PCI DSS v4.0.1: Card Data Processing in Hybrid Cloud Environments
Summarize this article with:
✨ AI Generated Summary
PCI DSS v4.0.1, effective from 2025, refines hybrid cloud and data integration security by clarifying shared responsibilities, expanding network segmentation, and endorsing phishing-resistant authentication without adding new controls. Key compliance practices include:
- Separating control plane (orchestration) from data plane (card data processing) to limit audit scope.
- Tokenizing PANs early, encrypting data with customer-managed keys, and enforcing TLS 1.2+ in transit.
- Maintaining immutable audit logs, centralized credential vaults, and codifying policies as infrastructure code.
Platforms like Airbyte Enterprise Flex enable compliance by keeping raw card data within customer-controlled environments while managing orchestration in the cloud, ensuring data sovereignty, encryption, and comprehensive logging for hybrid PCI DSS adherence.
Processing even a single credit card transaction exposes you to crushing fines, chargebacks, and brand damage if that data leaks. Teams spend more time wrangling breach fallout than shipping features, so preventing the leak in the first place matters more than post-mortems.
That's why the Payment Card Industry Data Security Standard (PCI DSS) remains the security north star. Published by the PCI Security Standards Council, the framework's 12 requirements cover everything from network isolation to continuous monitoring, giving you a baseline every assessor recognizes.
Version 4.0.1, released in 2024 and effective since 2025, doesn't add brand-new controls but sharpens language for cloud and hybrid deployments and recognizes phishing-resistant authentication. Even in distributed architectures, this standard remains the benchmark auditors and your customers trust.

What Changed in PCI DSS v4.0.1 for Data Integration and Hybrid Workloads?
The updated standard, effective since January 1 2025, doesn't introduce new controls, but it tightens the language you rely on when card data moves between on-premises systems and cloud services. The update's biggest shift is clarity: it spells out who owns which safeguards, so hybrid pipelines no longer fall into grey zones.
- Expanded network segmentation definitions. The standard retains the term 'network segmentation' but expands the Applicability Notes to map responsibility when you route cardholder data through a cloud provider's VPC or a SaaS iPaaS tool. You remain accountable for every byte, even if a vendor operates the infrastructure.
- Phishing-resistant authentication accepted. Requirement 8 now lets you replace traditional MFA with phishing-resistant factors such as FIDO2 keys. This is a practical win for federated SSO in multi-cloud environments.
- Clearer encryption guidance. Requirement 3 now clarifies keyed hashing for rendering PAN unreadable, aligning with cloud KMS services that sign data instead of storing raw keys. Legal-exception language was added so your cross-border data flows respect local crypto laws without breaking compliance requirements.
- Refined patch management scope. The 30-day mandate now targets critical and high-risk vulnerabilities. This eases the cadence mismatch between vendor-managed SaaS stacks and your own hosts.
- Strengthened shared-responsibility model. Each tweak reinforces that you must define, document, and audit how connectors, message queues, and storage tiers meet the refined text. The key insight here is treating every integration hop as inside scope unless you can prove isolation.
These refinements give you firmer guardrails without expanding scope, letting hybrid data teams harden pipelines with less ambiguity.
How Does PCI DSS Apply to Data Integration Pipelines?
When you move card data between systems, the standard follows every byte.
Requirement 3 Governs Storage
The framework's language makes Requirement 3 your north star for storage. PANs must stay unreadable whether they land in a warehouse, object store, or staging table.
Requirement 4 Secures Data in Transit
Requirement 4 demands TLS 1.2+ on every hop so that traffic between sources, queues, and destinations is never exposed in transit.
Requirement 10 Creates Audit Trails
Requirement 10 then insists you log and review each access or change, creating an immutable trail of every extract, transform, and load.
Any connector, API call, or transformation service that touches a Primary Account Number is automatically in scope. Even if the tool only parses metadata, the moment it can see the PAN, your assessor will see it too.
Hybrid Architectures Limit Cloud Scope
Hybrid architectures add another wrinkle. A typical hybrid data integration approach splits orchestration into a control plane (often cloud-hosted) and processing into a data plane inside your VPC or data center, enabling movement of the encrypted payload. While popular in the industry and used by some third-party providers, this is not a specific requirement from AWS fault isolation guidance. This separation limits scope in the cloud without sacrificing automation.
Modern platforms like Airbyte Enterprise Flex adopt the same pattern: their hybrid control plane handles jobs, yet your data plane, running on your infrastructure, extracts, masks, and loads the card data, following enterprise security architecture principles. You keep keys, logs, and full visibility, exactly what Requirements 3, 4, and 10 expect.
How Can Hybrid Cloud Architecture Support PCI DSS Compliance?
Separating orchestration from data movement keeps your cardholder data environment (CDE) small and testable. In a hybrid model, the control plane runs in the cloud while the data plane that processes PANs stays inside your VPC or on-premises network.
Because the control plane never touches live card data, you can expose it through hardened APIs. The data plane initiates all traffic over outbound-only channels, maintaining security without compromising functionality. This design proves especially valuable when demonstrating clear boundaries to assessors.
Implement tokenization for PANs as early as possible and encrypt every file with customer-managed keys. Store those keys in native KMS or HSM services to support Requirement 3 as workloads span regions. Enforce TLS on every hop between planes for Requirement 4, and stream logs to an immutable store for Requirement 10.
Full compliance demands additional controls such as monitoring, access management, and comprehensive security processes. When policies live in code, you can audit changes once rather than on every edge system.
By aligning each layer to a discrete control set, you limit assessor scope and keep hybrid compliance manageable.
What Are the Main Challenges of PCI DSS Data Integration in Hybrid Environments?
Moving cardholder data between on-premises systems and multiple clouds invites risks you rarely see in a single environment. You're juggling different security models, ownership boundaries and audit trails, all while the clock for attestation keeps ticking.
- Shadow data flows through SaaS tools. Marketing or finance teams spin up connectors that copy PANs outside the CDE. Without continuous discovery, you never know these flows exist until an assessor asks. Hybrid data integration compliance best practices recommend inventory scans that trace every API and bucket touching payment data.
- Limited visibility into vendor-managed connectors. Cloud ETL vendors hide logs and credentials, making it impossible to prove Requirement 10 logging or Requirement 7 least-privilege scopes. Deploy connectors in a customer-controlled data plane to retain full audit logs and rotate secrets on your schedule.
- Inconsistent encryption between regions. One cloud might default to AES-256 while another holds legacy volumes. Align every environment with the same KMS policies and document key custody in one place. Use outbound-only data plane tunnels to keep keys local to each jurisdiction.
- Cross-cloud audit documentation fragmentation. Assessors want a single narrative, but logs live in CloudWatch, syslog and vendor portals. Funnel every control-plane API call and data-plane event into a centralized SIEM.
A real-world example: a regional payment acquirer operating across EU and APAC runs orchestration in a cloud control plane, yet each region processes transactions locally. By enforcing outbound-only connections, unified KMS policies and a cross-region SIEM feed, the acquirer proves isolation, encryption and monitoring without pausing business growth.
How Should Enterprises Architect PCI DSS-Compliant Data Pipelines?
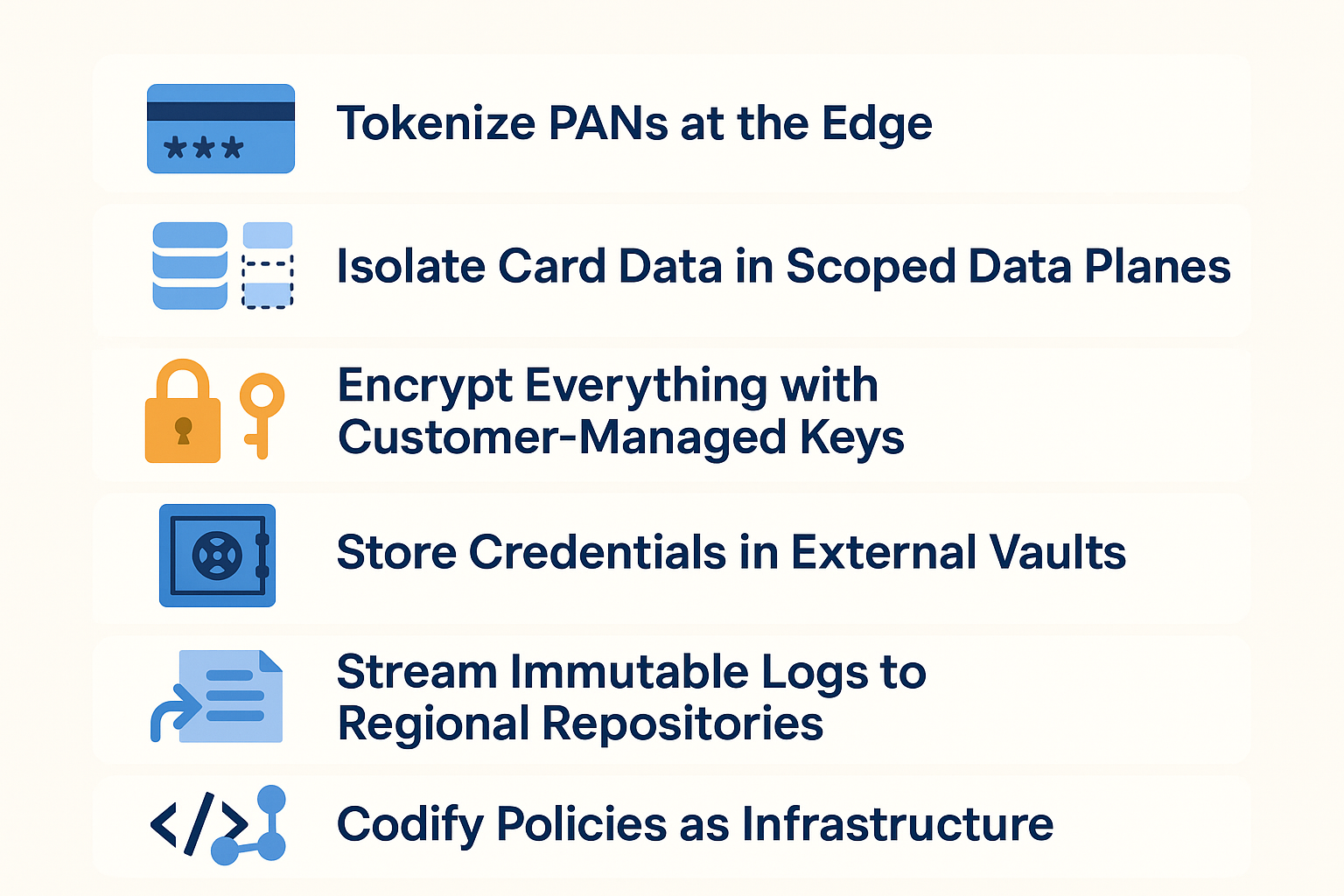
Keep your audit scope small and your life easier by funneling card data through a tightly isolated data plane while orchestration lives elsewhere. This control-plane/data-plane split underpins every design choice that matters.
1. Tokenize PANs at the Edge
The foundation of compliant architecture begins with classifying payloads at the edge and replacing PANs with tokens wherever your workflow allows. Tokenization services shrink scope before data even lands in your infrastructure.
2. Isolate Card Data in Scoped Data Planes
Direct any remaining card data exclusively into a scoped data plane (typically a private VPC or on-premises segment) while a cloud control plane handles scheduling and metadata. Outbound-only connectivity from the data plane eliminates risky inbound firewall holes that auditors love to scrutinize.
3. Encrypt Everything with Customer-Managed Keys
Encryption becomes your second line of defense. Use strong encryption algorithms such as TLS 1.2+ in motion and AES-256 at rest, and anchor keys in your cloud KMS or HSM. These practices help facilitate collecting evidence for Requirements 3 and 4, though comprehensive audit logs and trails are needed for PCI DSS compliance during audits.
4. Store Credentials in External Vaults
Expose control-plane APIs through signed, least-privilege roles, then store those credentials in an external secrets vault. Never embed keys in config files; it's the fastest way to fail a compliance review.
5. Stream Immutable Logs to Regional Repositories
Stream detailed, immutable logs to regionally fenced repositories. This approach makes continuous review painless rather than a quarterly nightmare.
6. Codify Policies as Infrastructure
Finally, codify every network rule, IAM role, and connector configuration as infrastructure code. Policy-as-code engines keep inadvertent scope creep from sneaking into production deployments.
This flow ensures tokenized, encrypted data stays in environments you govern, while auditors see a provable chain of controls that maps cleanly to Requirements 3, 4, 7, and 10.
How Does Airbyte Enterprise Flex Enable PCI DSS Data Integration Compliance?

You can keep cardholder data fully under your control while using a managed orchestration layer by deploying Airbyte Enterprise Flex. The platform splits responsibilities between a cloud-hosted hybrid control plane and a customer-owned data plane.
Key compliance capabilities include:
- Complete data sovereignty. Only job metadata flows to the control plane. Raw PANs never leave your network perimeter. The data plane initiates outbound-only connections, so you avoid opening inbound firewall ports.
- Clean architectural boundaries. This architecture maps cleanly to the control-plane/data-plane separation that auditors expect in hybrid assessments.
- End-to-end encryption. Every sync is encrypted in transit with TLS and stored with AES-256 under keys you manage through your preferred KMS.
- External credential management. Database and API credentials live in an external vault, not in the Airbyte UI, supporting Requirements 3, 4, and 8.
- Comprehensive audit logging. Every configuration change, job execution, and credential read is captured in an immutable log that satisfies Requirement 10.
A practical example demonstrates this approach: a global payment processor adopted Flex to keep EU card data inside regional VPCs while coordinating pipelines from a U.S. operations center. The company maintained the same 600+ connectors, RBAC model, and deployment automation across regions, proving that geographic sovereignty and compliance controls work together without feature compromises.
What's the Path Forward for PCI DSS Compliance in Hybrid Architectures?
Version 4.0.1 finally accepts that you won't park every workload in one place. By sharpening shared-responsibility notes and endorsing phishing-resistant authentication, the standard lets you run hybrid or multi-cloud stacks without diluting security.
Your enterprise strategy centers on three components: segment workloads between control and data planes, keep card data processing within isolated customer-controlled environments, and automate immutable audit logging across all integration points. Architectures like Airbyte Enterprise Flex demonstrate that compliance and innovation work together. You get modern data capabilities without compromising security standards.
Airbyte Flex delivers PCI DSS-compliant hybrid architecture, keeping card data in your VPC while enabling AI-ready data pipelines with complete sovereignty. Talk to Sales to discuss your payment processing compliance requirements and see how hybrid deployment solves cross-border data residency challenges.
Frequently Asked Questions
How does PCI DSS v4.0.1 differ from previous versions for hybrid environments?
Version 4.0.1 clarifies responsibilities for hybrid architectures without adding new controls. The update sharpens network segmentation language, accepts phishing-resistant authentication, and provides clearer guidance on keyed hashing for PAN protection. These changes help teams demonstrate compliance across cloud and on-premises systems with less ambiguity about who owns which controls.
Can tokenization completely remove systems from PCI DSS scope?
Tokenization significantly reduces scope by replacing PANs with surrogate values, but it doesn't eliminate all compliance requirements. Systems that generate, transmit, or store tokens still need security controls. The tokenization service itself remains in scope, and you must prove that detokenization only happens in controlled environments. This approach shrinks your audit perimeter but doesn't eliminate it entirely.
What's the difference between control plane and data plane in PCI DSS compliance?
The control plane manages orchestration, scheduling, and metadata without touching actual cardholder data. The data plane processes the PANs themselves, performing extract, transform, and load operations. This separation keeps sensitive data within your controlled environment while allowing cloud-based management. Auditors appreciate this clear boundary because it limits scope and makes responsibility mapping straightforward.
How often must enterprises recertify PCI DSS compliance?
Enterprises must validate PCI DSS compliance annually through a Qualified Security Assessor (QSA) or Self-Assessment Questionnaire (SAQ), depending on transaction volume and processing model. Beyond annual validation, you need continuous monitoring and quarterly network scans. Any significant infrastructure changes may trigger reassessment, so teams building hybrid pipelines should document architecture decisions and maintain audit trails throughout the year.

.webp)
