Sovereign Analytics Platform: Complete Architecture Guide
Summarize this article with:
✨ AI Generated Summary
Enterprise data teams face regulatory risks as legacy cloud analytics platforms often transfer sensitive data across borders, violating laws like GDPR and HIPAA. Sovereign analytics platforms solve this by ensuring data storage, processing, and encryption remain within customer-controlled jurisdictions, combining cloud-scale performance with strict compliance.
- Key features include customer-owned data planes, region-restricted storage, exclusive encryption key management, policy enforcement, and immutable audit logs.
- Deployment patterns: hybrid sovereign models, multi-region sovereign clusters, and air-gapped analytics balance compliance with scalability.
- Security and governance rely on end-to-end encryption, fine-grained access controls, policy automation, and cryptographic audit trails.
- Airbyte Enterprise Flex exemplifies this approach by separating control and data planes, enabling local execution with 600+ connectors and full data sovereignty.
Data teams at enterprise companies need real-time insights, but compliance teams say sensitive records can't leave national borders. GDPR violations cost millions in fines. HIPAA breaches trigger federal investigations. Export control violations can shut down entire product lines.
Legacy cloud analytics platforms create compliance gaps because their control planes, monitoring services, and automated failover routines sit outside customer regions. Even single-region database instances sync metadata to foreign support systems. The result: your data crosses borders without your knowledge, putting your organization at regulatory risk.
This guide shows enterprise architects and compliance teams how to build sovereign analytics platforms that keep data under your legal control while maintaining cloud-scale performance. You'll learn deployment patterns, governance controls, and practical architecture decisions that satisfy regulators without breaking your analytics workflows.
What Problems Does Data Sovereignty Solve for Analytics?
Cloud-scale analytics relies on elastic compute and global networks, but those capabilities directly conflict with laws requiring sensitive records stay within specific borders. When your BI dashboards or AI models depend on SaaS pipelines that replicate data through multiple regions, every cross-border hop risks compliance violations.
Regulators increasingly close gray areas with explicit residency mandates. GDPR, HIPAA, DORA, and export control regimes like ITAR require strict controls and documentation proving personal or restricted data never crosses unauthorized jurisdictions. Violations trigger more than fines: regulators suspend data flows, customers sue, and boards halt projects overnight.
Traditional approaches fail because vendors control where data actually gets processed. You might deploy in one region, but backups replicate globally, logs sync to central monitoring, and support teams access systems from anywhere. Each touch point creates liability.
Data sovereignty addresses this by guaranteeing you decide where data is stored, processed, and encrypted, under which jurisdiction its use is judged. It covers raw tables, backups, telemetry, and the keys that unlock them.
Current pain points include:
- Regulatory penalties: Multi-million dollar fines when records cross jurisdictions without authorization
- Audit failures: Unable to prove data never left approved boundaries
- Emergency rewrites: Sudden pipeline rebuilds when compliance gaps surface
- Reputational damage: Customer trust erodes faster than legal settlements resolve
With a sovereignty-first architecture, organizations eliminate hidden replication paths and regain verifiable control over every layer of their analytics stack.
What Defines a Sovereign Analytics Platform?
Your analytics team wants cloud-scale tools. Your legal team says data can't leave the country. A sovereign analytics platform resolves this tension by keeping all data inside infrastructure you control while delivering modern capabilities.
The difference isn't just hosting location. You can run private cloud through hyperscalers and still expose logs, encryption keys, or metadata to foreign jurisdictions. True sovereignty means you control the data flows, the encryption keys, and the audit trails.
Key characteristics:
- Customer-controlled data planes: Processing happens in your VPC or data center with minimal or no inbound network ports
- Region-restricted storage: Data stays in approved jurisdictions by architecture, not just policy
- Owned encryption keys: Vendor never touches your secrets or can decrypt your data
- Policy engines: RBAC and ABAC enforce access controls at every layer
- Immutable audit logs: Every query and transformation gets tracked with cryptographic proof
Orchestration can live in the cloud, but your compute and storage planes stay inside your jurisdiction. The platform enforces this boundary through architecture. Regional data zones become your data perimeter, and nothing crosses without explicit approval.
How Do You Architect a Sovereign Analytics Platform?
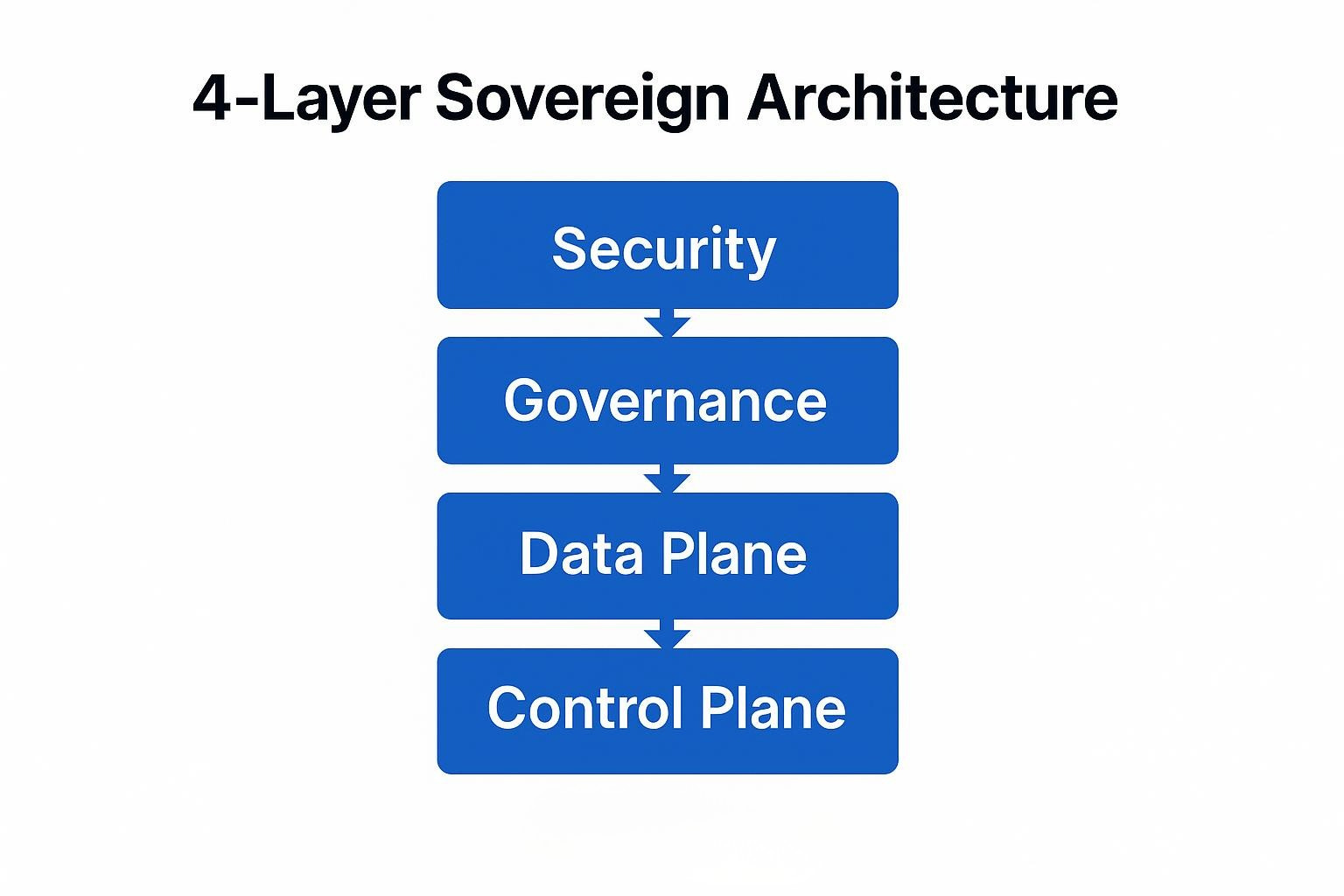
A sovereign analytics platform consists of four layers that keep every byte under your legal control while delivering cloud-scale performance.
Control Plane Architecture
The control plane sits in a managed cloud account and handles orchestration, scheduling, and monitoring. Because it never touches raw data, it can scale globally without breaking jurisdictional rules.
Airbyte Flex uses this pattern: the cloud control plane issues jobs but only metadata crosses the boundary. Customer records stay in your data plane. You get a single management interface without ceding custody.
Data Plane Design
All raw data lives in the data plane you own. Whether that means racks in your data center or a regional VPC, processing happens on infrastructure subject to your laws.
Processing workloads inside these zones is central to sovereignty. Hyperscale vendors now offer region-locked services and sovereign landing zones built on the same residency control principle.
Governance Layer
Above the data plane, a governance layer enforces fine-grained policies: lineage tracking, RBAC, ABAC, and clause-aware rules. Every query, transform, or model run gets logged and becomes provable.
Enterprise architects map these controls directly to frameworks like GDPR or HIPAA, avoiding manual spreadsheet audits that slow teams down.
Security Foundation
Security underpins everything through end-to-end encryption, external key management you hold, and immutable audit logs. In Airbyte Flex, secrets stay in your vault, not the vendor's, satisfying even the strictest "keys must remain on-premises" mandates.
Control-plane and data-plane separation simplifies networking. A single outbound HTTPS tunnel requires no inbound ports and no VPN. The control plane pushes config while your firewalls keep the rest of the world out. This pattern minimizes attack surface and keeps audits concise.
What Deployment Patterns Support Sovereign Analytics?
You have three ways to keep analytics compliant without giving up scale: hybrid sovereign models, multi-region sovereign clusters, and air-gapped analytics. Each puts your data plane under your control while letting orchestration live where it makes sense operationally.
1. Hybrid Sovereign Model
A cloud control plane schedules jobs to on-premises or private-cloud engines that never move raw data outside national borders. Policy-as-code keeps everything consistent across sites.
You get elastic scheduling and 600+ connectors without rebuilding your stack. Expect extra network security work and VPN costs.
Best for: Healthcare, fintech organizations needing fast rollout
2. Multi-Region Sovereign Clusters
When you operate across multiple jurisdictions, independent sovereign clusters work better. Storage and compute stay entirely local, then federated queries across clusters let you compare regions without triggering violations.
Higher infrastructure spend, but no latency spikes or regulatory headaches.
Best for: Global banks, SaaS vendors
3. Air-Gapped Analytics
Both control and data planes stay isolated, removing external dependencies and satisfying stringent telemetry rules. The trade-off is manual patching and limited real-time collaboration.
Best for: Defense, critical infrastructure
Pick the pattern that matches your compliance requirements, budget, and latency needs.
How Do You Enforce Security, Compliance, and Governance?
Regardless of deployment pattern, you maintain sovereignty by weaving security, compliance, and governance controls directly into the data plane. Every query, transformation, and model run must be provably compliant without slowing your team down.
Encryption and Key Management
End-to-end encryption secures data at rest and in transit. Regional boundaries ensure keys never leave jurisdictional zones. External key management lets you hold encryption keys, blocking cloud operators from unilateral access.
Immutable audit logging records every access event. Unified observability surfaces anomalies in real time, creating the transparency regulators demand.
Access Controls
Fine-grained RBAC and ABAC apply clause-scoped permissions, limiting each user to the minimal dataset required. Lineage tracking ties each dashboard back to its raw source, creating an evidentiary chain for regulators.
These controls work together to create defense in depth without creating bottlenecks.
Policy Automation
Automate safeguards with policy-as-code pipelines. GitOps workflows push signed policy bundles to each region. Local agents enforce them even when the cluster is air-gapped, or reconnect and reconcile when the link returns.
Healthcare teams keep ePHI inside national borders while running cross-region analytics on anonymized features for research. Airbyte's multi-jurisdictional compliance approach enables this by separating sensitive data processing from analytical insights.
Key governance controls:
- Column-level hashing: PII protection during data movement
- Row-level security: Query-time access filtering
- Attribute-based policies: Dynamic rules based on data classification
- Cryptographic audit trails: Tamper-proof compliance evidence
Hybrid estates add complexity: multiple clouds, on-premises clusters, and edge nodes all need the same rulebook. A centralized policy engine with offline replicas, plus cryptographically verifiable audits, lets you prove compliance everywhere without duplicating effort.
How Can a Sovereign Platform Still Enable Scalable Analytics?
Sovereignty doesn't mean shrinking your ambitions. It changes where and how the heavy lifting happens. You run containerized compute on autoscaling clusters inside each jurisdiction, keeping raw data close to source systems while spinning up extra capacity when query volumes spike.
Federated Query Processing
Once each region hosts its own compute pool, federated query engines stitch insights together. You submit one SQL statement, and engines fan it out to local nodes, aggregate results, and return a single answer. No cross-border data transfer required.
Performance Optimization
Performance tuning shifts from "scale up one warehouse" to "run many in parallel." Local caching cuts latency for interactive dashboards. Parallel execution across data planes shortens batch windows. Asynchronous replication syncs reference tables overnight so reports stay consistent.
Open Standards Integration
Standardized, open APIs tie the ecosystem together. You can swap engines or orchestration tools without rewriting pipelines. The result: full control over jurisdictional boundaries and the elastic scale you expect from modern analytics.
Scalability techniques:
- Regional compute pools: Auto-scaling within each jurisdiction
- Query federation: Cross-region analytics without data movement
- Intelligent caching: Frequently accessed data stays close to users
- Async replication: Reference data syncs during off-peak hours
How Does Airbyte Enterprise Flex Enable Sovereign Analytics Architectures?

Airbyte Enterprise Flex routes scheduling, monitoring, and connector metadata through a cloud-hosted control plane while running the entire data plane inside the VPC, data center, or air-gapped network you choose. No raw records ever reach Airbyte's servers.
The split is transparent: the control plane only pushes outbound API calls, and the data plane pulls container images and executes them locally. This lets you steer multiple regional planes from one dashboard without crossing borders.
Flex uses the same open-source codebase as Airbyte Cloud. You get 600+ connectors, change-data-capture replication, and modern destination support. No feature downgrades, just local execution. Teams report sub-minute clinical dashboards and under-30-second fraud models with zero cross-border data hops.
The open-source foundation means you can inspect, extend, and self-host if you deploy Airbyte's open-source edition yourself. Same Airbyte, same quality, any environment now fully under your control.
Key sovereignty features:
- External secrets management: Credentials stay inside your vault
- Immutable audit logs: Records remain in your environment
- Column-level hashing: PII masking guards regulated fields
- Regional isolation: Data residency enforced at the connector level
- 600+ connectors: Full catalog across all deployment models
- No vendor lock-in: Open-source roots ensure portability
How Should You Plan Your Move Toward Sovereign Analytics?
Map every dataset against your residency requirements first. Pick your highest-risk region and pilot a sovereign stack there. Negotiate full key custody in vendor contracts before you're locked in.
Start with your most sensitive workloads, prove the model works, then expand jurisdiction by jurisdiction. Airbyte Enterprise Flex provides hybrid deployment architecture with complete data sovereignty. Talk to Sales to discuss your compliance requirements and regional deployment needs.
Frequently Asked Questions
What Is the Difference Between Data Residency and Data Sovereignty?
Data residency means storing data in a specific geographic location. Data sovereignty adds legal control: you decide who can access the data, under which jurisdiction it falls, and who holds the encryption keys. Residency is about location; sovereignty is about control and legal jurisdiction.
Can You Run AI Workloads on a Sovereign Analytics Platform?
Yes. You train models on data inside your jurisdiction, then deploy them locally. Federated learning lets you improve models across regions without moving raw data. The key is ensuring training data, model weights, and inference results all stay within approved boundaries.
How Do You Handle Disaster Recovery in a Sovereign Architecture?
Replicate backups within the same jurisdiction or to approved secondary regions. Use cryptographic verification to prove backup integrity. Test recovery procedures regularly within jurisdictional boundaries. For multi-region deployments, each region maintains independent backup systems that never cross borders.
What Happens When Regulations Change in Your Jurisdiction?
Policy-as-code architectures adapt quickly. Update your policy definitions, push changes through GitOps pipelines, and local agents enforce new rules immediately. Because controls live in your infrastructure, not vendor systems, you control the update timeline. Immutable audit logs prove compliance before and after policy changes.

.webp)
