (managed in the cloud) from the data plane (runs in your infrastructure). Your EU personal data never leaves your VPC or on-premises environment, while you still get the benefits of a managed service for orchestration and monitoring.

.webp)
