Sovereign Cloud vs. Traditional Cloud: Control Plane Architecture
Summarize this article with:
✨ AI Generated Summary
Traditional cloud architectures pose significant compliance risks by co-locating control and data planes, leading to data residency violations, audit gaps, and vendor lock-in. Sovereign cloud architectures separate control plane management from data plane execution, enabling organizations to maintain regulatory compliance while leveraging cloud scalability and modern capabilities.
- Complete control over data location and processing within customer-designated boundaries ensures compliance with GDPR, HIPAA, and other regulations.
- Hybrid models provide cloud-managed orchestration with customer-controlled data planes, supporting secure communication and immutable audit trails.
- Implementation challenges include integration complexity and skills gaps, but benefits include reduced compliance risks, operational overhead, and near-native performance.
- Airbyte Enterprise Flex exemplifies sovereign cloud solutions by delivering secure, regionally flexible data integration with 600+ connectors, maintaining data sovereignty without sacrificing performance.
Your compliance team just flagged another data residency violation. Customer data from your Frankfurt operations somehow ended up processed through servers in Virginia, triggering a GDPR investigation that could cost millions in fines. Meanwhile, your legacy ETL platform crashed during peak trading hours, and you have no fallback because everything runs through the same SaaS control plane.
This isn't a hypothetical scenario. It's Tuesday morning for data teams at regulated enterprises. Traditional cloud architectures force impossible choices between modern capabilities and regulatory compliance, leaving organizations vulnerable to sovereignty violations while constraining their ability to innovate.
Sovereign cloud architectures solve this fundamental problem by separating control plane management from data plane execution. Instead of choosing between "compliant but limited" or "powerful but risky," organizations can deploy cloud-managed orchestration while keeping sensitive data and processing within controlled boundaries.
What Is Sovereign Cloud Architecture?
A sovereign cloud represents a fundamental architectural shift that separates where your data lives from where your applications are managed. Unlike traditional cloud deployments, where both control and data planes operate in vendor-controlled environments, sovereign cloud architectures maintain strict boundaries around sensitive data while enabling modern cloud capabilities.
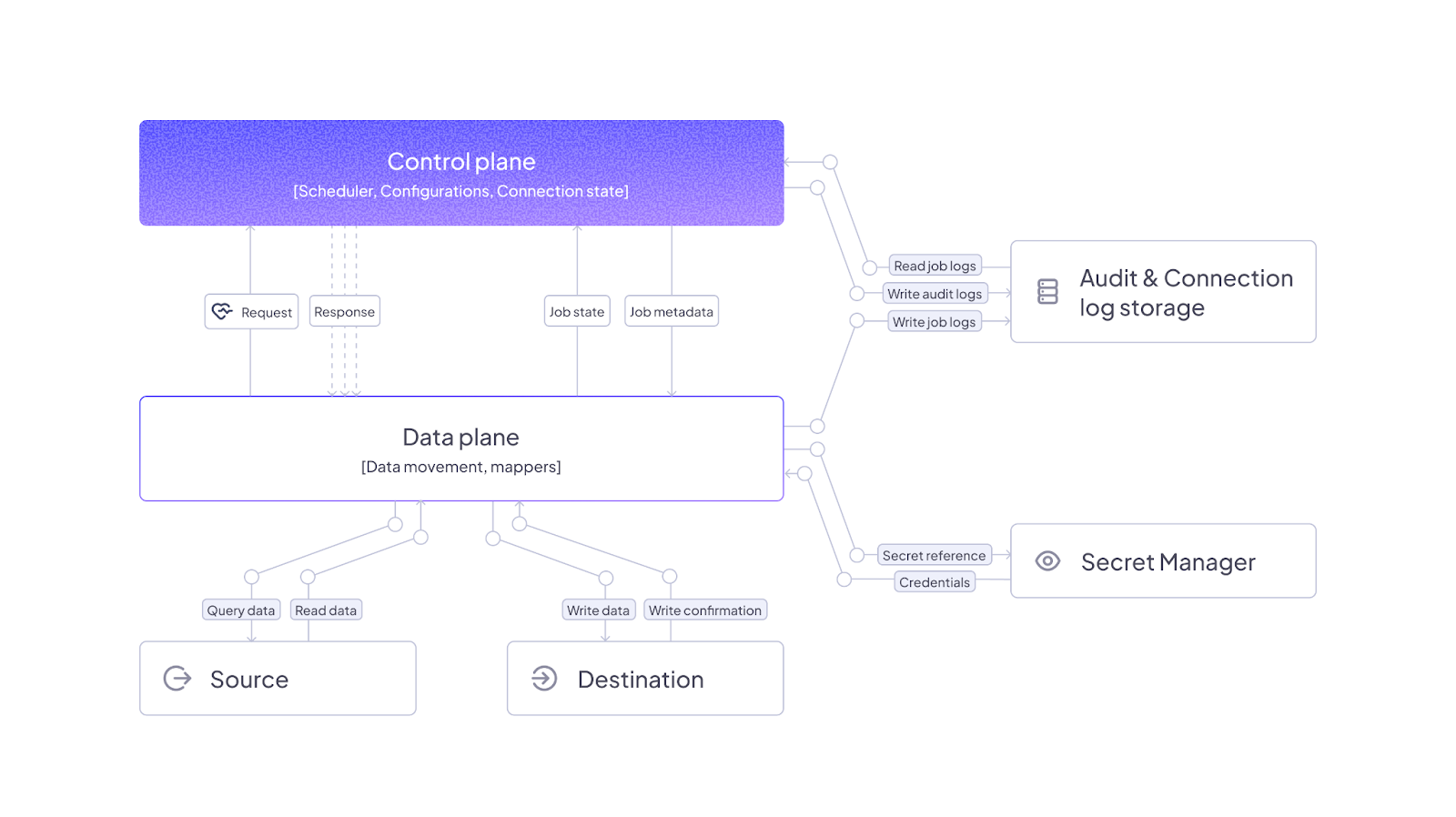
The core distinction lies in control plane separation. Your orchestration, monitoring, and management capabilities run in the cloud for operational efficiency, while your actual data processing happens within your controlled infrastructure—whether that's on-premises, private cloud, or specific regional data centers that meet your compliance requirements.
This isn't about compromising on functionality. Modern sovereign cloud implementations provide the same capabilities as their fully-managed counterparts, just with customer-controlled data planes that ensure regulatory compliance without operational trade-offs.
How Does Traditional Cloud Architecture Create Compliance Risks?
Traditional cloud architecture co-locates control planes and data planes within the same vendor-controlled environment. Your data, credentials, processing, and management all operate within infrastructure you don't directly control, creating multiple vectors for compliance violations.
- Data Residency Violations: When both orchestration and processing happen in vendor data centers, you lose granular control over data location. Cross-region failovers, load balancing, and scaling operations can move data across jurisdictional boundaries without explicit notification, violating GDPR, CCPA, or industry-specific residency requirements.
- Audit Trail Gaps: Traditional architectures often provide limited visibility into actual data movement and processing locations. When regulators demand proof that customer data never left specific geographic boundaries, you're dependent on vendor-provided logs that may not meet audit requirements.
- Vendor Lock-in Risks: Compliance requirements change faster than vendor capabilities. If new regulations require air-gapped processing or specific encryption standards, traditional cloud dependencies can create months-long migration projects with uncertain outcomes.
Financial services companies face particular challenges during trading hours when milliseconds matter, but compliance violations can trigger multi-million-dollar penalties. A single cross-border data movement during a routine scaling operation can result in regulatory investigations that dwarf any operational efficiency gains.
Sovereign Cloud vs. Traditional Cloud Comparison Matrix
What Are the Key Components of Sovereign Cloud Control Planes?
Sovereign cloud architectures implement clear separation between management functions that benefit from cloud scalability and data processing that requires strict control. Understanding these components helps evaluate whether specific implementations truly solve sovereignty challenges or simply rebrand existing limitations.
1. Cloud-Managed Orchestration Layer
The orchestration layer handles scheduling, monitoring, and workflow management through cloud infrastructure tuned for reliability and scalability. This includes job queuing, error handling, alerting, and integration with enterprise monitoring systems.
Key Capabilities:
- Centralized monitoring and alerting across distributed data planes
- Automated scaling decisions based on workload demands
- Integration with enterprise identity and access management systems
- Real-time performance tuning and resource allocation
2. Customer-Controlled Data Planes
Data planes execute actual processing within customer-controlled infrastructure, ensuring sensitive data never leaves approved boundaries. These environments connect securely to cloud orchestration while maintaining complete data sovereignty.
Critical Features:
- Cryptographic isolation ensures data and credentials stay within controlled boundaries
- Regional deployment options support data residency requirements
- Automated compliance logging for regulatory audit requirements
- Integration with existing enterprise security and network infrastructure
3. Secure Communication Channels
The communication layer enables cloud orchestration to manage distributed data planes without compromising security or sovereignty. This typically involves encrypted API communications that transmit orchestration commands while ensuring data payloads remain within controlled environments.
Security Requirements:
- End-to-end encryption for all control communications
- Certificate-based authentication preventing unauthorized access
- Network-level isolation supporting air-gapped deployments when required
- Complete audit logging of all control plane interactions
Why Do Regulated Industries Require Hybrid Control Plane Models?
Regulated industries operate under compliance frameworks that explicitly prohibit certain data movements while demanding operational capabilities that benefit from cloud scalability. Hybrid control plane models address these seemingly contradictory requirements without forcing trade-offs between compliance and capability.
Healthcare: HIPAA Compliance Challenges
Hospital networks must keep ePHI within controlled environments while supporting sub-minute dashboards for bed occupancy and lab turnaround times. Traditional SaaS platforms violate HIPAA by processing patient data in shared cloud environments, while legacy on-premises systems can't deliver the real-time capabilities clinical operations demand.
Financial Services: Cross-Border Trading Requirements
Trading firms need real-time fraud detection that fails when CDC lag exceeds 30 seconds, but GDPR and CCAR requirements force data to stay within specific regional boundaries. Cloud-only platforms can't guarantee data residency during high-volume periods, while on-premises alternatives lack the processing scale needed for millisecond decision-making.
Defense: Export Control Restrictions
Aerospace and defense contractors operate under ITAR restrictions that ban defense-related data from leaving US-controlled environments. Any platform that processes this data through foreign-owned cloud infrastructure—even temporarily—violates export control laws with multi-million-dollar penalties.
Manufacturing companies face similar challenges with industrial IoT data that includes proprietary processes or customer information subject to various international regulations. Hybrid architectures enable global scale while maintaining regional compliance.
How Do Sovereign Clouds Handle Data Residency Requirements?
Data residency compliance requires more than geographic server placement—it demands granular control over data movement, processing locations, and access patterns that traditional cloud architectures cannot guarantee. Sovereign cloud implementations address these requirements through architectural controls rather than policy promises.
- Geographic Boundary Enforcement: Instead of relying on vendor policies about data location, sovereign architectures implement cryptographic controls that prevent data from leaving approved boundaries. Data processing happens within customer-designated regions or facilities, with orchestration commands transmitted separately from actual data payloads.
- Audit-Ready Documentation: Regulatory audits require proof that sensitive data never crossed jurisdictional boundaries, with timestamped evidence of processing locations and access patterns. Sovereign cloud architectures generate immutable audit logs that track every data movement and processing operation within customer-controlled environments.
- Failover and Scaling Controls: Traditional cloud platforms may move data during scaling operations or failover scenarios without explicit customer control. Sovereign implementations ensure that even automatic scaling and disaster recovery operations respect data residency requirements, preventing compliance violations during operational disruptions.
The European Union's Digital Operational Resilience Act (DORA) exemplifies why architectural sovereignty matters more than policy compliance. DORA requires financial institutions to demonstrate granular control over data processing locations and third-party dependencies, with evidence that customer data can be recovered and processed entirely within EU boundaries during crisis scenarios.
What Are the Performance Trade-offs in Sovereign Cloud Architectures?
Organizations often assume that sovereignty requirements necessarily compromise performance, but modern hybrid architectures can deliver superior performance characteristics while maintaining compliance. The key lies in understanding where performance tuning provides business value versus where compliance constraints create necessary boundaries.
- Network Latency Considerations: Separating control planes from data planes does introduce additional network hops for orchestration commands, but this impact is negligible for most enterprise workloads. Data processing happens locally within customer infrastructure, so the latency-sensitive operations maintain optimal performance characteristics.
- Scaling Efficiency: Cloud-managed orchestration often scales more efficiently than fully on-premises alternatives because resource allocation decisions benefit from broader infrastructure visibility and automated resource allocation. Customer-controlled data planes can implement scaling policies tuned for specific workload patterns while using cloud intelligence for resource planning.
- Operational Overhead: Hybrid architectures reduce operational overhead compared to fully self-managed alternatives while maintaining sovereignty. Organizations avoid managing orchestration infrastructure, monitoring systems, and control plane updates while retaining complete control over data processing environments.
Real-world implementations show that properly designed sovereign architectures deliver 95%+ of fully-managed performance while eliminating compliance risks. The 5% performance difference is typically offset by reduced regulatory overhead and faster audit completion times.
How Do You Evaluate Sovereign Cloud Security Controls?
Evaluating sovereign cloud security requires examining both technical controls and operational transparency that traditional cloud assessments often overlook. Compliance isn't just about meeting current regulatory requirements—it's about maintaining sovereignty as regulations evolve and threat landscapes change.
Technical Control Assessment
- Data Plane Isolation: Verify that customer data never transits vendor-controlled infrastructure, even for processing operations. This includes encrypted communications, temporary storage, logging, and error handling that might inadvertently expose sensitive information outside controlled boundaries.
- Cryptographic Independence: Ensure that encryption keys and certificates remain within customer control, preventing vendor access to sensitive data even during support operations. Key management systems should operate entirely within customer infrastructure with no vendor key escrow or recovery capabilities.
- Network Segmentation: Confirm that data planes operate with network-level isolation from vendor infrastructure and other customer environments. Even control communications should transit dedicated channels that prevent data leakage through shared network infrastructure.
Operational Transparency Verification
- Audit Log Completeness: Request samples of audit logs to verify that every data access, movement, and processing operation generates immutable records suitable for regulatory compliance. Logs should include sufficient detail to reconstruct data lineage for compliance investigations.
- Incident Response Procedures: Review how security incidents are handled, particularly whether vendor support personnel can access customer data during troubleshooting operations. Sovereign architectures should enable complete support without compromising data plane isolation.
- Compliance Documentation: Evaluate whether the vendor provides compliance documentation that supports your regulatory requirements, including SOC 2, GDPR, HIPAA, or industry-specific certifications relevant to your operational environment.
What Implementation Challenges Should You Anticipate?
Sovereign cloud implementations involve organizational and technical complexity beyond traditional cloud migrations. Understanding common challenges helps organizations plan realistic timelines and resource requirements while avoiding architecture decisions that compromise long-term flexibility.
Technical Integration Challenges
- Integration Complexity: Hybrid architectures require secure integration between cloud orchestration and customer data planes, often involving network configurations, certificate management, and security policy coordination that spans multiple operational domains.
- Performance Tuning: Tuning hybrid architectures for optimal performance requires understanding both cloud orchestration characteristics and local infrastructure capabilities, with monitoring and performance tuning spanning multiple environments.
Organizational Readiness Factors
- Skills Gap Management: Teams need expertise in both cloud orchestration platforms and on-premises infrastructure management, plus specialized knowledge of regulatory compliance and security controls. This combination of skills is rare and requires dedicated training programs.
- Change Management: Organizations must establish operational procedures that maintain sovereignty during routine operations, including deployment processes, incident response, and capacity planning that respect compliance boundaries.
Successful implementations typically involve 3-6 month implementation phases with dedicated project teams that include both cloud and compliance expertise. Organizations that attempt to treat sovereign cloud as a simple configuration change often encounter deployment delays and architecture compromises that limit long-term value.
How Will Sovereign Cloud Requirements Evolve?
Regulatory frameworks continue evolving toward greater sovereignty requirements, with new legislation emerging across multiple jurisdictions that demand more granular control over data processing and storage locations. Organizations need sovereign cloud architectures that adapt to changing requirements without requiring complete re-architecture.
- Emerging Regulatory Frameworks: The EU's Digital Services Act and proposed AI regulations include specific data processing location requirements that traditional cloud architectures cannot support. Similar legislation is developing in other jurisdictions, creating a global trend toward data sovereignty requirements.
- Industry-Specific Requirements: Financial services, healthcare, and defense industries face increasingly strict requirements for data processing transparency and control. These requirements often include specific infrastructure ownership, processing location verification, and audit capabilities that go beyond current cloud offerings.
- Geopolitical Considerations: International tensions are driving governments toward data sovereignty legislation that restricts cross-border data flows, even for routine processing operations. Organizations with global operations need architectures that can adapt to changing geopolitical requirements without business disruption.
The trend is clearly toward greater sovereignty requirements rather than relaxation of existing rules. Organizations that invest in truly sovereign architectures today will have competitive advantages as regulatory requirements continue tightening across multiple industries and jurisdictions.
Sovereign cloud architectures represent the future of enterprise data processing for regulated industries. By separating control plane management from data plane execution, organizations can use modern cloud capabilities while maintaining complete control over sensitive data and meeting evolving compliance requirements.
Airbyte Enterprise Flex Delivers Sovereign Cloud Architecture With 600+ Connectors
Stop choosing between cloud capabilities and compliance requirements. Airbyte Enterprise Flex delivers true hybrid control plane architecture that addresses every sovereignty challenge discussed in this article—without compromising on the modern data integration capabilities your business demands.
Complete Data Sovereignty: Your customer data never leaves your environment. Airbyte manages the orchestration, monitoring, and job scheduling through our cloud control plane, while all data processing happens within your VPC or on-premises infrastructure. This architectural separation ensures regulatory compliance while eliminating the operational overhead of managing orchestration infrastructure.
Enterprise-Grade Security Controls: Airbyte Enterprise Flex includes the governance capabilities that regulatory frameworks require. External secrets management integrates with your existing credential systems, ensuring sensitive connection information stays within your control. Column-level hashing provides PII protection during data movement, while comprehensive audit trail logging stores compliance records in your own infrastructure—exactly what auditors need for GDPR, HIPAA, and SOX compliance.
Regional Flexibility: Deploy multiple isolated workspaces across different regions to meet data residency requirements. Whether you need separate processing for EU and US customer data or air-gapped deployment for defense contractors, Airbyte Enterprise Flex's flexible data plane architecture adapts to your compliance requirements without feature compromises.
AWS PrivateLink Support: Secure VPC connectivity ensures that even control communications between the cloud orchestration layer and your data planes never transit the public internet. This network-level isolation supports the most stringent security requirements while maintaining the operational benefits of cloud-managed orchestration.
Unlike competitors who force trade-offs between sovereignty and capability, Airbyte Enterprise Flex provides the complete 600+ connector library with consistent quality across all deployment models. Same connectors, same reliability, same performance—just with architectural controls that keep your sensitive data exactly where compliance requires it to stay.
Talk to Sales about deploying sovereign cloud architecture that scales with your regulatory requirements without limiting your data integration capabilities.
Frequently Asked Questions
What makes a cloud deployment truly sovereign
A deployment is considered sovereign when the organization controls where data is processed, stored, and encrypted—rather than the vendor. In this model, orchestration can run in the cloud, but all data processing remains within your controlled infrastructure. This ensures compliance with data residency and sovereignty laws while maintaining modern cloud functionality.
Can sovereign cloud architectures still integrate with public cloud services
Yes. Secure, outbound-only connections such as AWS PrivateLink or private service endpoints allow communication between the cloud orchestration layer and your internal systems. This setup keeps sensitive data inside your environment while enabling you to use cloud-based monitoring, scaling, and automation tools.
How difficult is it to migrate from a traditional cloud to a sovereign model
Migration complexity depends on your existing architecture and compliance landscape. Most organizations move in phases, starting with their most regulated workloads. The key is to separate control plane functions like scheduling and monitoring from data plane execution early in the design process to minimize disruption.
Does using a sovereign cloud mean sacrificing performance
No. Because data processing happens locally, latency-sensitive workloads often perform as well as—or better than—traditional cloud setups. The only extra overhead comes from orchestration traffic, which is minimal. Platforms like Airbyte Enterprise Flex provide full performance and compliance without operational trade-offs.

.webp)
