Top companies trust Airbyte to centralize their Data







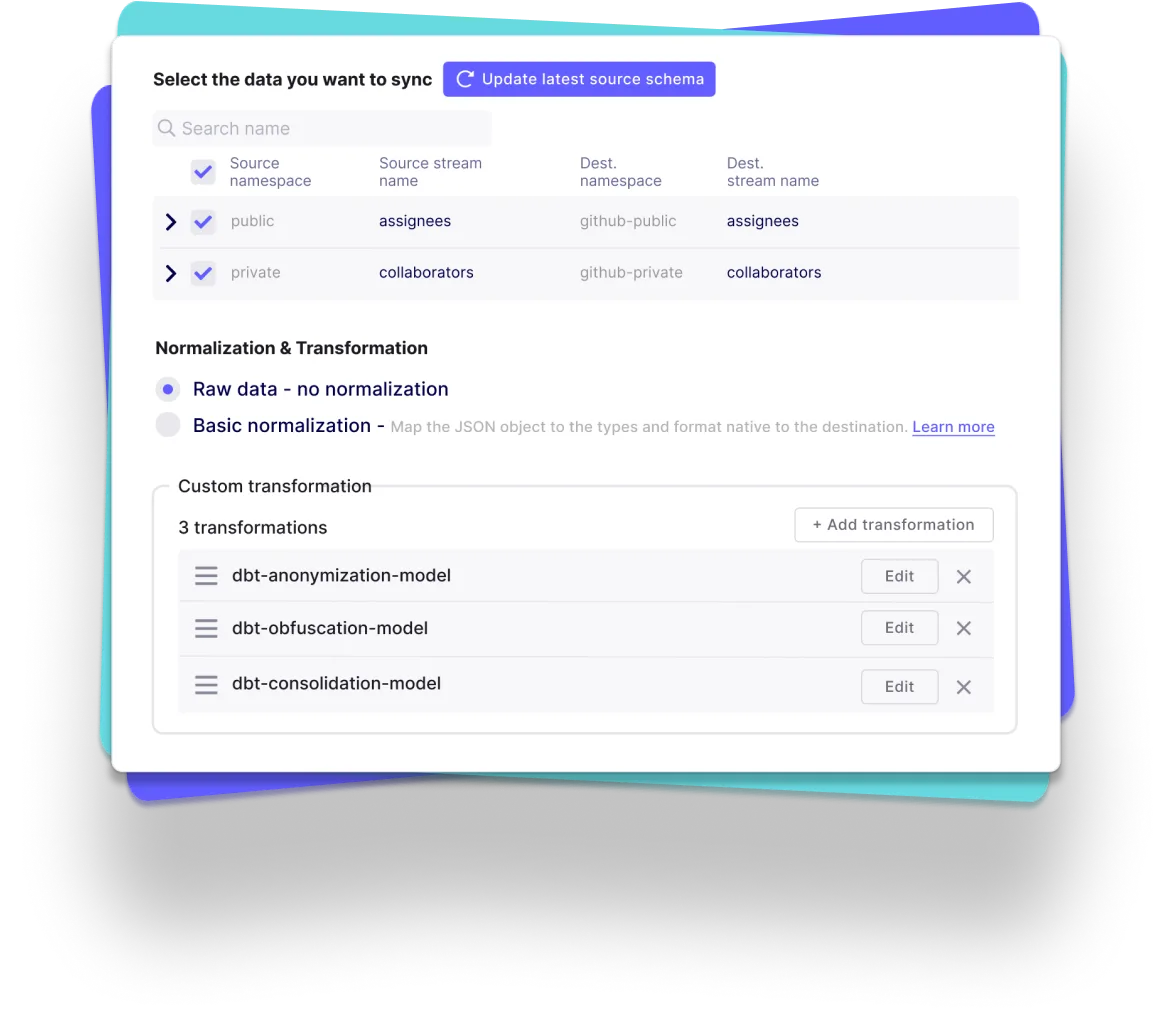
Sync your Data
Ship more quickly with the only solution that fits ALL your needs.
As your tools and edge cases grow, you deserve an extensible and open ELT solution that eliminates the time you spend on building and maintaining data pipelines
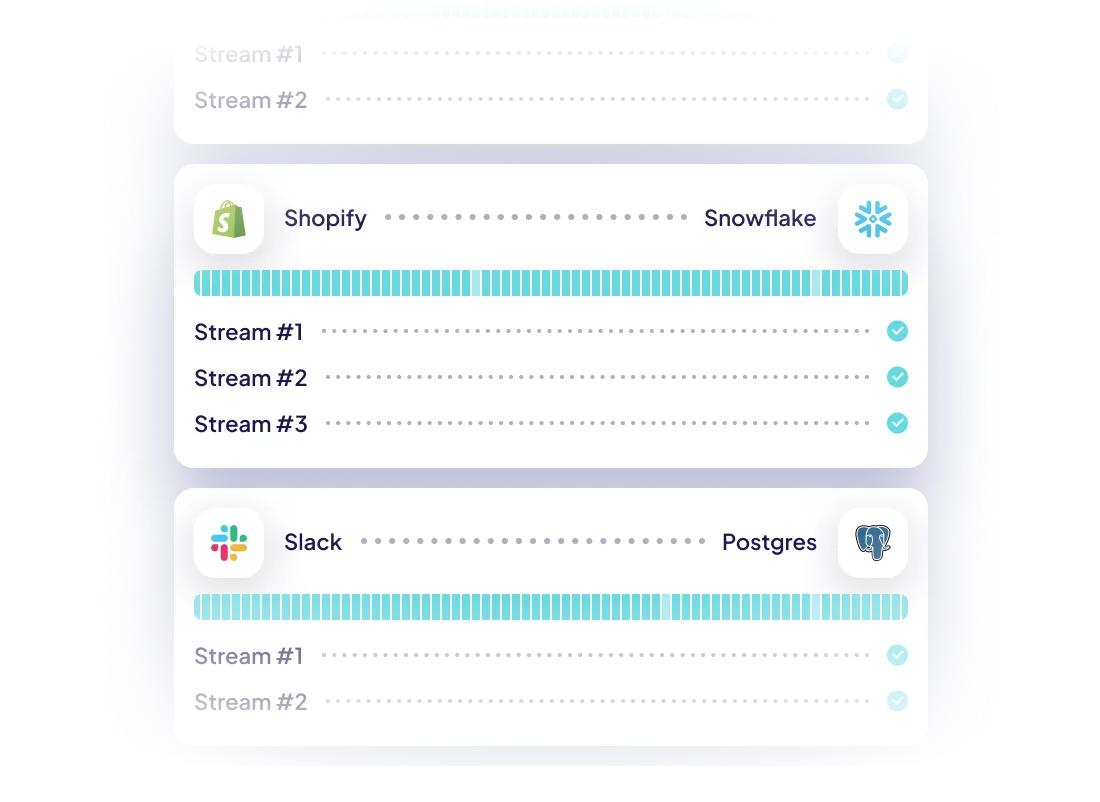
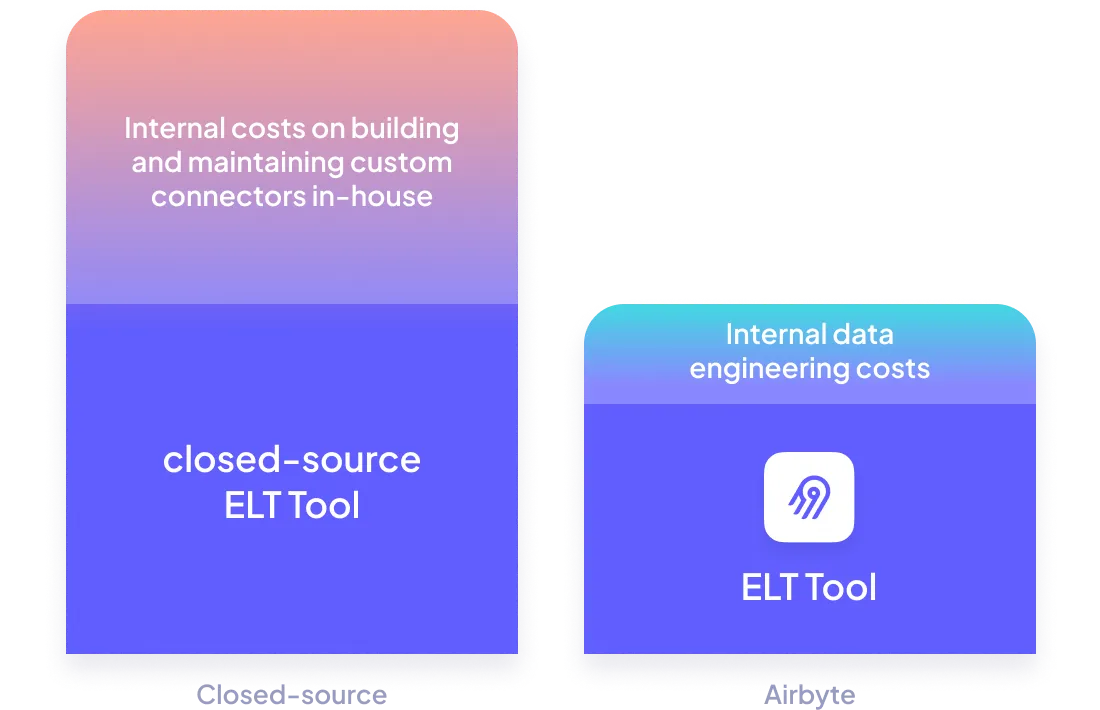
Leverage the largest catalog of connectors

Cover your custom needs with our extensibility

Free your time from maintaining connectors, with automation
- Automated schema change handling, data normalization and more
- Automated data transformation orchestration with our dbt integration
- Automated workflow with our Airflow, Dagster and Prefect integration

Reliability at every level
Airbyte Open Source
Airbyte Cloud
Airbyte Enterprise

Why choose Airbyte as the backbone of your data infrastructure?
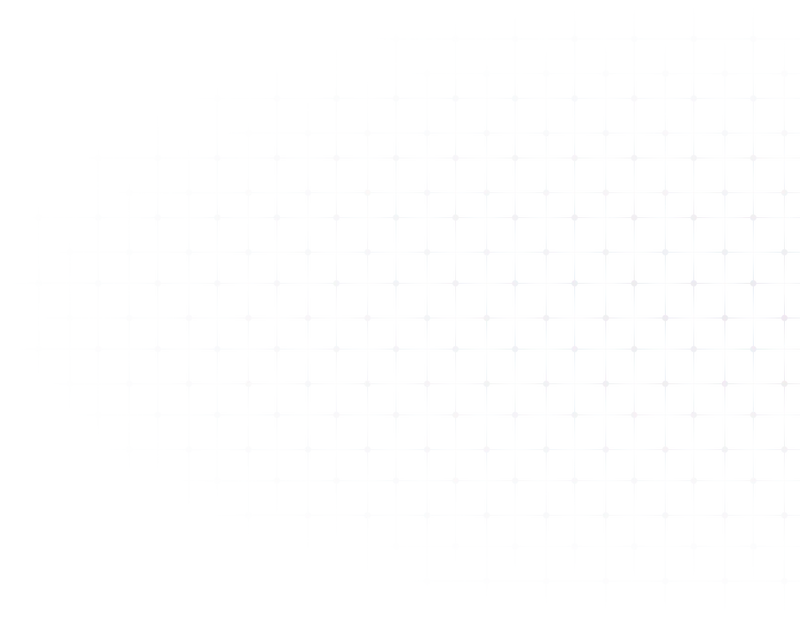
Keep your data engineering costs in check
Get Airbyte hosted where you need it to be
- Airbyte Cloud: Have it hosted by us, with all the security you need (SOC2, ISO, GDPR, HIPAA Conduit).
- Airbyte Enterprise: Have it hosted within your own infrastructure, so your data and secrets never leave it.

White-glove enterprise-level support
Including for your Airbyte Open Source instance with our premium support.

Fnatic, based out of London, is the world's leading esports organization, with a winning legacy of 16 years and counting in over 28 different titles, generating over 13m USD in prize money. Fnatic has an engaged follower base of 14m across their social media platforms and hundreds of millions of people watch their teams compete in League of Legends, CS:GO, Dota 2, Rainbow Six Siege, and many more titles every year.
Ready to get started?
FAQs
What is ETL?
ETL, an acronym for Extract, Transform, Load, is a vital data integration process. It involves extracting data from diverse sources, transforming it into a usable format, and loading it into a database, data warehouse or data lake. This process enables meaningful data analysis, enhancing business intelligence.
The intruder is an online vulnerability scanner that finds cyber security weaknesses in your digital infrastructure, to avoid costly data breaches. The intruder was founded in 2015 to help solve the information overload crisis in vulnerability management. Having worked both as an ethical hacker for tier one companies, and for blue teams defending critical national infrastructure, That while vulnerability management tools were great at finding issues, they were less useful when it came to prioritizing them, tracking them, and timely alerting when problems arose.
Intruder's API provides access to a wide range of data related to security testing and vulnerability management. The following are the categories of data that can be accessed through Intruder's API:
1. Vulnerability data: This includes information about the vulnerabilities detected during the security testing process, such as the severity level, description, and recommended remediation steps.
2. Scan data: This includes information about the scans performed, such as the start and end time, scan type, and scan results.
3. Asset data: This includes information about the assets being scanned, such as the IP address, hostname, and operating system.
4. User data: This includes information about the users who have access to the Intruder platform, such as their email address, name, and role.
5. Report data: This includes information about the reports generated by the Intruder platform, such as the report type, format, and content.
6. Integration data: This includes information about the integrations with other tools and platforms, such as the API keys, webhook URLs, and authentication credentials.
Overall, Intruder's API provides a comprehensive set of data that can be used to improve security testing and vulnerability management processes.
What is ELT?
ELT, standing for Extract, Load, Transform, is a modern take on the traditional ETL data integration process. In ELT, data is first extracted from various sources, loaded directly into a data warehouse, and then transformed. This approach enhances data processing speed, analytical flexibility and autonomy.
Difference between ETL and ELT?
ETL and ELT are critical data integration strategies with key differences. ETL (Extract, Transform, Load) transforms data before loading, ideal for structured data. In contrast, ELT (Extract, Load, Transform) loads data before transformation, perfect for processing large, diverse data sets in modern data warehouses. ELT is becoming the new standard as it offers a lot more flexibility and autonomy to data analysts.