Operational Resilience: Business Continuity During CSP Outages
Summarize this article with:
✨ AI Generated Summary
Operational resilience in cloud-dependent businesses hinges on four pillars: redundancy, failover orchestration, data replication, and governance continuity, which together mitigate outages and maintain compliance. Hybrid architectures with unified orchestration enhance business continuity by enabling autonomous failover, workload portability, and data sovereignty across multiple clouds and on-premises environments. Regular testing, automated replication, and continuous governance are essential to ensure rapid recovery, compliance with regulations like DORA, and uninterrupted operations during cloud provider failures.
Whether you run fintech analytics or power an e-commerce storefront, most of your stack lives on AWS, Azure, or Google Cloud. When those platforms falter, so does your revenue. Downtime drains budgets at thousands to millions of dollars per hour and destroys customer trust instantly.
This dependency creates a critical vulnerability. Architectures that absorb cloud disruptions through redundancy, failover, and continuous governance protect mission-critical operations and the reputation that depends on them.
What Are the Key Elements of Operational Resilience?
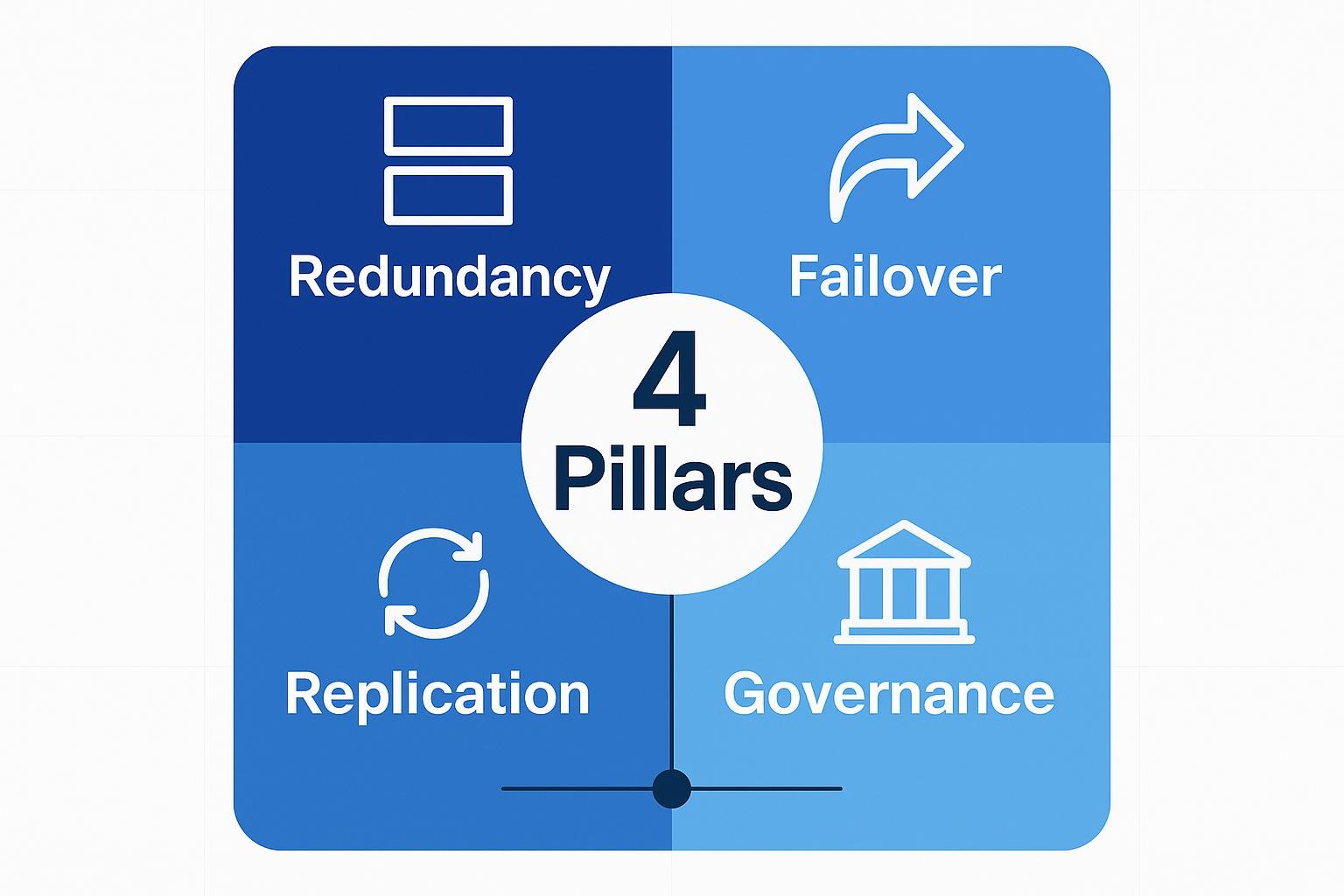
Robust operational resilience rests on four pillars that keep your core systems running when cloud providers fail. Together they turn outages into manageable engineering events rather than business disasters.
Redundancy gives you a safety net by deploying duplicate workloads across regions or different vendors. This approach avoids single-point failures like power disruptions that routinely knock out entire data-center halls.
Failover orchestration makes that safety net automatic through a control plane that monitors health and reroutes traffic. This prevents the multi-hour standstills that occur when mis-configured network changes freeze routes.
Data replication ensures every location stays current through continuous sync, protecting you from corruption or loss if a storage shelf fails mid-transaction. Modern redundancy and replication mechanisms mitigate this scenario, though they don't entirely eliminate it.
Governance and compliance continuity keeps auditors satisfied by ensuring regulations like DORA have evidence that controls remain intact during third-party outages. This means logs, access rules, and encryption keys must travel with your workloads, not stay with the provider.
How Do CSP Outages Threaten Operational Resilience?
When a cloud region goes dark, every dependency you've placed behind that single provider vanishes with it. The triggers are often surprisingly mundane, yet their impact can be devastating.
Infrastructure Failures
Power loss inside a data center still tops the outage charts, despite redundant generators designed to prevent exactly this scenario. Failed drives, switches, or cooling units quickly snowball into service-wide downtime that affects every workload in that region.
Human Error and Configuration Issues
Human error like a mistyped command or mis-scoped IAM rule has taken entire platforms offline, leaving teams scrambling to understand what went wrong. Unvetted software patches can cripple the control plane that schedules every workload, while routing misconfigurations sever connectivity between regions. Even DDoS defenses sometimes overcorrect, blocking legitimate traffic and amplifying the very disruption they're meant to prevent.
Cascade Effects Across Dependencies
The real risk isn't any single failure. It's their shared blast radius. A DNS or identity outage in one availability zone cascades through microservices that expect internal APIs to be reachable, stalling transaction queues and corrupting in-flight data.
Regulatory and Compliance Implications
Regulators now treat that concentration risk as systemic. Both DORA and the expanded NIS2 mandate explicit safeguards against third-party ICT failures. Ignore them and you're not just facing revenue losses but also compliance penalties on top of the outage itself.
How Can Hybrid Architectures Strengthen Business Continuity?
When a cloud region falters, you need critical workloads to keep running somewhere else. A hybrid architecture with cloud-managed orchestration combined with local or regional execution provides exactly that safety net.
This model uses a central control plane to schedule jobs while data planes operate in your own VPCs, private clouds, or on-premises clusters. Workloads can swing between environments without code changes, so a failure in one provider never becomes a single point of business failure. The pattern has gained traction as organizations recognize the limitations of single-cloud strategies.
Hybrid deployment delivers several key advantages:
- Eliminates single points of failure by duplicating services across clouds and on-premise sites
- Enables rapid recovery through continuous replication that lets you spin up healthy copies the moment problems start
- Maintains data sovereignty by keeping sensitive data within chosen jurisdictions to simplify mandates like GDPR
- Provides workload portability so you can pick the best provider or move off one quickly without re-architecting
- Preserves cloud elasticity by bursting to public cloud for peak demand while falling back to on-prem resources when a provider stumbles
- Prevents configuration drift through shared control plane policies that work consistently across environments
Your regional data planes keep processing transactions even if a WAN link drops. Because policies and configurations live in a shared control plane, you avoid the drift that usually plagues multi-environment setups.
The result is straightforward: you stay in control, even when a cloud you depend on is not.
How Does Unified Orchestration Ensure Continuity During CSP Outages?
Unified orchestration maintains pipeline continuity by separating the control plane from each data plane. Because the control plane only holds schedules, metadata, and lineage but not your actual data, it can monitor every cloud region simultaneously and react when failures occur.
The orchestration layer provides continuity through several mechanisms:
- Real-time failure detection through health checks that register outages in seconds
- Automatic job re-queuing that pushes affected tasks to secondary regions or on-premises data planes
- State preservation by maintaining every run ID, schema change, and CDC offset in a durable metadata store
- Seamless recovery that lets backup environments pick up exactly where the primary left off
- Audit trail integrity through archived failover logs that preserve a single, authoritative history
Once the primary cloud recovers, unified orchestration reverses the process: it moves new tasks back to the original data plane, reconciles state, and archives failover logs for audit. This creates a fail-fast, recover-fast loop that shields your users from underlying disruptions while preventing duplicate writes or missing records even in chaotic outages.
How Does Airbyte Enterprise Flex Enable Operational Resilience?

Airbyte Enterprise Flex demonstrates how separated architecture maintains data flow even when your primary cloud falters. The cloud-managed control plane schedules and monitors every sync, while your data plane running in your VPC, on-premises, or a secondary cloud executes jobs locally. Only metadata crosses the wire, so your data never leaves trusted infrastructure.
During a provider outage, that separation becomes your lifeline:
- Autonomous failover as the control plane spins up identical pipelines in alternate regions
- Uninterrupted processing through outbound-only connectivity with no blocked inbound ports
- Complete feature parity with the entire 600+ connector catalog available everywhere
- No code changes or feature compromises when switching between environments
- Preserved audit trails through immutable, customer-hosted logs that meet DORA requirements
Consider a retail bank running data planes in Frankfurt and Paris. When AWS Frankfurt goes dark, Flex automatically reroutes scheduled CDC jobs to Paris within minutes. Transaction reporting continues uninterrupted, and compliance officers still have their audit trails.
How Can Enterprises Build and Test an Operational Resilience Strategy?
Waiting for the next outage to test your resilience strategy is like learning to swim during a flood. Your framework needs regular rehearsal under pressure to actually work when it matters.
1. Map Critical Services and Compliance Requirements
Start by mapping your mission-critical services and compliance-sensitive data flows. This isn't theoretical planning. You need to know exactly which systems keep your business running and which regulatory requirements can't be compromised during an outage.
2. Deploy Redundant Infrastructure
Deploy redundant data planes across regions or on-premises environments, then mirror your control plane or enable cross-cloud orchestration to maintain consistent management during failures.
3. Implement Automated Replication
Implement automated CDC replication with generous retention windows so your backup systems stay current. Run actual failover drills and measure your recovery time objectives against real business requirements.
4. Validate Governance Controls
Validate that your logs and governance controls work in every exercise. Compliance audits during outages aren't theoretical.
5. Execute Regular Drills and Continuous Improvement
Execute quarterly chaos engineering and tabletop drills, then adjust your playbooks based on what breaks. Continuous monitoring and governance audits keep your strategy current as your infrastructure evolves. The goal isn't perfect prevention but maintaining operations when prevention fails.
Why Hybrid Orchestration Defines the Future of Operational Resilience?
Building truly resilient systems means accepting that any provider can fail and designing accordingly. Hybrid architectures with unified orchestration provide autonomous failover and consistent governance across environments, turning potential disasters into manageable incidents.
This approach doesn't eliminate cloud dependencies but manages them intelligently. By separating control from execution, maintaining data sovereignty, and automating cross-environment failover, organizations can harness cloud benefits while avoiding cloud risks.
The question isn't whether your primary cloud will experience an outage. It's whether your business will survive when it does.
Airbyte Enterprise Flex delivers hybrid deployment that keeps your data in your infrastructure while providing the same 600+ connectors with no feature trade-offs. Talk to sales about building operational resilience with complete data sovereignty.
Frequently Asked Questions
What is the difference between redundancy and failover orchestration?
Redundancy deploys duplicate workloads across multiple regions or providers to eliminate single points of failure. Failover orchestration automates the process of detecting failures and rerouting traffic to healthy environments. You need both: redundancy provides the backup infrastructure, while orchestration ensures automatic switching without human intervention.
How does hybrid architecture reduce cloud vendor lock-in?
Hybrid architecture separates your control plane from data planes that run in any environment. Because workloads use the same connectors and codebase regardless of where they execute, you can move between clouds, on-premises, or mixed deployments without rewriting integration logic. This portability eliminates the switching costs that typically lock you into a single provider.
Can operational resilience strategies meet DORA compliance requirements?
Yes. DORA explicitly requires ICT risk management, third-party oversight, and exit strategies for cloud services. A hybrid architecture with unified orchestration demonstrates compliance by maintaining immutable audit trails, enabling rapid failover between providers, and proving data sovereignty during regulatory audits. Your logs and governance controls must remain accessible regardless of which cloud provider experiences an outage.
How quickly can systems failover during a cloud provider outage?
Failover speed depends on your architecture and monitoring frequency. Well-designed unified orchestration can detect outages within seconds through health checks, then reroute jobs to backup data planes in under a minute. The key is maintaining current replicas through continuous CDC replication and keeping metadata synchronized across all environments, so backup systems can resume exactly where primary systems stopped.

.webp)
